SharePoint vs. OneDrive vs. Teams
Where Should You Store Your Files?
Microsoft 365 offers multiple file storage solutions—SharePoint, OneDrive, and Teams—each designed for different use cases. However, many organizations struggle to determine where to store files and how to manage document collaboration efficiently. Choosing the wrong storage location can lead to content sprawl, security risks, and version control issues.
In this guide, we’ll break down the key differences between SharePoint, OneDrive, and Teams, explore best practices, and help you decide the right place to store your files.
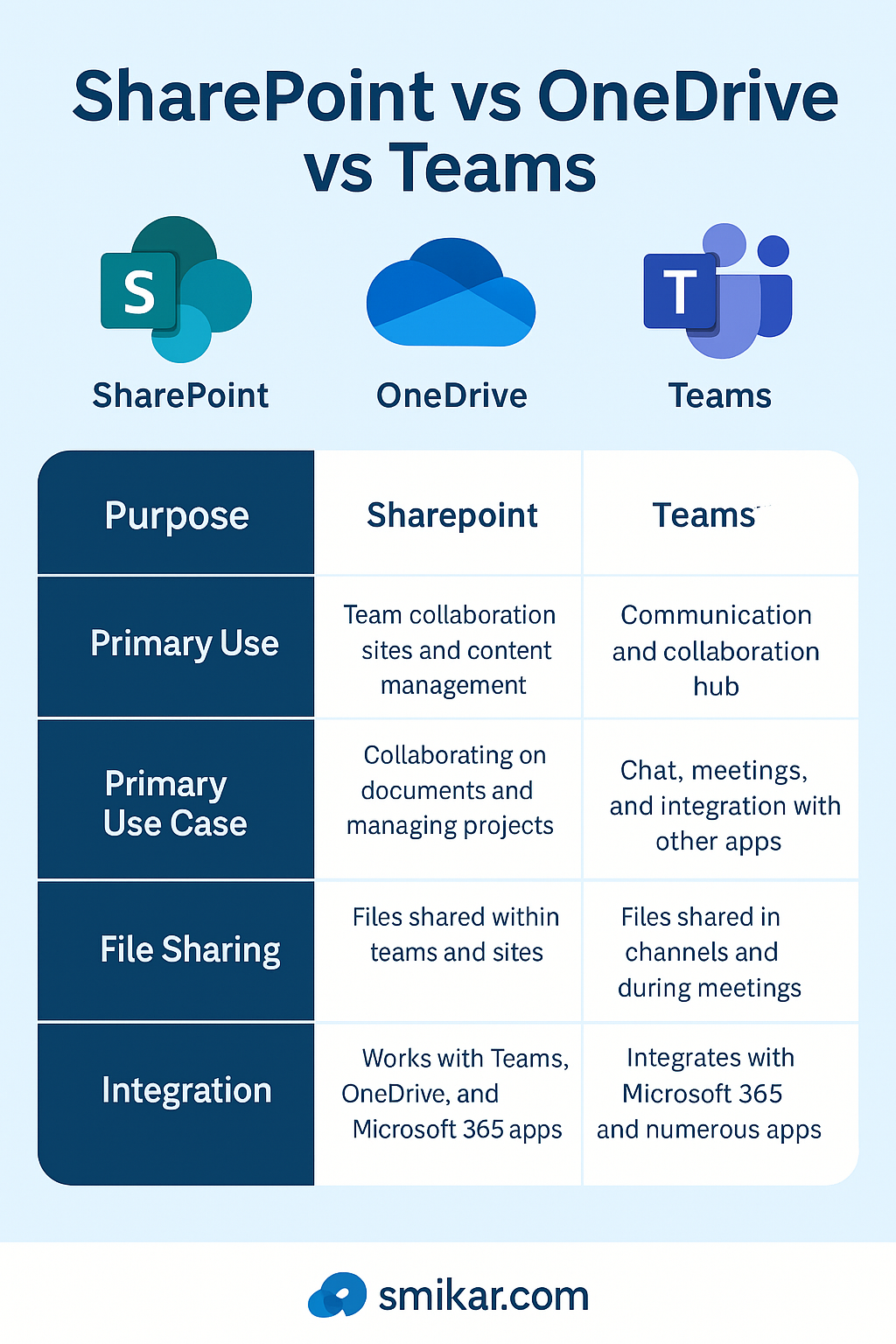
Key Takeaways: Quick Comparison
| Feature | OneDrive | SharePoint | Teams |
|---|---|---|---|
| Best for | Personal file storage | Team collaboration & document management | Real-time team collaboration |
| Default Permissions | Private (unless shared) | Managed at site/library level | Shared with team members |
| Version Control | Basic | Advanced (major/minor versions) | Advanced (via SharePoint) |
| Collaboration | Limited | Extensive (workflows, permissions, co-authoring) | Extensive (chat + file sharing) |
| Integration | Limited | Deep Microsoft 365 integration | Full Microsoft 365 integration |
Understanding the Purpose of Each Storage Solution
What is OneDrive?
OneDrive is personal cloud storage for Microsoft 365 users. It is designed primarily for individual use, allowing employees to store their own work files securely in the cloud. By default, files stored in OneDrive are private, but users can share them as needed.
Key Features of OneDrive:
-
Personal storage space – Each user gets their own OneDrive with ample storage.
-
Seamless synchronization – Access files across devices, including desktops, mobile devices, and the web.
-
File sharing options – Users can share files with colleagues via links or access controls.
-
Limited collaboration – While co-authoring is possible, OneDrive lacks the structured collaboration tools found in SharePoint and Teams.
-
Backup and security – Files are protected in Microsoft’s secure cloud and can be restored if deleted.
What is SharePoint?
SharePoint is a powerful team collaboration and document management platform that provides a structured way to store, manage, and share files across an organization. Unlike OneDrive, SharePoint is meant for teams and departments to work together on shared files with version control, metadata, and advanced permissions.
Key Features of SharePoint:
-
Team and department file storage – Centralized storage for teams, projects, and organizations.
-
Advanced permissions management – Assign read, edit, or full control access to different groups or individuals.
-
Version history and co-authoring – Track changes and allow multiple people to edit documents simultaneously.
-
Integration with Microsoft 365 – Works with Power Automate, Power Apps, and Microsoft Lists for workflow automation.
-
Customizable document libraries – Organize content efficiently with metadata, columns, and filters.
What is Microsoft Teams?
Microsoft Teams is a collaboration and communication hub that includes chat, meetings, calls, and file sharing. While Teams itself is not a storage platform, it integrates deeply with SharePoint and OneDrive.
Key Features of Microsoft Teams:
-
Real-time collaboration – Share files, edit documents, and discuss projects in a unified workspace.
-
Chat and meetings integration – Combine messaging and document collaboration for seamless teamwork.
-
Tightly integrated with SharePoint – Files uploaded to Teams are actually stored in SharePoint document libraries.
-
Channel-based organization – Create teams and channels to keep conversations and files structured.
-
Permissions inherited from Teams membership – Files shared in Teams are automatically available to team members.
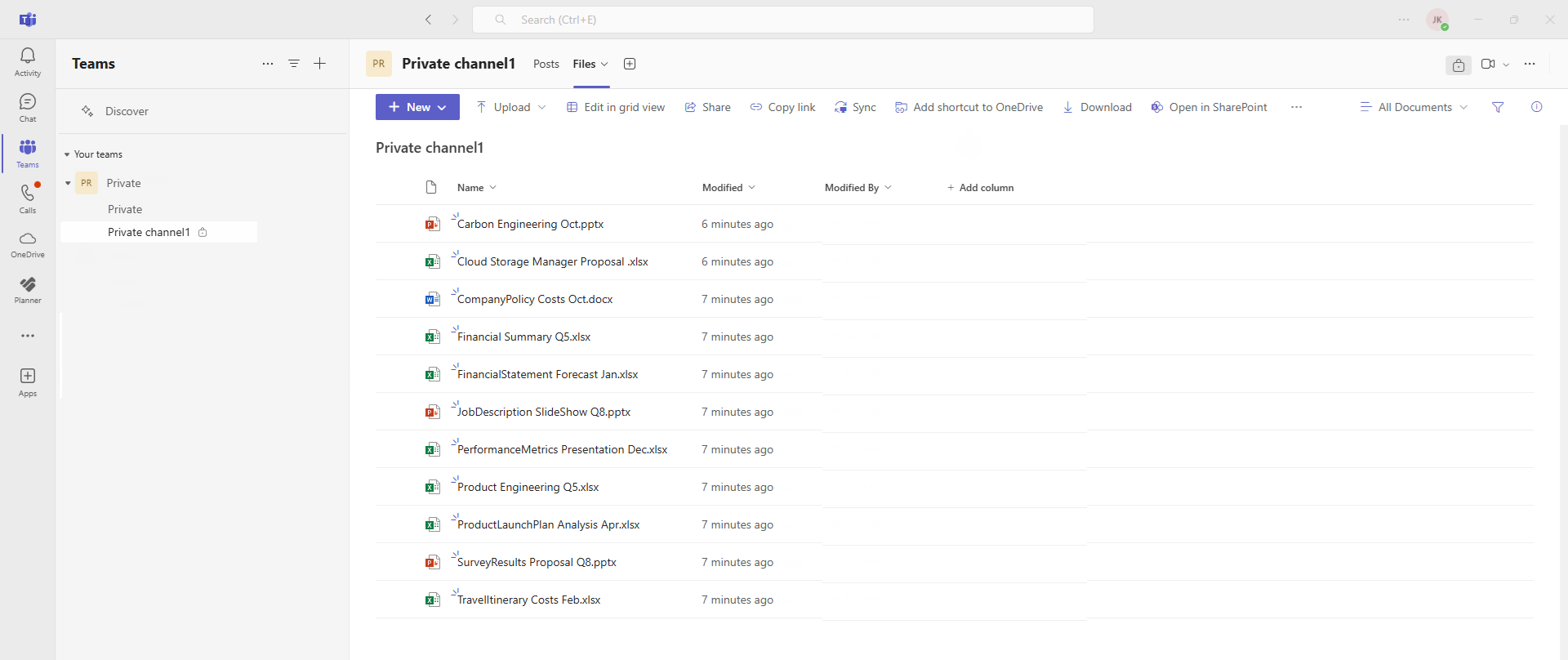
Common Scenarios: Where Should You Store Your Files?
💡 Scenario 1: You’re working on a draft document that only you need access to. ✅ Store it in OneDrive (it’s your personal cloud storage).
💡 Scenario 2: Your marketing team needs access to shared branding files. ✅ Store it in SharePoint (it’s an organization-wide resource).
💡 Scenario 3: Your project team needs to collaborate on files and discuss progress. ✅ Store them in Teams (it provides chat, meetings, and file collaboration).
💡 Scenario 4: You’re moving from a network drive and want a structured document repository. ✅ Use SharePoint (it allows folders, metadata tagging, and governance).
💡 Scenario 5: You need to share a quick file with a colleague. ✅ Use OneDrive (and send a direct sharing link).
Best Practices for File Storage in Microsoft 365
✔ Use OneDrive for personal and temporary files. ✔ Use SharePoint for team collaboration and document retention. ✔ Use Teams for project-based file sharing and discussions. ✔ Enable version control in SharePoint to track changes. ✔ Implement governance policies to prevent content sprawl. ✔ Archive old content to reduce SharePoint storage costs.
FAQs: Your Top Questions Answered
1️⃣ Can I move files between OneDrive, SharePoint, and Teams? Yes! Files can be moved or copied between OneDrive, SharePoint, and Teams using the “Move To” or “Copy To” options.
2️⃣ Is OneDrive private? Yes, OneDrive files are private by default, but they can be shared with others.
3️⃣ Can I use SharePoint as a file server replacement? Yes, SharePoint can replace traditional file servers with its cloud-based storage and document management features.
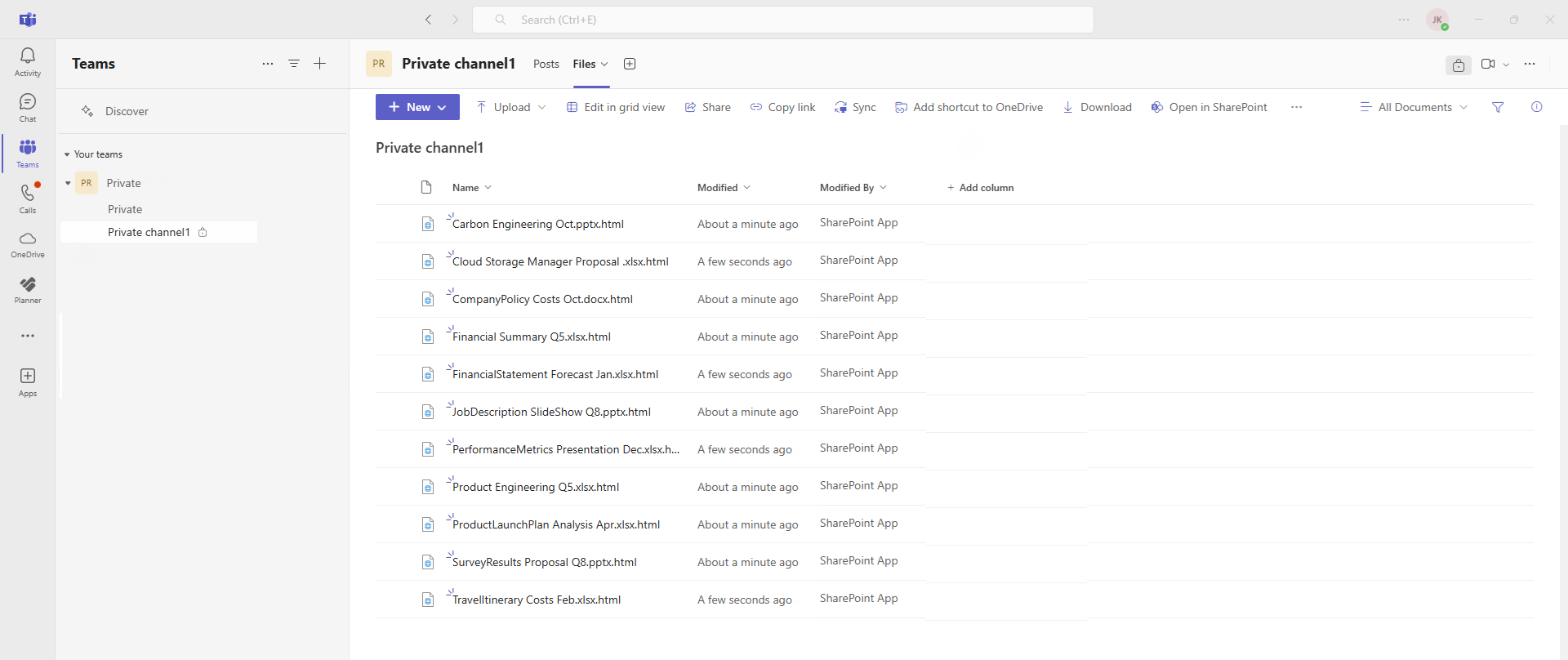
4️⃣ What happens if I delete a file in Teams? Files in Teams are stored in SharePoint. If deleted, they go to the SharePoint recycle bin and can be restored within 93 days.
5️⃣ How is Teams different from SharePoint? Teams is a collaboration hub with chat and meetings, while SharePoint is a structured document management system.
6️⃣ Can I access OneDrive files offline? Yes, OneDrive allows offline access through the OneDrive sync app on Windows and Mac.
7️⃣ What’s the maximum file size for SharePoint and OneDrive? The maximum upload limit for SharePoint and OneDrive is 250GB per file.
8️⃣ Does Teams store files separately from SharePoint? No, files shared in Teams are actually stored in the underlying SharePoint document library.
9️⃣ Should I store sensitive data in SharePoint? Yes, but it’s recommended to apply security policies such as DLP (Data Loss Prevention) and access controls.
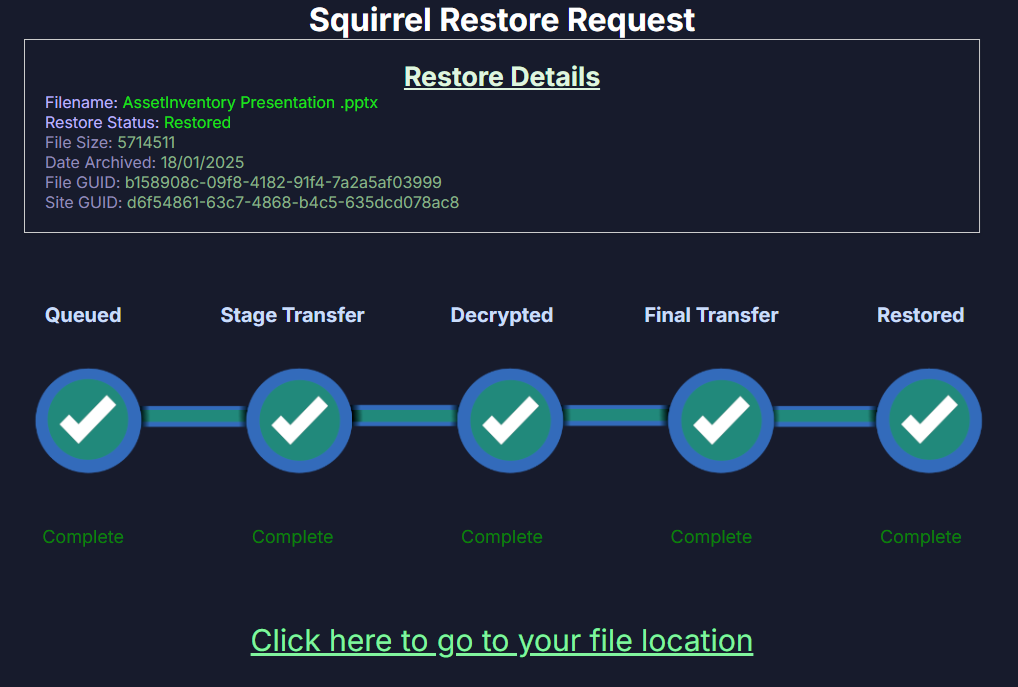
🔟 How can I save SharePoint storage space? Use an archiving solution like Squirrel Archiving to move older files to Azure while maintaining accessibility.
Conclusion
Choosing between OneDrive, SharePoint, and Teams depends on who needs access, how the files will be used, and whether collaboration is required. By following these best practices, you can improve productivity, enhance security, and optimize your Microsoft 365 storage strategy.
If your organization struggles with SharePoint storage limits, consider Squirrel Archiving to optimize space and keep your SharePoint environment efficient.
📢 Need help managing SharePoint storage? Learn more about Squirrel.