SCCM Clients re-evaluate software updates
SCCM – Change the time for a client to re-evaluate software updates

System Center Configuration Manager (SCCM) is an essential tool for managing and deploying software updates in an organization. SCCM provides a robust platform to manage software updates for desktops, servers, and mobile devices. However, SCCM clients can be configured to re-evaluate software updates based on specific criteria such as time, detection method, or client settings. In this article, we will discuss how to change the time for a client to re-evaluate software updates in SCCM.
What is SCCM, and Why is it Important?
SCCM is a system management software developed by Microsoft. It is used to manage large-scale deployments of operating systems, applications, and updates across an organization’s network. SCCM can manage various devices such as desktops, laptops, servers, and mobile devices. SCCM is essential for organizations that need to manage software updates across a large number of devices.
How to Change the Time for a Client to Re-evaluate Software Updates in SCCM
Changing the re-evaluation time for software updates can help keep devices up to date with the latest security patches. By default, SCCM clients are configured to check for software updates every seven days. However, this time interval can be changed based on an organization’s requirements. The following steps can be followed to change the time for a client to re-evaluate software updates in SCCM:
Step 1: Open the SCCM Console
Launch the SCCM console on your computer. The SCCM console can be launched by clicking on the Start menu and searching for “Configuration Manager Console.”
Step 2: Navigate to the Client Settings
In the SCCM console, navigate to the “Administration” tab and click on “Client Settings” under the “Client Settings” section.
Step 3: Configure the Software Updates Client Settings
In the “Client Settings” window, click on “Software Updates” in the left-hand pane. In the right-hand pane, scroll down to the “Software update evaluation schedule” section.
Step 4: Set the Time for Re-evaluating Software Updates
In the “Software update evaluation schedule” section, click on “Custom schedule.” In the “Custom schedule” window, enter the number of days that you want SCCM clients to re-evaluate software updates. Click on “OK” to save the changes.
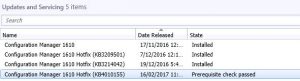
SCCM Client Software Update Evaluation FAQs
| FAQ | Answer |
|---|---|
How often does SCCM check for software updates? |
i. Default Time Interval for Checking Software Updates: The default time interval for SCCM to check for software updates is every 7 days. |
| ii. How to Configure the Time Interval for Checking Software Updates: To change the time interval for checking software updates in SCCM, go to “Administration” > “Client Settings” > “Default Client Settings” > “Software Updates.” Under the “Software Update Scan Schedule” section, select the desired interval from the drop-down list. Click “OK” to save the changes. | |
How do I force SCCM to check for software updates? |
i. Using SCCM Console to Force Software Update Check: To force SCCM to check for software updates using the console, navigate to “Assets and Compliance” > “Devices.” Select the devices that you want to check for updates, right-click and select “Client Notification” > “Check for Software Updates.” |
ii. Using PowerShell to Force Software Update Check: To force SCCM to check for software updates using PowerShell, open PowerShell as an administrator and run the following command: Invoke-CMSoftwareUpdateScan -DeviceName <DeviceName> -AllowUseDefaultCredentials -ForceScan. Replace <DeviceName> with the name of the device you want to check for updates. |
|
How do I know if my SCCM client is up to date? |
i. Checking the Last Scan Status of SCCM Client: To check the last scan status of an SCCM client, navigate to “Assets and Compliance” > “Devices.” Select the device that you want to check, and click on “Software Updates” > “Last Scan States.” This will display the last scan status of the device. |
| ii. Verifying the Installed Software Updates on SCCM Client: To verify the installed software updates on an SCCM client, navigate to “Assets and Compliance” > “Devices.” Select the device that you want to check, and click on “Software Updates” > “Compliance 1 – Overall Compliance.” This will display a list of installed and missing software updates on the device. |
SCCM is an essential tool for managing and deploying software updates in an organization. Changing the time for a client to re-evaluate software updates in SCCM can help keep devices up to date with the latest security patches. In this article, we discussed how to change the re-evaluation time for software updates in SCCM. We also answered some FAQs to make the process easy. By following the steps outlined in this article, you can ensure that your SCCM clients are up to date with the latest software updates.