Update SCCM to Version 1906 – Easy Update Instructions
Step by Step guide on how to update to SCCM 1906
Hi all, Microsoft has just recently released their latest iteration to SCCM, version 1906. With this update of SCCM comes quite a few welcome features and to find out more go to this link on the Microsoft site.
But you are here to see how easy it is to upgrade your SCCM to the current branche 1906.
So let’s get started on the upgrade process for SCCM 1906.
- As always when performing any upgrades, make sure that you have a good known valid backup or snapshot of the servers you are targeting. Once you have confirmed you have both or either of these in place, open your SCCM console with your SCCM administration account.
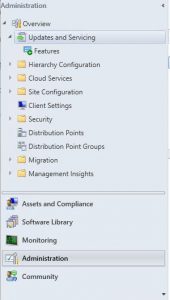
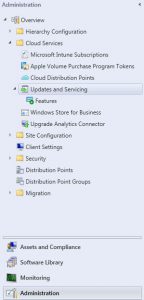
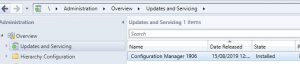
- Now click on Administration then highlight Updates and Servicing.
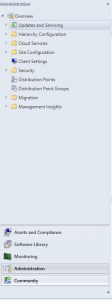
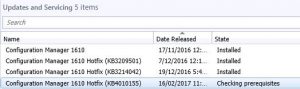
- Now in the main Window you should hopefully see the SCCM 1906 update is Ready to Install. If not, click on Check for Updates and allow for sometime for SCCM to download the latest branch update from the Microsoft site. Remember to refresh your window as it wont show up automatically.
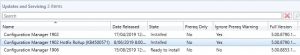
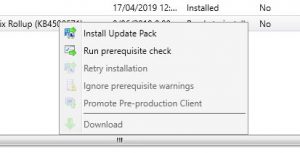
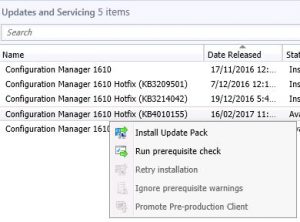
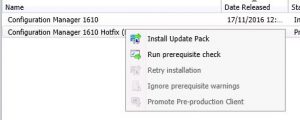
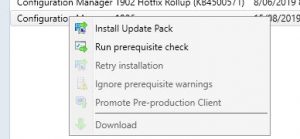
- As you can see from the prior picture, our environment has the SCCM 1906 update all ready to install and that our previous SCCM 1902 updates had been installed. First thing we need to do is to Run prerequisite check. Highlight the Configuration Manager 1906 update, right click and choose Run prerequisite check.
- This check will take a little time, you can see the status of the check by refreshing the window.

You can also select Monitoring in the SCCM console Window, navigate to Updates and Servicing, highlight the Configuration Manager 1906 update, right click that and choose show status for a more detailed display of the status of the prerequisite check of SCCM 1906.
(now this may take sometime to allow the 1906 upgrade to confirm that your SCCM environment is ready for the install, so always be patient)
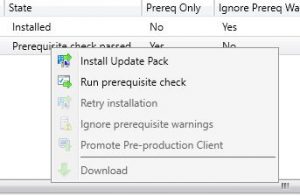
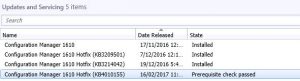
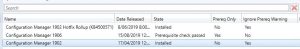
- OK, hopefully your SCCM environment passed all the checks to confirm it is ready for the SCCM 1906 installation. Now go back to the Administration and you should see that the Prerequisite Check Passed for the Configuration Manager 1906 update as below.
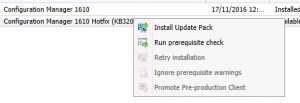
- Now to the gritty stuff, we are ready to start the upgrade process for SCCM 1906. Again, highlight the Configuration Manager 1906 update, right click and choose Install Update Pack.
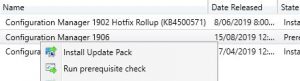
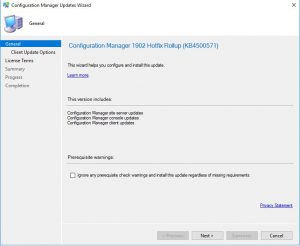
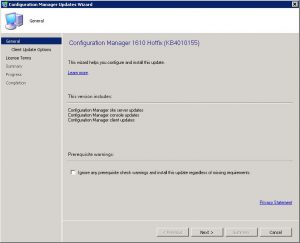
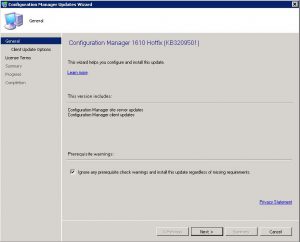
- You are now presented with the Configuration Manager Updates Wizard. Click on Next when you are ready to start the installation, this will take around 30 – 45 minutes to complete so make sure you have a big enough change window for the update process.
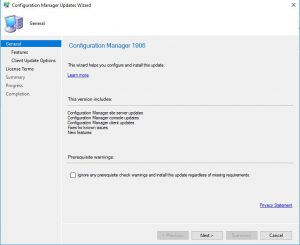
- On the second windows of the SCCM updates wizard, carefully choose any options / features that you require and then click on Next.
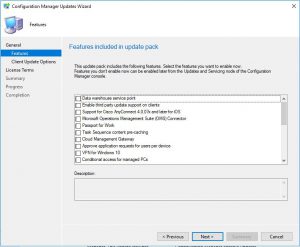
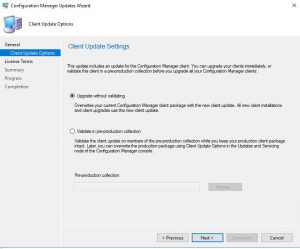
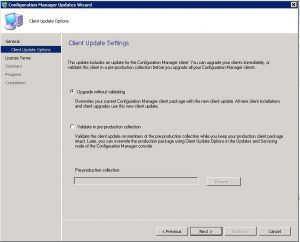
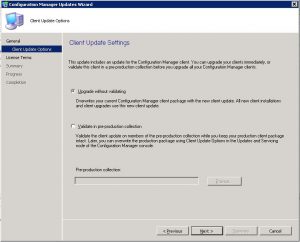
- Client Update Settings window allows you to choose if you would like to validate the client update on members of a Pre-Production collection so that you can test there are no issues with the update. As this is one of SmiKar’s software test environments, I am going to just Upgrade without Validating. When you are ready to proceed click on Next.
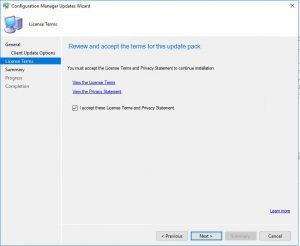
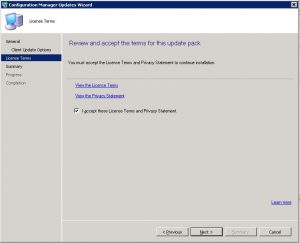
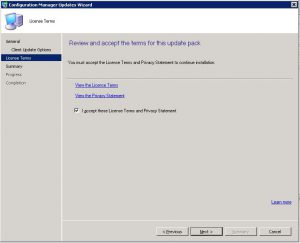
- We are almost ready to start the installation and upgrade to SCCM 1906. On the License Terms window, you can read the License Terms if you wish to do so, click on Next when you are ready for the next step.
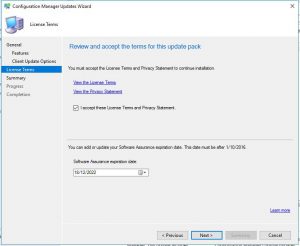
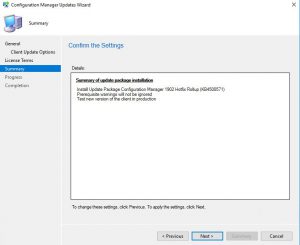
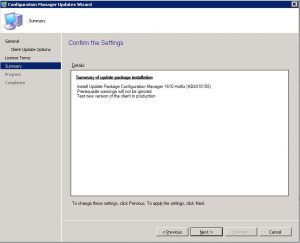
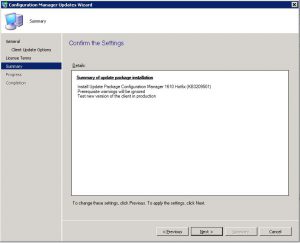
- Now the last step before the upgrade process starts off. On the Configuration Manager Updates Wizard Summary Window, check the settings and details you want have been selected and then finally click on Next. This will start the upgrade to SCCM 1906 so make sure you want to do this.
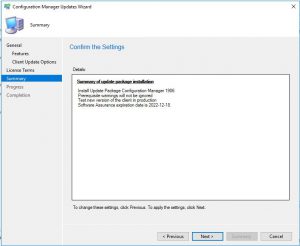
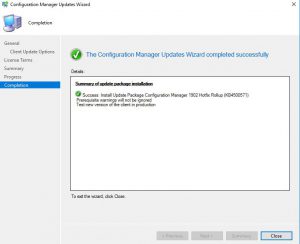
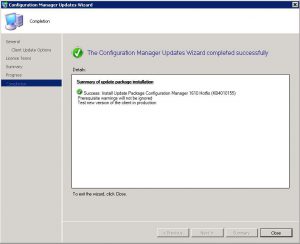
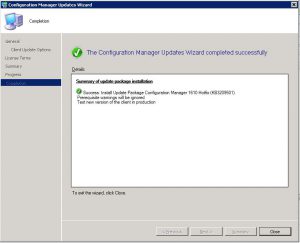
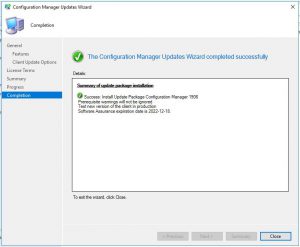
- The last window you can now close and the SCCM 1906 update will complete in the background.
- Now what if you dont want to refresh the SCCM console window and wish to see more details about what is happening with the update to SCCM 1906. Well you can easily get a more detailed view of the upgrade process by going to the local C Drive of your SCCM server and opening the ConfigMgrSetup.log file. If you have Trace32 installed to read your log files, it will display this in a nice and easy to read fashion.
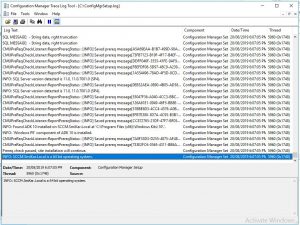
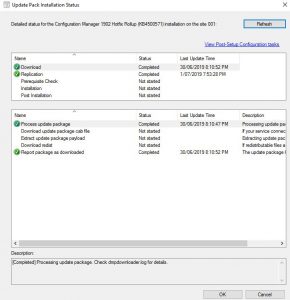
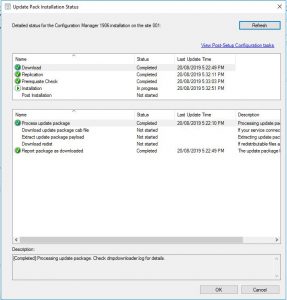
- Alternatively to see the update, in your SCCM Console go to Monitoring then Updates and Servicing Status, highlight the Configuration Manage 1906 update, right click and choose Show Status. In the Update Pack Installation Status window, highlight Installation and you can also see the what the SCCM 1906 update is doing.
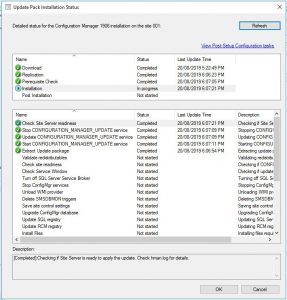
- Hopefully after some time (it took around 30 minutes to complete the upgrade to SCCM 1906 in our test environment), everything should have installed and updated your SCCM to the latest branche. You may get a warning that your Configuration Manager console needs to be updated as well.
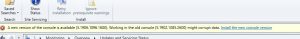
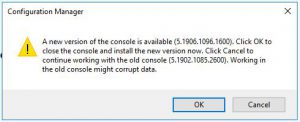
- Close the console then reopen to update. (the SCCM 1906 update took a few minutes to complete in the lab)
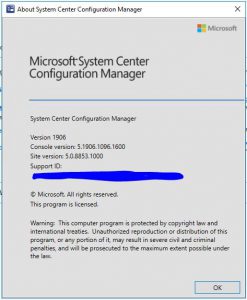
- Finally after quite a few easy steps, we can confirm that the SCCM environment successfully installed to the current branche, SCCM 1906.
Now that you have updated your SCCM to version 1906, perhaps you use SCCM to patch your virtual server environment. While you are here, check out SnaPatch and see how it allows you to have an easy roll back position should any issues with your patch deployment occurs.