How to Schedule Azure VM Deployment – Step-by-Step Guide
How to schedule the deployment of Azure VMs
Automate Azure VM Deployment
If you need to schedule the regular deployment of your Azure VMs, you can do this easily with one of our Azure tools, AVMD (Azure VM Deployer). With the Azure VM deployer you can deploy single and multiple Virtual Machines quickly, easily and repeatably.
AVMD is completely FREE, you can download it from here and start using it right away.
Hopefully you have AVMD all setup and an azure admin account with the appropriate permissions to your Azure tenant to start the scheduled deployment of your Azure VMs.
Azure VM Deployment Use Cases
| Use Case | Description |
|---|---|
Dev/Test Environments |
Scheduling Azure VM deployment for development and testing environments allows for efficient use of resources by creating and deleting VMs as needed. For example, a development team might schedule VM deployment during business hours and delete them at the end of the day to avoid wasting resources. |
Batch Processing |
Scheduling Azure VM deployment for batch processing can help optimize resource utilization by only creating VMs when needed. This can be particularly useful for applications that require large amounts of compute resources for short periods of time, such as data analysis or video encoding. |
Disaster Recovery |
Scheduling Azure VM deployment for disaster recovery can help ensure that backup VMs are always available and up-to-date. This can be critical in the event of a system failure or other outage. |
Scheduled Maintenance |
Scheduling Azure VM deployment for scheduled maintenance can help minimize the impact of maintenance on users by automatically redirecting traffic to other VMs while maintenance is performed. |
High Availability |
Scheduling Azure VM deployment for high availability can help ensure that VMs are always available to users. This can be achieved by automatically creating new VMs when existing ones fail or become unavailable. |
Cost Optimization |
Scheduling Azure VM deployment can help optimize costs by only creating VMs when they are needed, and deleting them when they are no longer needed. This can be particularly useful for organizations that have variable workloads or need to closely manage their cloud spend. |
Launch the Azure VM Deployer
To start automating and scheduling deployment of your Azure VMS, simply open up Azure VM Deployer and let is synchronise with your Azure environment.
Scan your Azure Tenancy First
First, ensure that you have the AVMD tool downloaded and set up on your machine. You’ll also need an Azure admin account with the necessary permissions to your Azure tenant to deploy VMs. Once you’re ready to begin, launch the Azure VM Deployer and allow it to synchronize with your Azure environment.
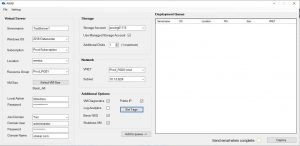
Azure VM Deployment Settings
- You can now start filling out all the settings to deploy your VMs to your Azure subscription.
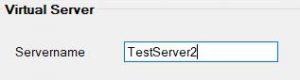
Provide a Name for your Virtual Server
Choose the Servers Operating System
Azure Subscription
Azure Availability Zone Location
Azure Resource Group
Choose the Azure Virtual Machine size
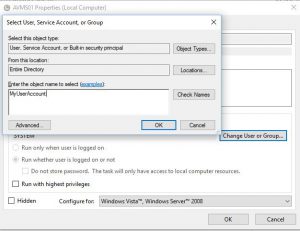
Provide a local Administrator account and password
Join the VM automatically a domain (You will need an account with Domain Join Permissions)
Which Azure Storage account you wish to deploy the VM to
Any additional disks you want to add to the VM during deployment
The Azure vNet and Subnet
Further additional options if you want VM diagnostics, Azure Log Analytics, a Basic NSG, Public IP, Azure Resource Tags and finally if you want to shutdown the VM post deployment.Click Add to queue when you have filled out all the Azure VM details and it will populate these settings to the Deployment Queue.
Provide a name for your Azure VM
For any additional VMs, keep filling out the details and add them to the queue too. If the servers are all the same type and settings you just need to update the server name before adding them to the deployment queue.
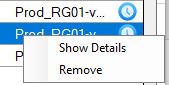
Azure VM Details
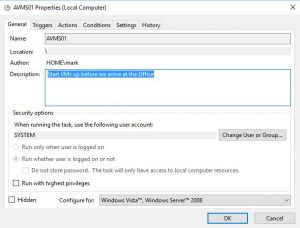
Now when you have added all the Virtual Machines you wish to deploy to Azure you are now ready to start deployment, but you may want to just confirm that your VM settings are correct. Simply right click the blue icon next to each Virtual Machine in the Deployment Queue and choose Show Details
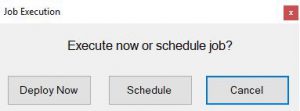
Azure VM Deployment Schedule Creation
Now lets start the deployment of your Azure Virtual Machines. Click the DEPLOY button in the bottom left hand corner and you are now presented with the options to deploy right now or schedule the VM deployment of your Azure VMs.
Azure VM New Deployment Schedule
In this example we will schedule the deployment of the Azure VMs, so click on schedule, then on OK to start the schedule creation.
Azure VM New Deployment Schedule
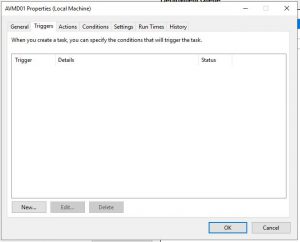
We are now prompted to create the schedule to deploy your Azure Virtual Machines, click on New.
Scheduled Deployment Execution
In this example we will schedule the deployment of the Azure VMs, so click on schedule, then on OK to start the schedule creation.
Schedule Creation
We are now prompted to create the schedule to deploy your Azure Virtual Machines, click on New.
Schedule Settings
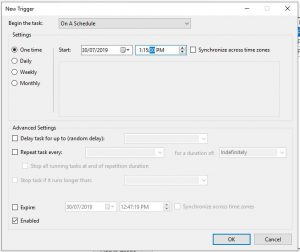
Simply put in the date and time you wish for your Azure VMs to deploy at then click OK. (You can set to schedule this once off, or a reoccurring daily, weekly or monthly schedule.)
Schedule Date and Time Settings
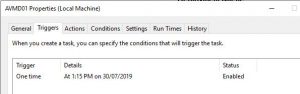
Confirm that the date and time you want to schedule the VMs for deployment to your Azure subscription is correct.
Confirm the Schedule is Correct
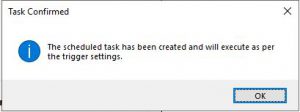
Click on OK in the scheduler window and the deployment task is now confirmed.
Scheduled Deployment is underway
My scheduled deployment has now kicked off and we can see in my Azure Portal that the machines are now deploying.
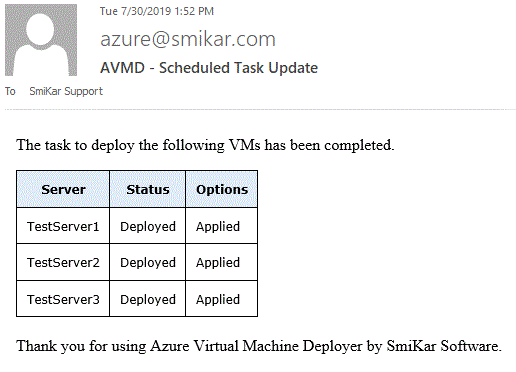
Scheduled Deployment Alerting
If you had set up your email alerts, you will receive an email letting you know that your VMs have now deployed to Azure.
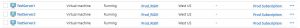
- After some time your Azure Virtual Machines should have now deployed. As seen in the Azure Portal I can see that our Azure VMs are up and running, in the correct resource group, Azure Subscription and Azure Location.
Dont forget that the Azure VM Deployer is completely free and one of our Azure Management Tools.
Azure VMs are now deployed
After some time your Azure Virtual Machines should have now deployed. As seen in the Azure Portal I can see that our Azure VMs are up and running, in the correct resource group, Azure Subscription and Azure Location.
Dont forget that the Azure VM Deployer is completely free and one of our Azure Management Tools.
Azure FAQs
| Question | Answer |
|---|---|
What is Azure VM deployment? |
Azure VM deployment is the process of creating and managing virtual machines in the Microsoft Azure cloud platform. |
What are the benefits of using Azure VMs? |
Azure VMs offer a wide range of benefits, including scalability, flexibility, security, and cost-effectiveness. |
How do I create a new Azure VM? |
You can create a new Azure VM through the Azure portal, Azure CLI, or Azure PowerShell. |
What operating systems are supported on Azure VMs? |
Azure VMs support a wide range of operating systems, including Windows Server, Linux, and various distributions of Unix. |
What are the different VM sizes available in Azure? |
Azure offers a variety of VM sizes, ranging from small, low-cost instances to large, high-performance instances. |
How can I manage and monitor my Azure VMs? |
You can manage and monitor your Azure VMs through the Azure portal, Azure CLI, or Azure PowerShell, as well as third-party tools such as Azure Monitor and Azure Log Analytics. |
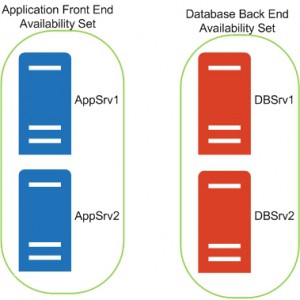
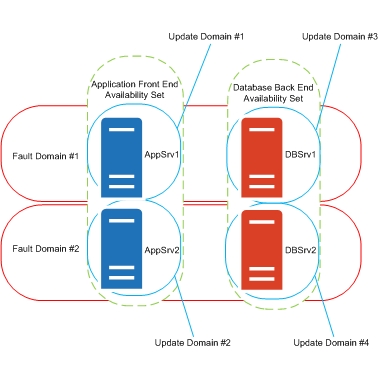
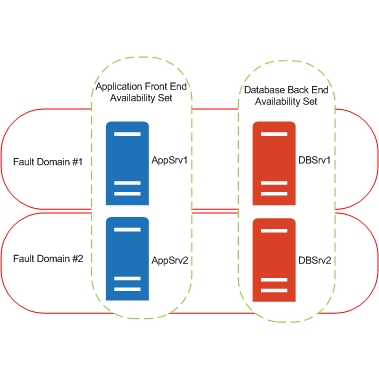
What are availability sets in Azure VM deployment? |
Availability sets are used to ensure high availability for VMs by distributing them across multiple physical servers in a data center. |
How can I secure my Azure VMs? |
You can secure your Azure VMs through a variety of measures, including network security groups, firewall rules, and encryption. |
What is Azure Site Recovery and how does it work with VMs? |
Azure Site Recovery is a disaster recovery solution that can be used to replicate and recover VMs in the event of a site outage or other disaster. |
How can I optimize the performance of my Azure VMs? |
You can optimize the performance of your Azure VMs through various means, such as selecting the appropriate VM size, optimizing disk performance, and using caching. |