Cloud Reverse Migration: A Comprehensive Guide
The rapid technological advancements in the last decade led to a massive migration of data and applications from on-premise environments to the cloud. While this cloud migration trend dominated the IT world, a recent paradigm shift has emerged that’s moving in the opposite direction – ‘Cloud Reverse Migration’ or ‘Cloud Repatriation’. This burgeoning movement towards cloud repatriation has piqued the interest of many, prompting a need for a comprehensive exploration of this concept, its driving factors, and the tools that facilitate it.
Understanding Cloud Reverse Migration
Cloud Reverse Migration, also known as Cloud Repatriation, is the strategic move of transferring digital data, operations, applications, or services from a cloud environment back to its original on-premise location or to an alternate private data center. Contrary to some misconceptions, this migration process does not denote the failure of cloud computing; instead, it is a strategic response to the evolving needs of businesses and a reflection of the realization that not all workloads are suited for the cloud.
The Rising Trend of Cloud Repatriation
While the benefits of cloud computing – flexibility, scalability, and cost savings, to name a few – remain valid and significant, an increasing number of businesses are reconsidering their digital strategies and migrating their operations back on-premises. This trend, known as Cloud Repatriation, is becoming increasingly prevalent across different sectors for a multitude of reasons.
Reasons for Cloud Reverse Migration
Financial Considerations
At first glance, cloud services may appear to be a more cost-efficient alternative due to the reduced upfront costs and the promise of predictable recurring expenses. However, the reality is often more complicated. The ongoing costs of cloud services, which include data transfer fees and charges for additional services, can accumulate rapidly, turning what initially seemed like a cost-saving move into a financial burden. For some businesses, investing in and maintaining in-house infrastructure can be more cost-effective over the long term.
Data Security and Control
With data breaches and cyberattacks becoming more sophisticated and commonplace, organizations are increasingly concerned about their data’s security. While cloud service providers have robust security measures in place, storing sensitive data off-premises often results in companies feeling they have less control over their data protection strategies. By migrating data back on-premise, organizations can regain control and implement security measures tailored to their unique requirements.
Performance and Latency Issues
Despite the cloud’s advantages, certain applications, particularly those requiring real-time data processing and low latency, can face performance issues in a cloud environment. Factors such as network congestion, physical distance from the data center, and shared resources can result in slower response times. As such, for applications where speed is paramount, on-premises solutions often prove superior.
Compliance and Regulatory Concerns
Certain industries, such as healthcare and finance, are subject to strict data management regulations. These industries often need to keep their data on-premises to comply with data sovereignty laws and privacy regulations. In such cases, cloud reverse migration becomes a necessary step towards ensuring compliance and avoiding hefty penalties.
Carbon: Your Reliable Partner for Cloud Reverse Migration
When it comes to facilitating the cloud repatriation process, the right tools can make a world of difference. Carbon, a software tool developed by SmiKar, is specifically designed to streamline the process of migrating Azure Virtual Machines (VMs) back to an on-premise environment, either on VMware or Hyper-V. With its user-friendly interface and impressive features, Carbon simplifies what could otherwise be a complex process.
Comprehensive VM Management
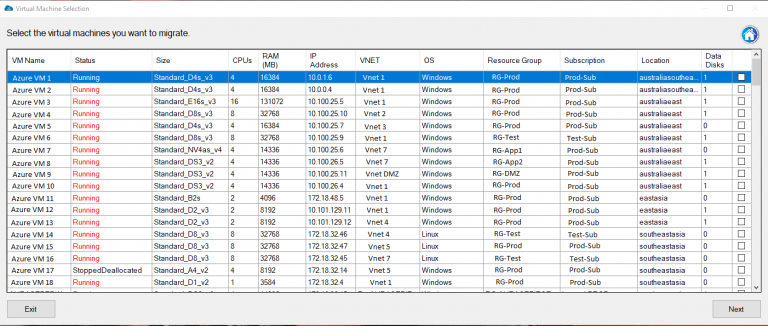
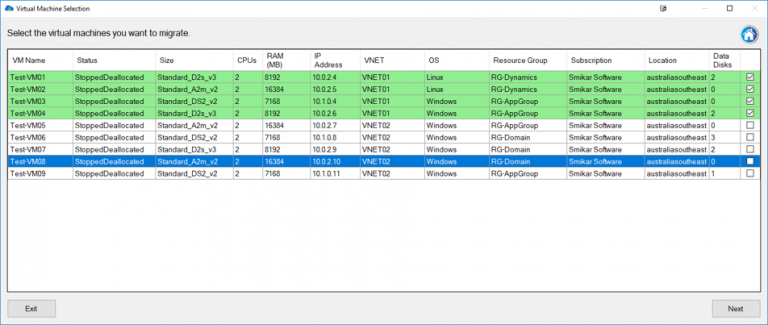
Carbon’s comprehensive VM management is one of its key features. With Carbon, users gain a detailed understanding of their Azure VMs – including VM name, status, size, number of CPUs, memory allocation, IP address, VNET, operating system, resource group, subscription name, location, and more. This detailed information aids users in making informed decisions about which VMs to migrate and how best to configure them in their on-premise environment.
Easy Migration and Conversion Process
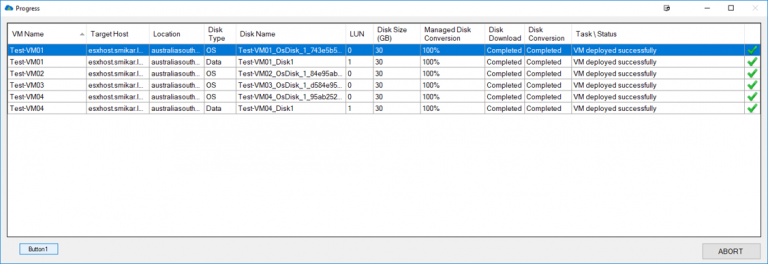
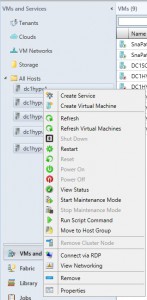
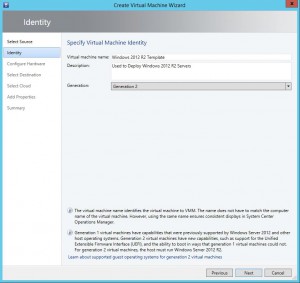
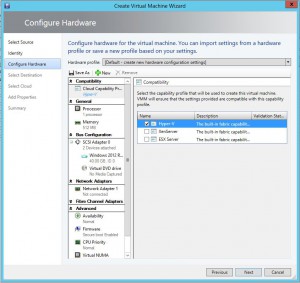
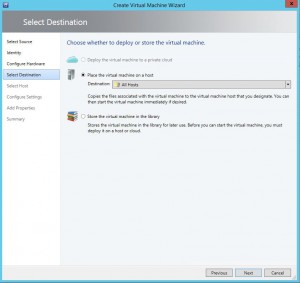
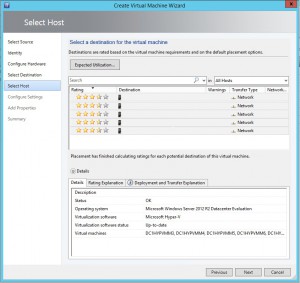
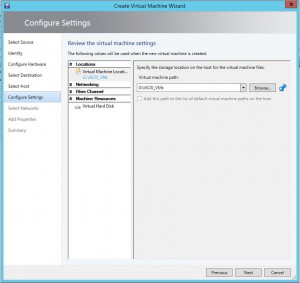
One of Carbon’s greatest strengths is its ability to simplify the migration and conversion process. By integrating seamlessly with VMware or Hyper-V environments, Carbon enables users to replicate and convert their Azure VMs to their chosen on-premise hypervisor with just a few clicks. The software sets up replicated Azure VMs with the same CPU, memory, and disk configurations, ensuring a smooth transition back to the on-premise environment.
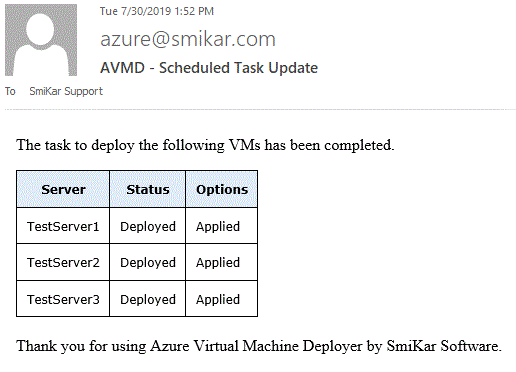
Automatic Configuration and Email Notifications
To help users stay informed about the progress of their migration, Carbon offers automatic configuration and email notifications. These notifications can alert users to any changes in their VMs’ status, allowing them to monitor the migration process more effectively.
Customizable User Interface
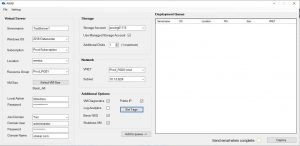
Recognizing that each user has unique preferences, Carbon provides a customizable interface that allows users to adjust settings to suit their needs. Whether users prefer a particular hypervisor, datastore, or Azure subscription, Carbon offers the flexibility to accommodate these preferences, making the migration process as straightforward and user-friendly as possible.
How Carbon Streamlines Cloud Reverse Migration
Carbon’s streamlined process for migrating Azure VMs back to on-premise infrastructure has brought ease and simplicity to a typically complex task. By providing detailed VM information, an easy-to-navigate migration process, automatic configuration, and email notifications, along with a customizable interface, Carbon enables businesses to execute a smooth and successful cloud reverse migration.
Conclusion
Cloud reverse migration is a growing trend among businesses seeking to address cloud computing’s limitations. Whether driven by financial considerations, data security and control concerns, performance issues, or regulatory compliance, the move towards cloud repatriation has become an increasingly viable option for many organizations. With tools like SmiKar’s Carbon, this process is made significantly more manageable, providing businesses with a path to successfully navigate their journey back to on-premise infrastructure.
Reverse Cloud Migration FAQs
| Number | Question | Answer |
|---|---|---|
| 1 | What is Cloud Reverse Migration? | Cloud Reverse Migration, also known as Cloud Repatriation, is the process of moving data, operations, applications, or services from a cloud environment back to its original on-premise location or to a private data center. |
| 2 | Why are businesses opting for Cloud Repatriation? | Businesses are opting for Cloud Repatriation for several reasons. These can include financial considerations, data security and control, performance and latency issues, and regulatory compliance concerns. |
| 3 | What are some common issues businesses face with cloud-based solutions? | Common issues include unexpected costs, lack of control over data security, performance issues especially with applications that require real-time data processing and low latency, and compliance issues in industries with strict data regulations. |
| 4 | How can Cloud Reverse Migration address these issues? | Cloud Reverse Migration allows businesses to regain control over their data, potentially reduce costs, improve application performance, and ensure compliance with industry regulations. |
| 5 | What is Carbon and how does it support Cloud Reverse Migration? | Carbon is a reverse cloud migration tool. It streamlines the process of migrating Azure Virtual Machines (VMs) back to an on-premise environment, either on VMware or Hyper-V. It offers comprehensive VM management, easy migration and conversion, automatic configuration and email notifications, and a customizable user interface. |
| 6 | What are the key features of Carbon for cloud reverse migration? | Key features of Carbon include comprehensive VM management, simplified migration and conversion process, automatic configuration and email notifications, and a customizable user interface to adjust settings to user preferences. |
| 7 | How does Carbon ease the process of cloud reverse migration? | Carbon eases the process of cloud reverse migration by offering a detailed view of Azure VMs, enabling seamless migration and conversion, providing automatic notifications about the migration process, and allowing users to customize the software to their preferences. |
| 8 | What types of businesses can benefit from using Carbon for Cloud Reverse Migration? | Businesses of all sizes and across various sectors can benefit from Carbon, especially those looking to move their Azure VMs back to on-premise environments due to financial, security, performance, or compliance reasons. |
| 9 | How does Carbon ensure a seamless transition from the cloud to on-premise environments? | Carbon ensures a seamless transition by integrating with your on-premise VMware or Hyper-V environments. It replicates and converts Azure VMs to the chosen on-premise hypervisor, maintaining the same CPU, memory, and disk configurations. |
| 10 | Can Carbon assist in managing costs during Cloud Reverse Migration? | By providing comprehensive details about Azure VMs and offering a simplified migration process, Carbon can help businesses make informed decisions, potentially helping to manage costs associated with Cloud Reverse Migration. |