
by Mark | Jun 22, 2016 | How To, Patch Management, SCCM
Creating an Effective Patch Management Process for Your Enterprise
As cyber threats continue to grow in number and complexity, keeping your enterprise’s software and hardware up-to-date is crucial for maintaining security. A robust patch management process is key to achieving this goal. In this article, we’ll explore the steps involved in creating an effective patch management process that will help you reduce risk, save time and effort, and gain auditor approval.
Overview of Patch Management Process
One of the critical tasks for administrators is to create a patch management process that can deploy and manage software updates. Admins need to keep track of multiple sources, including blogs, emails, RSS feeds, and forums, to stay up-to-date with the latest vulnerabilities and patches. Having an outdated system can lead to vulnerabilities and potential security holes that hackers can exploit. In large enterprises that require compliance with ISO 27001, ISO 270012, or even SOX (Sarbanes-Oxley), outdated applications, hardware, and systems can raise red flags during audits.
To create a patch management process, you need to follow a set of procedures that involve various stages, including patch management risk, patch management software, and patch deployment.

Patch Management Software
One of the best patch management software available for managing a server and desktop fleet is Microsoft’s System Centre Configuration Manager (SCCM). SCCM not only automates the download and deployment of updates but also inventories all your systems and software, making life easier for administrators responsible for large environments. SCCM should have an up-to-date inventory of your environment, including the operating system types, to deploy patches to the right machines.
Patch Deployment
Automating the deployment of updates to your machines using an Automatic Deployment Rule within SCCM can save time and effort. Setting this rule to coincide when Microsoft releases its monthly updates (Patch Tuesday) is good practice. Before deployment, it is crucial to test the update to ensure it doesn’t break any systems. Gaining approval for deployment will require some sort of rollback functionality.
.
The Patch Management Process for deployment of updates follows these steps:
- SCCM downloads the latest updates from Microsoft on Patch Tuesday.
- Administrator socializes the latest patch releases with relevant parties.
- CAB (Change Approval Board) approval is required for deployment of the latest patches to the Pilot Group.
- The administrator sets a maintenance window and schedules when the patches should be installed.
- Patches are deployed to the Pilot group.
- UAT (User Acceptance Testing) is performed to ensure no issues arise due to patch deployment.
- Once UAT approval has been gained, the administrator presents a new Change Request to CAB for approval of the deployment of patches to Production systems.
- Approval has been accepted, and the administrator sets up a new deployment package for deployment to Production systems.
Patching Risk
Not having Pilot or Development and Test systems that mirror Production can create a roll-back position that is required before CAB will approve any update deployment. This often means the administrator spends late nights ensuring backups are successful or creating snapshots before allowing updates to deploy.
SnaPatch – SCCM Patch Management Addon Software – Reduce Effort and Risk
SnaPatch is an add-on software for Microsoft’s System Centre Configuration Manager that interfaces with your existing SCCM and virtual environment. SnaPatch will automate a snapshot of your virtual servers before SCCM deploys monthly updates, allowing you to gain the auditors’ approval for your ISO 27001, ISO 270012 or even SOX (Sarbanes-Oxley) patching compliance. This process that SnaPatch completes automatically, will give you a quick roll back position should a patch cause errors to your virtual servers. SnaPatch automates it all, from downloading the latest monthly Windows Updates, to completing a snapshot of your servers prior to patches being deployed, then communicating with SCCM that the patches can now deploy, and finally deleting the snapshot after a period of time, all while emailing you alerts about your patching progress.
In conclusion, creating and maintaining a well-defined patch management process is critical for ensuring the security of your environment. Automated patch deployment and testing are essential to save time and reduce effort, while add-on software like SnaPatch can help reduce risk and gain auditor approval. It’s important to understand the risks associated with outdated systems and the potential harm that can occur if those vulnerabilities are exploited. Don’t wait until it’s too late; start developing your patch management process today to keep your enterprise safe and secure. By following the guidelines outlined in this article, you can reduce risk, save time and effort, and ensure compliance with industry standards.

by Mark | Jun 21, 2016 | How To, SCCM
SCCM Update Deployment Issues?
Troubleshooting Tips and Logs to Resolve Common Problems
Are you experiencing issues with deploying updates within SCCM? Don’t worry; you’re not alone. Many administrators struggle with troubleshooting and identifying the root cause of update deployment problems. However, with the right knowledge and tools, you can quickly resolve these issues and ensure your updates are deployed successfully. In this article, we’ll discuss some troubleshooting tips and the logs you can use to identify and resolve common SCCM update deployment issues.
Identifying the Appropriate Log to Troubleshoot SCCM Update Deployment Issues
One of the most challenging aspects of troubleshooting SCCM update deployment issues is identifying which log to look at. Fortunately, SCCM has many logs available to help you determine the root cause of any issues. Here are some of the logs you can review to identify the issue:
Server Side Software Update Logs:
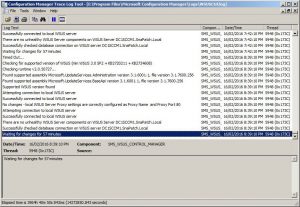
- SUPsetup.log – Installation of SUP Site Role.
- WCM.log, WSUSCtrl.log – Configuration of WSUS Server/SUP.
- WSyncMgr.log – SMS/WSUS Updates Synchronization Issues.
- Objreplmgr.log – Policy Issues for Update Assignments/CI Version Info policies.
- RuleEngine.log – Auto Deployment Rules.
-
Client Side Software Update Logs:
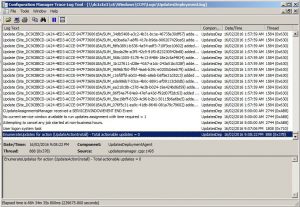
- UpdatesDeployment.log – Deployments, SDK, UX.
- UpdatesHandler.log – Updates, Download.
- ScanAgent.log – Online/Offline scans, WSUS location requests.
- WUAHandler.log – Update status (missing/installed – verbose logging), WU interaction.
- UpdatesStore.log – Update status (missing/installed).
- indirWindowsUpdate.log – Scanning/Installation of updates.
Hopefully these logs will help you troubleshoot Update Deployment from within SCCM. Click these links to see how you can create a SCCM Automatic Deployment Rule for your Microsoft Updates and SCEP Definition Updates to help you automate your update and definitions deployments.
Troubleshooting SCCM Update Deployment Issues
Now that you know which logs to look at, it’s time to start troubleshooting. Here are some common SCCM update deployment issues you may encounter, along with their possible solutions:
Issue 1: Updates are not downloading or installing on client devices.
Solution: Check the UpdatesDeployment.log and UpdatesHandler.log for errors. Make sure the client devices have access to the update source location, and the content is distributed to the distribution point.
Issue 2: The SCCM client is not reporting update compliance status.
Solution: Check the UpdatesStore.log, UpdatesDeployment.log, and WUAHandler.log for errors. Verify that the SCCM client has the correct permissions to read the WSUS catalogs and update metadata.
Issue 3: Automatic Deployment Rules (ADR) are not working correctly.
Solution: Check the RuleEngine.log and WCM.log for errors. Verify that the ADR criteria and schedules are configured correctly and that the update metadata is up to date.
Automating SCCM Update and Definitions Deployments
Manually deploying updates and definitions can be a time-consuming task, especially if you have many devices to manage. SCCM offers Automatic Deployment Rules (ADR), which allow you to automate the process of deploying updates and definition updates. By creating an ADR, you can define criteria for the types of updates to deploy, when to deploy them, and to which collections to deploy them. Here are some links to help you get started with creating SCCM Automatic Deployment Rules for your Microsoft Updates and SCEP Definition Updates:
In conclusion, SCCM update deployment issues can be frustrating, but with the right knowledge and tools, you can quickly identify and resolve them. By reviewing the appropriate logs and following the troubleshooting tips we’ve outlined, you can ensure that your updates are deployed successfully. Additionally, by automating the deployment

by Mark | Jun 19, 2016 | How To, Patch Management, SCCM
How to Manually Download and Deploy Updates with SCCM
If you are an IT professional who is responsible for managing software updates for an organization, then you know how important it is to keep all systems up-to-date with the latest patches and security updates. Microsoft’s System Centre Configuration Manager (SCCM) is a popular tool used by many IT professionals for patch management. In this article, we will discuss how to manually download and deploy updates with SCCM.
SCCM FAQs
What is SCCM?
SCCM stands for System Centre Configuration Manager, which is a popular tool used by IT professionals for managing software updates, among other things.
Why would I need to manually download updates with SCCM?
There may be scenarios where the Auto Deployment Rule fails to download updates, or when using a third-party tool like SnaPatch, where you need to manually download and deploy updates with SCCM.
Can I automate the process of downloading and deploying updates with SCCM?
Yes, SCCM provides an Automatic Deployment Rules (ADR) feature, which can automate the process of downloading and deploying updates to multiple systems.
What are the benefits of using SCCM for patch management?
SCCM offers centralized management, automated deployment, reporting, and security features for patch management.
Is it necessary to manually download updates with SCCM?
It depends on your organization’s specific needs and scenarios. In most cases, SCCM’s Auto Deployment Rules feature can effectively manage software updates without the need for manual downloading and deployment. However, there may be certain situations where manual intervention is required.
How do I know which updates to download manually with SCCM?
You can use SCCM’s Software Updates feature to view available updates and select the ones you need to download manually.
What if I don’t have an Auto Deployment Rule set up in SCCM?
In that case, you can follow the same steps mentioned in the article to manually download updates with SCCM.
How long does it take to download updates manually with SCCM?
The time it takes to download updates manually with SCCM depends on the size of the updates and the speed of your internet connection.
Can I download updates manually with SCCM on multiple computers at once?
Yes, you can deploy updates manually to multiple computers at once by selecting multiple computers in SCCM’s console and initiating the update download process.
Are there any risks associated with manually downloading updates with SCCM?
There is always a risk associated with any manual process, such as human error, downloading the wrong updates, or disrupting systems during the update process. However, SCCM provides a range of tools and features to help mitigate these risks. It is important to follow best practices and guidelines when manually downloading updates with SCCM.
Step-by-Step Guide to Manually Download Updates with SCCM
If you ever need to manually download and deploy updates with SCCM, or even when using SnaPatch, and you dont know how to download updates that havent been downloaded automatically by the Auto Deployment Rule, this post will show you how.
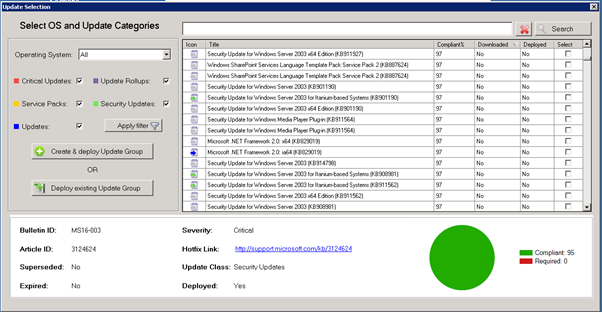
To kick off a manual download of updates using SCCM, follow these steps.
Open your SCCM console and go to Software Library, then expand Software Updates and then click on All Software Updates.
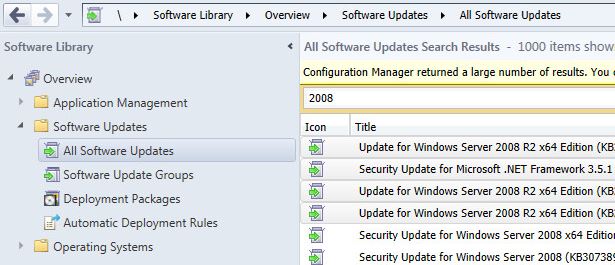
Let the list populate and select the updates that want to download, then right click and choose Download.
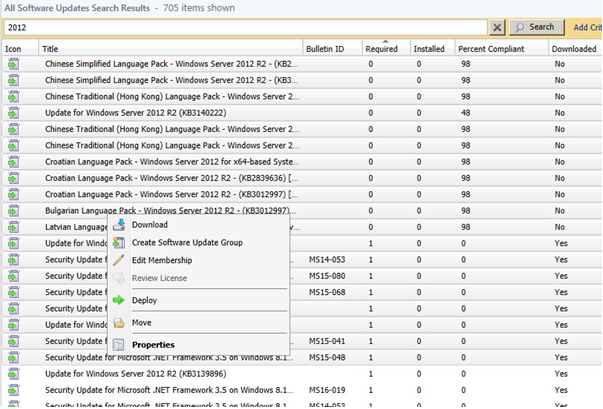
It will then prompt your to Select a Deployment Package. Click Browse.
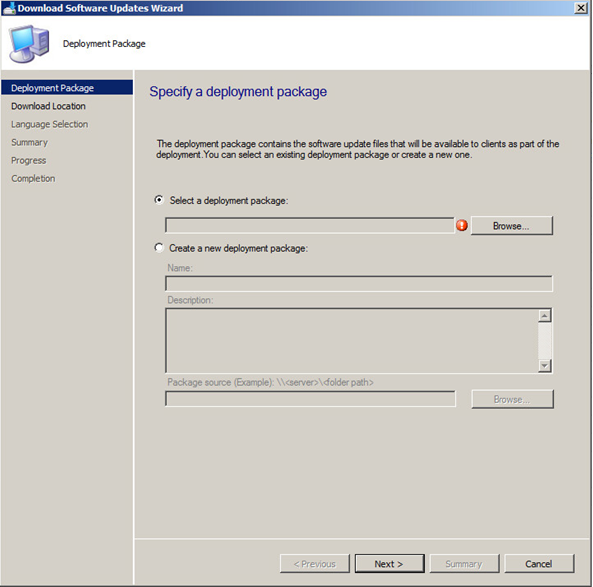
Select the Auto Deployment Rule that you use for your SnaPatch deployments and then click on OK.
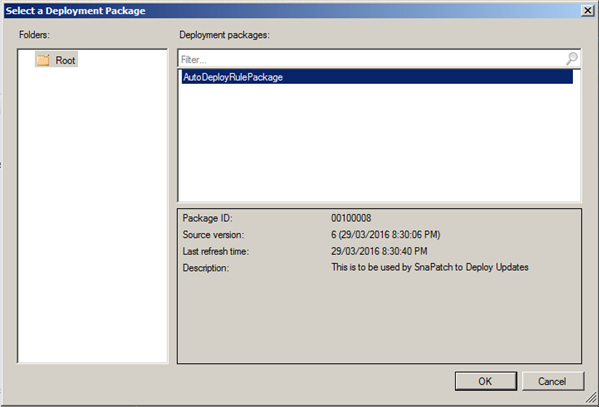
Once the deployment rule had been selected, click on Next.
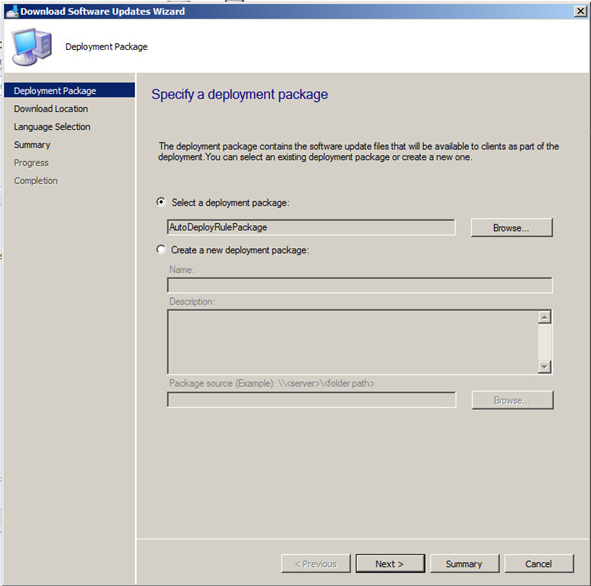
Now choose to Download software updates from the Internet.
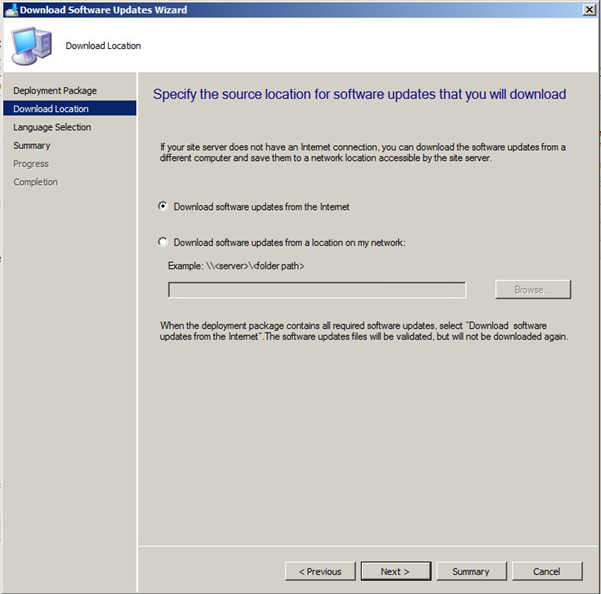
Choose the required update language.
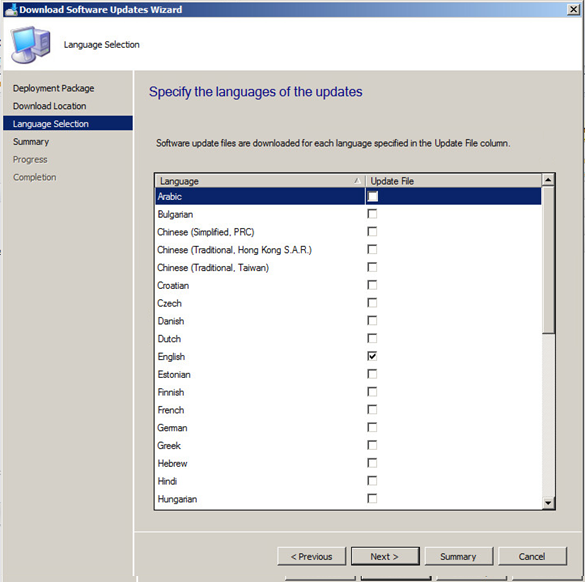
Now you should be ready to download the updates you have selected. If ready to do so, click on Next.
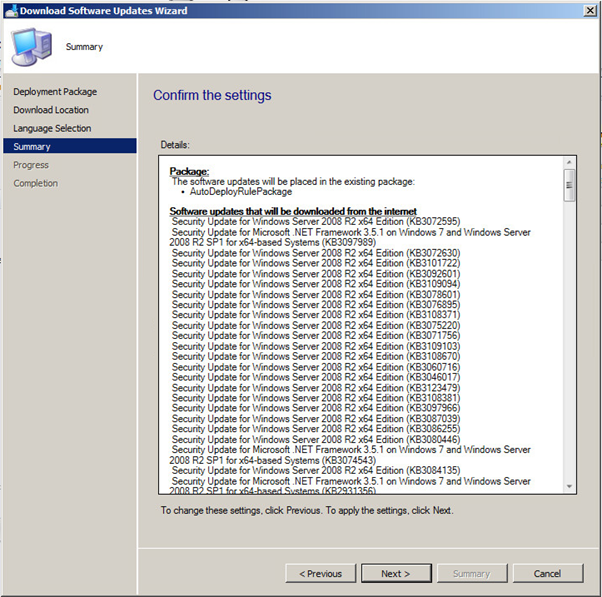
Your updates will start downloading. Note that this may take some time to complete the downloads.
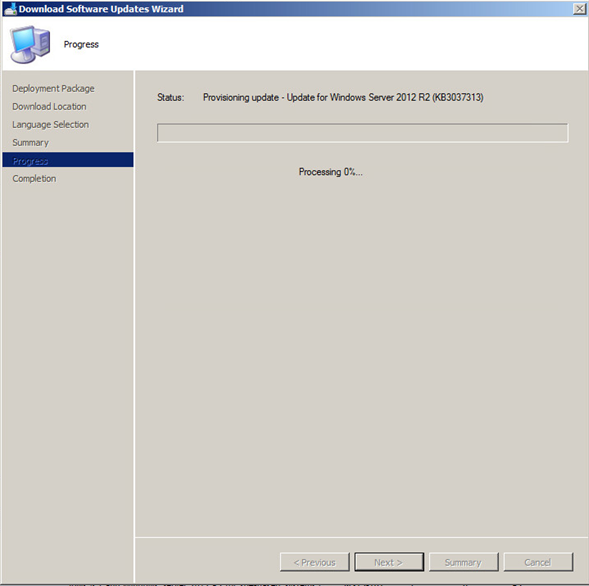
Hopefully all went well and your updates are now ready to be deployed.
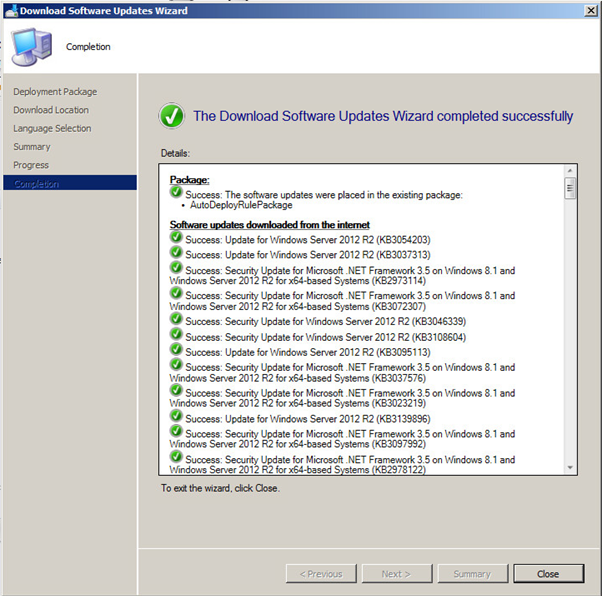
Click this link to see how to setup a SCCM Automatic Deployment Rule.
In this article, we have discussed how to manually download and deploy updates with SCCM. We have also highlighted the benefits of using SCCM for patch management. By following the steps outlined in this article, you can ensure that all systems in your organization are up-to-date with the latest patches and security updates.

by Mark | Mar 29, 2016 | How To, Patch Management
Manually download updates with SCCM
In today’s fast-paced world, keeping up with the latest software updates is critical. With new features, bug fixes, and security patches being released every day, it’s essential to ensure that your systems are up to date. Microsoft’s System Center Configuration Manager (SCCM) is an enterprise-grade software management solution that allows you to deploy and manage software updates across your organization. In this article, we will explore how to manually download updates with SCCM to keep your systems up to date.
What is SCCM?
SCCM is a software management tool developed by Microsoft. It allows IT administrators to manage and deploy software updates, security patches, and other configuration changes across their organization’s Windows devices. SCCM provides a centralized console where administrators can view and manage all of their organization’s Windows devices and ensure that they are up-to-date with the latest software and security updates.
Why Use SCCM?
There are several benefits to using SCCM for software management:
- Centralized management: SCCM provides a centralized console for managing all Windows devices in an organization, making it easy to manage software updates and security patches across multiple devices.
- Automation: SCCM can automate the deployment of software updates and security patches, saving IT administrators time and ensuring that updates are consistently applied across all devices.
- Reporting: SCCM provides detailed reporting capabilities, allowing administrators to track which devices are up-to-date with the latest software and security updates.
Now that we’ve covered the basics of SCCM let’s dive into the process of manually downloading updates with SCCM.
Understanding SCCM Software Updates
Before we dive into how to manually download updates with SCCM, let’s first understand what software updates are and how SCCM handles them. Software updates are packages that contain updates to existing software, such as security patches, bug fixes, and feature enhancements. SCCM uses the Windows Server Update Services (WSUS) infrastructure to manage and deploy software updates.
WSUS is a server role that allows administrators to manage and distribute updates for Windows operating systems and other Microsoft software. SCCM uses WSUS to download software updates from Microsoft Update and distribute them to client computers in the organization. SCCM also allows administrators to create and deploy custom software updates to meet specific business needs.
Now that we have a basic understanding of how SCCM handles software updates let’s explore how to manually download updates with SCCM.
If you ever have the need to Manually Download Updates with SCCM (like with a zero day exploit deployment) I will show you how to below. This helps even if updates haven’t been downloaded automatically by the Auto Deployment Rule.
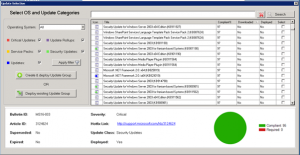
To kick off a manual download of updates with SCCM, follow these steps.
Open your SCCM console and go to Software Library, then expand Software Updates and then click on All Software Updates.
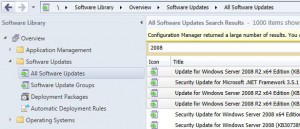
Let the list populate and select the updates that want to download, then right click and choose Download.
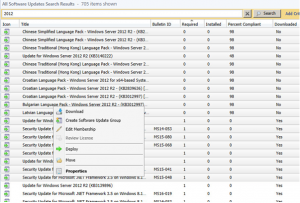
It will then prompt your to Select a Deployment Package. Click Browse.
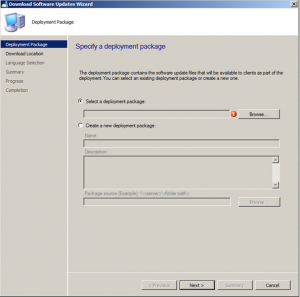
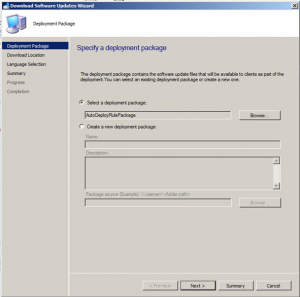
Select the Auto Deployment Rule that you use for your monthly patch deployments and then click on OK.
Once the deployment rule had been selected, click on Next.
Now choose to Download software updates from the Internet.
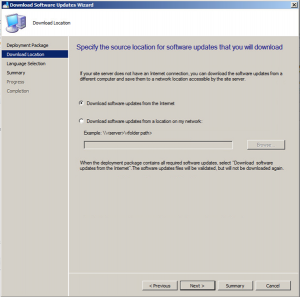
Choose the required update language then click Next.
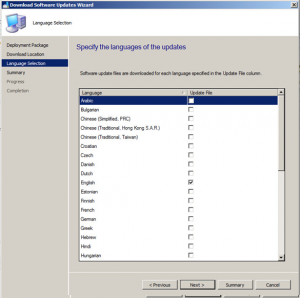
Now you should be ready to download the updates you have selected. If ready to do so, click on Next.
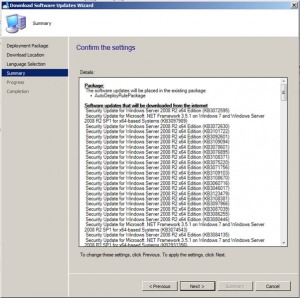
Your updates will start downloading. Note that this may take some time to complete the downloads.
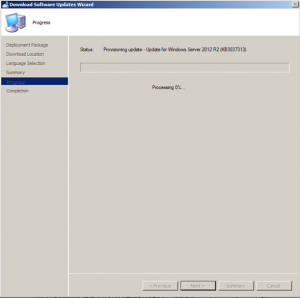
Hopefully all went well and your updates are now ready to be deployed.
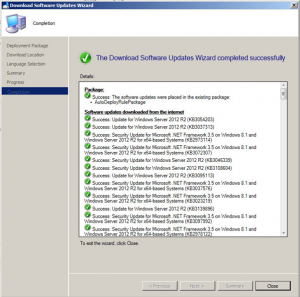
This is a great way to download updates really quickly and make them available to deploy them to your desktops and servers. Click the link to see another great post on how to create a SCCM Automatic Deployment Rule.
by Mark | Mar 9, 2016 | Patch Releases, Security
The following thirteen Patch Tuesday updates / patches have been released by Microsoft for the January 2016 Update deployment.
Are you ready to start deploying and remove the patching risk using SnaPatch Patch Management Software?
MS16-023 – Critical
Cumulative Security Update for Internet Explorer (3142015)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-024 – Critical
Cumulative Security Update for Microsoft Edge (3142019)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-025 – Important
Security Update for Windows Library Loading to Address Remote Code Execution (3140709)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if Microsoft Windows fails to properly validate input before loading certain libraries. However, an attacker must first gain access to the local system with the ability to execute a malicious application.
MS16-026 – Critical
Security Update for Graphic Fonts to Address Remote Code Execution (3143148)
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if an attacker either convinces a user to open a specially crafted document, or to visit a webpage that contains specially crafted embedded OpenType fonts.
MS16-027 – Critical
Security Update for Windows Media to Address Remote Code Execution (3143146)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow remote code execution if a user opens specially crafted media content that is hosted on a website.
MS16-028 – Critical
Security Update for Microsoft Windows PDF Library to Address Remote Code Execution (3143081)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow remote code execution if a user opens a specially crafted .pdf file.
MS16-029 – Important
Security Update for Microsoft Office to Address Remote Code Execution (3141806)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-030 – Important
Security Update for Windows OLE to Address Remote Code Execution (3143136)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow remote code execution if Windows OLE fails to properly validate user input. An attacker could exploit the vulnerabilities to execute malicious code. However, an attacker must first convince a user to open either a specially crafted file or a program from either a webpage or an email message.
MS16-031 – Important
Security Update for Microsoft Windows to Address Elevation of Privilege (3140410)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker is able to log on to a target system and run a specially crafted application.
MS16-032 – Important
Security Update for Secondary Logon to Address Elevation of Privilege (3143141)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if the Windows Secondary Logon Service fails to properly manage request handles in memory.
MS16-033 – Important
Security Update for Windows USB Mass Storage Class Driver to Address Elevation of Privilege (3143142)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker with physical access inserts a specially crafted USB device into the system.
MS16-034 – Important
Security Update for Windows Kernel-Mode Drivers to Address Elevation of Privilege (3143145)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to the system and runs a specially crafted application.
MS16-035 – Important
Security Update for .NET Framework to Address Security Feature Bypass (3141780)
This security update resolves a vulnerability in the Microsoft .NET Framework. The security feature bypass exists in a .NET Framework component that does not properly validate certain elements of a signed XML document.






























