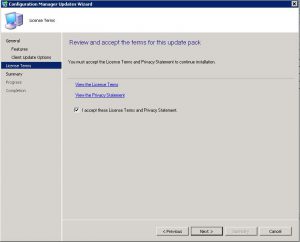
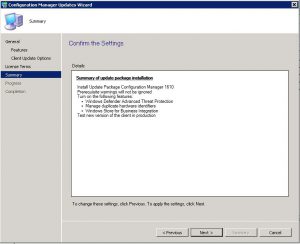
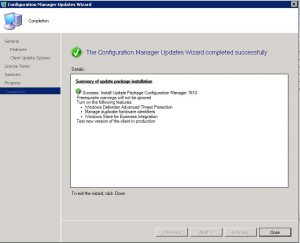
Snapshot before Patching
Automate Snapshot Creation Before Deployment
Reduce Patching Risks with SnaPatch
System administrators are responsible for ensuring the smooth functioning of their organization’s computer systems. They are the ones who deploy new software and updates, perform maintenance tasks, and troubleshoot any issues that arise. However, keeping these systems up-to-date can be a daunting task, especially when new updates and patches are released frequently. This is where taking a snapshot before patching comes into play.
A snapshot before patching is a crucial tool that system administrators can use to protect their systems from vulnerabilities. In this article, we will discuss why taking a snapshot before patching is essential and how it can help system administrators safeguard their systems.
What is a Snapshot Before Patching?
A snapshot before patching is a backup copy of your system’s current state. This copy can be used to restore your system to its previous state in case something goes wrong during the patching process. Taking a snapshot before patching ensures that you have a stable and reliable system to fall back on if the patching process fails.
Why is a Snapshot Before Patching Important?
Taking a snapshot before patching is essential for several reasons. Here are some of the main reasons why system administrators should make this a standard practice:
- Protects Against System Failure: Patching can sometimes cause system failures. Having a snapshot before patching ensures that you can quickly restore your system to its previous state in case of such failures.
- Provides a Safe Environment for Testing: Taking a snapshot before patching allows system administrators to test the patches in a safe environment. This ensures that any issues that arise during the testing process can be addressed before the patches are applied to the live system.
- Helps in Disaster Recovery: Snapshots can be used as part of a disaster recovery plan. In case of a disaster, snapshots can be used to restore your system to a previous state.
Best Practices for Using Snapshots Before Patching
Here are some best practices for using snapshots before patching:
Always Test Patches:
Test patches in a safe environment before applying them to the live system.
Schedule Regular Snapshots:
Schedule regular snapshots so that you always have an up-to-date backup of your system.
Name Your Snapshots:
Give your snapshots meaningful names so that you can easily identify them.
Store Snapshots Securely:
Store your snapshots in a secure location to prevent unauthorized access.
Snapshots Before Patching FAQs
What is the difference between a snapshot and a backup?
A snapshot is a point-in-time copy of your system, whereas a backup is a copy of your system’s data that is stored separately.
How often should I take a snapshot before patching?
It depends on your organization’s needs. However, it is a good practice to take a snapshot before each patching session.
Can I take a snapshot of a virtual machine?
Yes, you can take a snapshot of a virtual machine. In fact, taking snapshots of virtual machines is a common practice in virtualized environments.
What happens if I don’t take a snapshot before patching?
If you don’t take a snapshot before patching, you run the risk of losing important data or causing system failures.
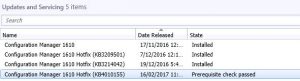
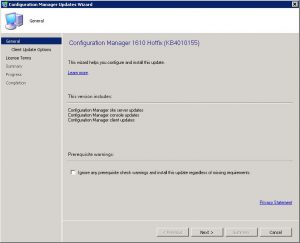
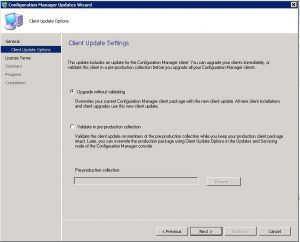
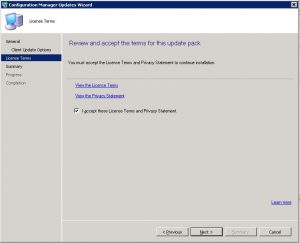
How to Snapshot before deploying Patches.
How SnaPatch Can Help You Take Snapshots Before Patching
When it comes to taking snapshots before patching, it can be a time-consuming and manual process for system administrators. However, there is a tool that can simplify the process and make it more efficient: SnaPatch.
What is SnaPatch?
SnaPatch is a software application that interacts with your Microsoft System Centre Configuration Manager (SCCM) environment to pull in all your machine information. It uses SCCM as the source of truth for all your VM information.
Next, it interfaces with either your vCentre or System Centre Virtual Machine Manager (SCVMM), or both. It takes control of your VM environment, allowing it to create and delete snapshots of your VMs.
How does SnaPatch work?
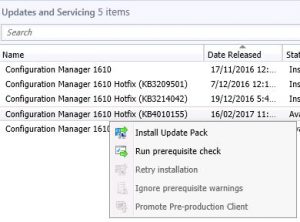
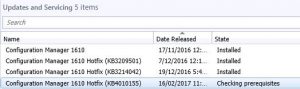
SnaPatch simplifies the snapshot process by automating it. It creates a snapshot of any virtual machine before allowing it to be patched. If the snapshot fails, the VM will not receive updates and will be removed from the patching schedule. SnaPatch streamlines the process and frees up your time by automating the snapshot and patching processes, while keeping you updated on progress via email notifications.
How do you deploy SnaPatch?
Deploying SnaPatch is easy and straightforward. After installation, the application discovers your SCCM environment and allows you to configure various settings such as email notifications, snapshot creation, and patch deployment.
Why use SnaPatch?
SnaPatch helps you take snapshots before patching in a more efficient and streamlined manner. It complies with SOX regulations and minimizes risk, and its automated snapshot creation feature ensures that you can easily roll back updates if necessary, giving you peace of mind and more time to focus on other critical tasks.
Conclusion
In conclusion, taking snapshots before patching is a critical step in ensuring the security and stability of your systems. SnaPatch can help simplify and automate this process, allowing you to deploy Microsoft updates in your VM environment safely and efficiently. Try SnaPatch today and streamline your patching process!