
by Mark | Jun 19, 2016 | How To, Patch Management, SCCM
How to Manually Download and Deploy Updates with SCCM
If you are an IT professional who is responsible for managing software updates for an organization, then you know how important it is to keep all systems up-to-date with the latest patches and security updates. Microsoft’s System Centre Configuration Manager (SCCM) is a popular tool used by many IT professionals for patch management. In this article, we will discuss how to manually download and deploy updates with SCCM.
SCCM FAQs
What is SCCM?
SCCM stands for System Centre Configuration Manager, which is a popular tool used by IT professionals for managing software updates, among other things.
Why would I need to manually download updates with SCCM?
There may be scenarios where the Auto Deployment Rule fails to download updates, or when using a third-party tool like SnaPatch, where you need to manually download and deploy updates with SCCM.
Can I automate the process of downloading and deploying updates with SCCM?
Yes, SCCM provides an Automatic Deployment Rules (ADR) feature, which can automate the process of downloading and deploying updates to multiple systems.
What are the benefits of using SCCM for patch management?
SCCM offers centralized management, automated deployment, reporting, and security features for patch management.
Is it necessary to manually download updates with SCCM?
It depends on your organization’s specific needs and scenarios. In most cases, SCCM’s Auto Deployment Rules feature can effectively manage software updates without the need for manual downloading and deployment. However, there may be certain situations where manual intervention is required.
How do I know which updates to download manually with SCCM?
You can use SCCM’s Software Updates feature to view available updates and select the ones you need to download manually.
What if I don’t have an Auto Deployment Rule set up in SCCM?
In that case, you can follow the same steps mentioned in the article to manually download updates with SCCM.
How long does it take to download updates manually with SCCM?
The time it takes to download updates manually with SCCM depends on the size of the updates and the speed of your internet connection.
Can I download updates manually with SCCM on multiple computers at once?
Yes, you can deploy updates manually to multiple computers at once by selecting multiple computers in SCCM’s console and initiating the update download process.
Are there any risks associated with manually downloading updates with SCCM?
There is always a risk associated with any manual process, such as human error, downloading the wrong updates, or disrupting systems during the update process. However, SCCM provides a range of tools and features to help mitigate these risks. It is important to follow best practices and guidelines when manually downloading updates with SCCM.
Step-by-Step Guide to Manually Download Updates with SCCM
If you ever need to manually download and deploy updates with SCCM, or even when using SnaPatch, and you dont know how to download updates that havent been downloaded automatically by the Auto Deployment Rule, this post will show you how.
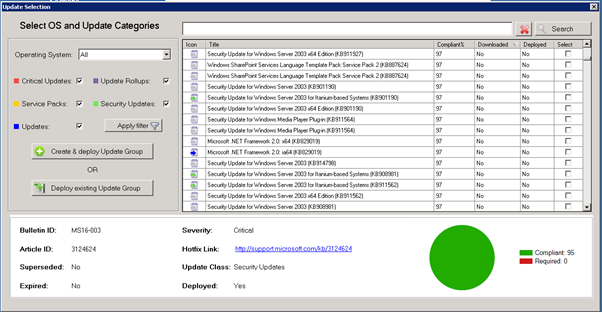
To kick off a manual download of updates using SCCM, follow these steps.
Open your SCCM console and go to Software Library, then expand Software Updates and then click on All Software Updates.
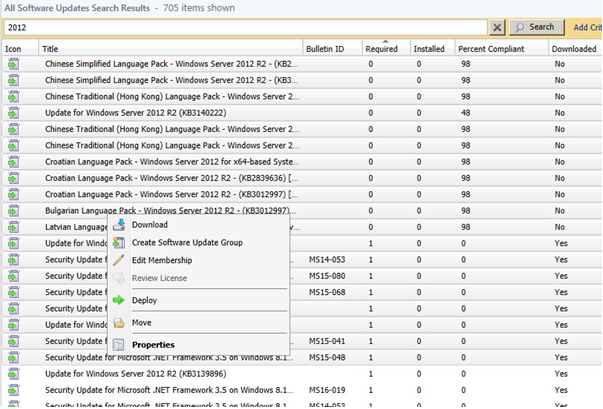
Let the list populate and select the updates that want to download, then right click and choose Download.
It will then prompt your to Select a Deployment Package. Click Browse.
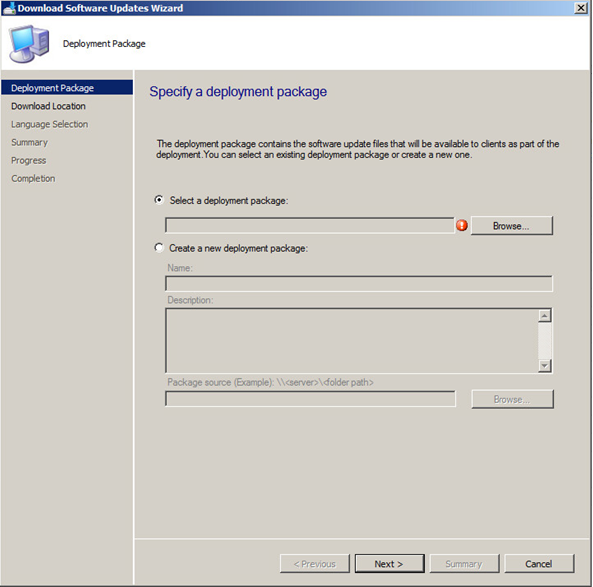
Select the Auto Deployment Rule that you use for your SnaPatch deployments and then click on OK.
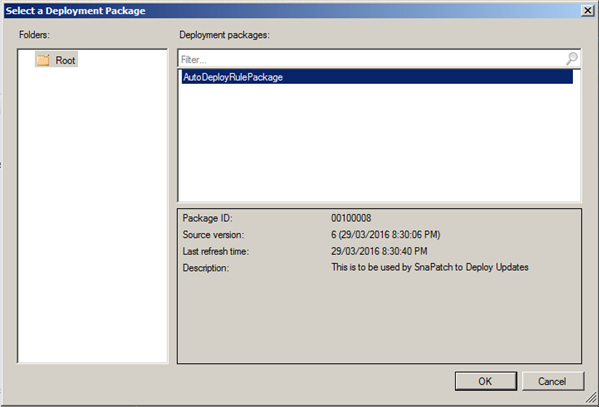
Once the deployment rule had been selected, click on Next.
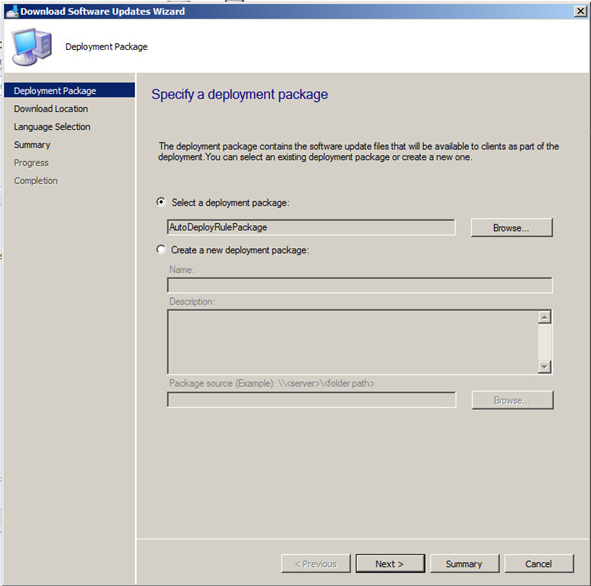
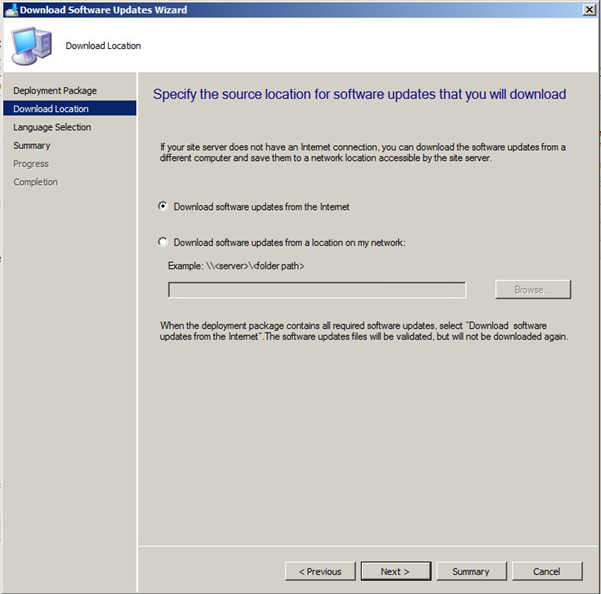
Now choose to Download software updates from the Internet.
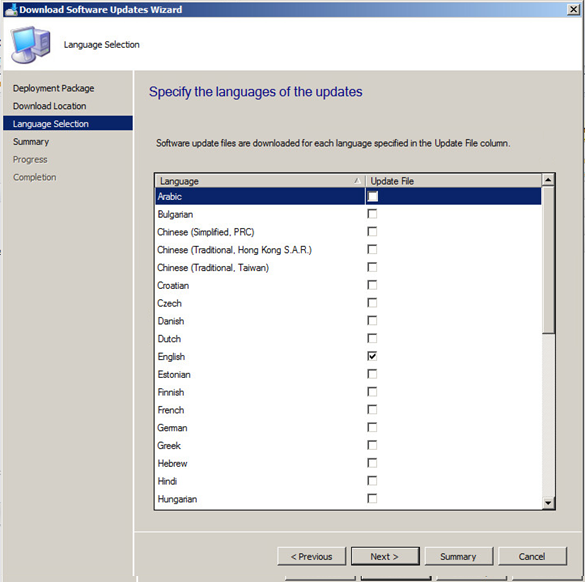
Choose the required update language.
Now you should be ready to download the updates you have selected. If ready to do so, click on Next.
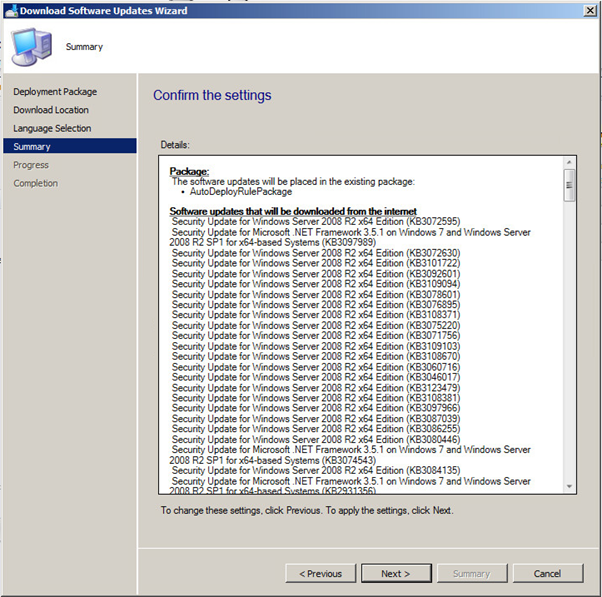
Your updates will start downloading. Note that this may take some time to complete the downloads.
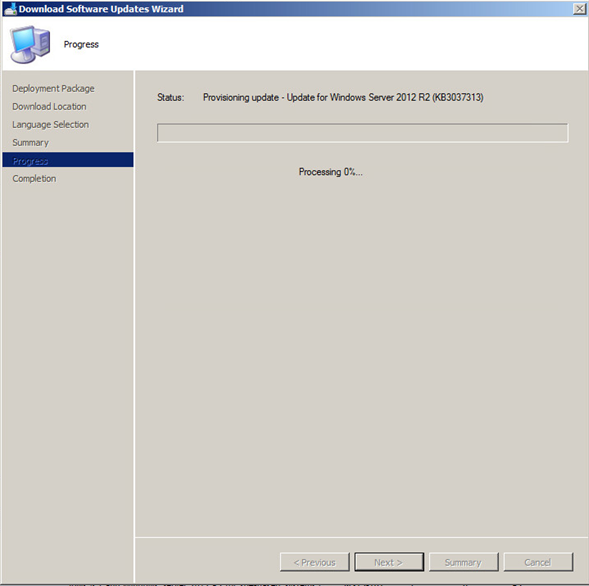
Hopefully all went well and your updates are now ready to be deployed.
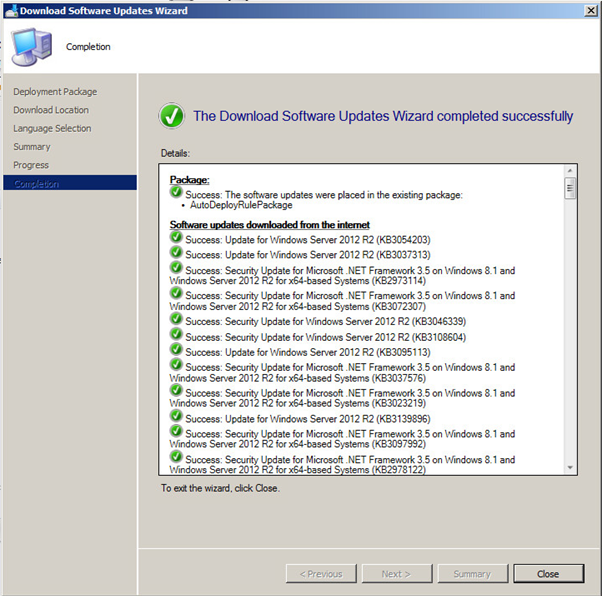
Click this link to see how to setup a SCCM Automatic Deployment Rule.
In this article, we have discussed how to manually download and deploy updates with SCCM. We have also highlighted the benefits of using SCCM for patch management. By following the steps outlined in this article, you can ensure that all systems in your organization are up-to-date with the latest patches and security updates.

by Mark | Jun 19, 2016 | How To, Patch Management, SCCM
Microsoft SCCM update deployment best practices
Microsoft SCCM (System Center Configuration Manager) is a powerful tool for deploying updates to Windows-based computers. However, deploying updates with SCCM can be tricky if you don’t follow best practices. In this article, we will discuss some of the best practices that Microsoft recommends for deploying Microsoft Updates from SCCM 2012.
Limit Software Updates to 1000 in a Single Deployment
One of the best practices recommended by Microsoft is to limit the number of software updates to 1000 for each software update deployment. When you create an automatic deployment rule or manually deploy software updates, do not select more than 1000 updates to deploy. This will prevent the deployment from becoming too large and overwhelming the systems that are receiving the updates.
Create a New Software Update Group for Every Deployment
Another best practice is to create a new software update group each time an automatic deployment rule runs for “Patch Tuesday” or for general deployment. There is a limit of 1000 software updates for a software update deployment. When you create an automatic deployment rule, you can specify whether to use an existing update group or create a new update group each time the rule runs. If you specify criteria in an automatic deployment rule that results in multiple software updates and the rule runs on a recurring schedule, specify to create a new software update group each time the rule runs. This will prevent the deployment from surpassing the limit of 1000 software updates per deployment.
Use an Existing Software Update Group for Endpoint Protection Definition Updates
When you use an automatic deployment rule to deploy Endpoint Protection definition updates on a frequent basis, it is recommended to always use an existing software update group. Otherwise, potentially hundreds of software update groups will be created over time. Typically, definition update publishers will set definition updates to expire when they are superseded by four newer updates. Therefore, the software update group that is created by the automatic deployment rule will never contain more than four definition updates for the publisher: one active and three superseded.
Test updates before deploying them
It’s always a good idea to test updates in a non-production environment before deploying them in a production environment. This can help identify any issues or conflicts that may arise during the deployment process.
Use maintenance windows
Maintenance windows can be used to specify a period of time during which updates can be installed on client machines. This can help prevent updates from being installed during critical business hours or when users are actively working on their computers.
Monitor deployment status
It’s important to monitor the deployment status of updates to ensure that they are being installed successfully. SCCM provides various reports that can be used to monitor deployment status.
Keep SCCM up-to-date
It’s important to keep SCCM up-to-date with the latest updates and hotfixes. This can help ensure that SCCM is functioning properly and can help prevent any issues or bugs from affecting the update deployment process.
SCCM Update Deployment FAQs
| Question |
Answer |
What is SCCM?
|
SCCM stands for System Center Configuration Manager. It is a software management tool that allows organizations to manage and deploy software, updates, and patches across multiple devices and systems. |
What are some best practices for deploying updates with SCCM?
|
Some best practices for deploying updates with SCCM include scheduling updates during non-business hours, testing updates on a small group of devices before deploying to the entire organization, and creating a rollback plan in case of issues. It’s also important to regularly monitor the deployment process and report any issues or errors. |
How should updates be prioritized for deployment?
|
Updates should be prioritized based on their criticality and potential impact on the organization. Security updates should always be prioritized, followed by critical updates and then important updates. Updates that are not critical or important can be deferred or postponed. |
How often should updates be deployed?
|
The frequency of updates deployment can vary depending on the organization’s needs and policies. However, it’s generally recommended to deploy updates at least once a month to ensure that systems are protected against known vulnerabilities and threats. |
How can SCCM help with update deployment?
|
SCCM provides a centralized platform for managing and deploying updates across multiple devices and systems. It allows administrators to automate the update deployment process, monitor the deployment status, and report any issues or errors. SCCM can also help ensure that updates are deployed in a consistent and standardized manner, reducing the risk of errors and inconsistencies. |
Should you have a Patching Process / Schedule?
|
Yes, a patching process will schedule when you regularly deploy your updates. It helps monitor and track when patches should be deployed to which environment. |
What should be included in a rollback plan?
|
A rollback plan should include steps for undoing the update deployment, as well as a plan for communicating with end-users and stakeholders. It should also identify any potential risks or challenges associated with rolling back updates, and outline strategies for mitigating those risks.
You can also use SnaPatch, which automates a snapshot of your servers prior to patch deployment. This will allow you to easily roll back should a patch cause an issue to your sever fleet. |
How can SCCM help with update reporting?
|
SCCM provides a variety of reporting tools that allow administrators to monitor the status of update deployments, identify any issues or errors, and report on compliance with organizational policies and regulatory requirements. These reports can help ensure that systems are up-to-date and secure, and can also provide valuable insights into the overall health and performance of the IT environment. |
SCCM Update Deployment Final Thoughts
What is SCCM update deployment?
SCCM (System Center Configuration Manager) is a software management tool used by IT administrators to deploy updates to client machines. SCCM update deployment involves deploying software updates to client machines in a controlled and efficient manner.
Why is SCCM update deployment important?
SCCM update deployment is important because it helps ensure that client machines are up-to-date with the latest security patches and software updates. This can help prevent security vulnerabilities and improve the overall performance and stability of client machines.
What are some best practices for SCCM update deployment?
Some best practices for SCCM update deployment include limiting the number of software updates to 1000 per deployment, creating a new software update group for each automatic deployment rule, using an existing software update group for Endpoint Protection definition updates, testing updates before deployment, using maintenance windows, monitoring deployment status, and keeping SCCM up-to-date with the latest updates and hotfixes.
How do I monitor the deployment status of updates in SCCM?
SCCM provides various reports that can be used to monitor the deployment status of updates. These reports can be accessed from the SCCM console and can provide information on the success or failure of update deployments.
How often should I deploy updates in SCCM?
The frequency of update deployments in SCCM can vary depending on the organization’s needs and policies. However, it is generally recommended to deploy updates on a regular basis, such as monthly or quarterly, to ensure that client machines are up-to-date with the latest security patches and software updates.

by Mark | Jun 19, 2016 | How To, SCCM
Streamlining SCCM Installation with Microsoft’s Prerequisite Tool
Microsoft has recently launched a valuable tool that simplifies the installation process of System Center Configuration Manager (SCCM). The SCCM Installation Prerequisites tool helps administrators ensure that the necessary prerequisites are in place before the installation process begins. This tool also automatically installs the required prerequisites, saving you time and effort.
Checking and Installing Prerequisites Made Easy
With the SCCM Installation Prerequisites tool, you can easily verify that all the required prerequisites are already in place. It checks for prerequisites for a Central Primary site, Primary or Secondary Sites, and other site system roles, such as Management Point, Application Catalog, Distribution Point, Enrollment Point, among others.
Additionally, the tool installs any missing prerequisites automatically. This reduces the risk of errors and makes the installation process smoother and quicker.
Installing SCCM Made More Efficient
Installing SCCM can be a challenging task, particularly when it comes to the setup process. However, the SCCM Installation Prerequisites tool streamlines the installation process and makes it more efficient. The tool is designed to run before the SCCM installation process begins, which ensures that all prerequisites are in place and ready to go.
To use the SCCM Installation Prerequisites tool, simply download it from the Microsoft website and run it before you begin the SCCM installation. It’s that simple!
Overall, Microsoft’s SCCM Installation Prerequisites tool is a valuable tool that simplifies the SCCM installation process. It ensures that all prerequisites are in place and automatically installs any missing ones, making the installation process more efficient and streamlined. So, if you’re an administrator who regularly installs SCCM, this tool is a must-have in your toolkit.

by Mark | Jun 19, 2016 | SCCM
A Comprehensive Guide to SCCM Build Numbers
As an IT professional, it’s essential to be aware of the various build numbers of Microsoft’s System Center Configuration Manager (SCCM). This guide will provide an overview of SCCM build numbers, including their release dates and descriptions. By the end of this guide, you’ll have a better understanding of SCCM build numbers and be able to choose the right version for your organization.
SCCM Build Numbers Overview
SCCM is an enterprise management solution from Microsoft that allows IT teams to manage both traditional and modern devices. It provides a comprehensive set of tools to manage Windows, macOS, Linux, Unix, and mobile devices running iOS, Android, and Windows Phone. SCCM helps manage and deploy software, as well as security updates and patches.
SCCM comes in different versions, and each version has its build numbers, release dates, and descriptions. The following is an overview of SCCM build numbers:
System Centre Configuration Manager (SCCM) by Microsoft versions
System Center Configuration Manager 2016
| Build Number |
Release Date |
Description |
| 5.0.8299.1000 |
2015, September 22 |
SCCM 2016 Technical Preview 3 (Update 1509) |
| 5.0.8315.1000 |
2015, October 14 |
SCCM 2016 Technical Preview 3 (Update 1510) |
| 5.0.8325.1000 |
2015, November 12 |
SCCM 2016 Technical Preview 4 (Update 1511) |
| 5.0.8336.1000 |
2015, December 18 |
SCCM 2016 Technical Preview 4 (Update 1512) |
| 5.0.8347.1000 |
2016, January 27 |
SCCM 2016 Technical Preview 4 (Update 1601) |
System Center Configuration Manager 2012 R2
| Build Number |
Release Date |
Description |
| 5.00.7958.1000 |
2013, October 18 |
SCCM 2012 R2 RTM |
| 5.00.7958.1101 |
2013, November 02 |
SCCM 2012 Post R2 Hotfix |
| 5.00.7958.1203 |
2014, March 28 |
SCCM 2012 R2 CU1 |
| 5.00.7958.1303 |
2014, June 27 |
SCCM 2012 R2 CU2 |
| 5.00.7958.1401 |
2014, September 23 |
SCCM 2012 R2 CU3 |
| 5.00.7958.1501 |
2015, February 2 |
SCCM 2012 R2 CU4 |
| 5.00.7958.1604 |
2015, May 6 |
SCCM 2012 R2 CU5 |
| 5.00.8239.1000 |
2015, May 14 |
SCCM 2012 R2 SP1 |
| 5.00.8239.1203 |
2015, August 4 |
SCCM 2012 R2 SP1 CU1 |
| 5.00.8239.1301 |
2015, November 10 |
SCCM 2012 R2 SP1 CU2 |
System Center Configuration Manager 2012 SP1 & SP2
| Build Number |
Release Date |
Description |
| 5.00.7804.1000 |
– |
SCCM 2012 SP1 |
| 5.00.7804.1202 |
|
SCCM 2012 SP1 CU1 |
| 5.00.7804.1300 |
|
SCCM 2012 SP1 CU2 |
| 5.00.7804.1400 |
|
SCCM 2012 SP1 CU3 |
| 5.00.7804.1500 |
|
SCCM 2012 SP1 CU4 |
| 5.00.7804.1600 |
2014, July 23 |
SCCM 2012 SP1 CU5 |
| 5.00.8239.1000 |
2015, May 14 |
SCCM 2012 SP2 |
| 5.00.8239.1203 |
2015, August 4 |
SCCM 2012 SP2 CU1 |
| 5.00.8239.1301 |
2015, November 10 |
SCCM 2012 SP2 CU2 |
System Center Configuration Manager 2012
| Build Number |
Release Date |
Description |
| 5.00.7711.0000 |
2012, March 31 |
SCCM 2012 RTM |
| 5.00.7711.0200 |
2012, August 22 |
SCCM 2012 CU1 |
| 5.00.7711.0301 |
2012, November 27 |
SCCM 2012 CU2 |
System Center Configuration Manager 2007
| Build Number |
Release Date |
Description |
| 4.00.5135.0000 |
|
SCCM 2007 Beta 1 |
| 4.00.5125.0000 |
|
SCCM 2007 Beta 1 Escrow |
| 4.00.5221.0000 |
|
SCCM 2007 Beta 1 Refresh Escrow |
| 4.00.5224.0000 |
|
SCCM 2007 Beta 1 Refresh |
| 4.00.5224.0000 |
|
SCCM 2007 Beta 1 Refresh |
| 4.00.5571.0000 |
|
SCCM 2007 Beta 2 Escrow |
| 4.00.5574.0000 |
|
SCCM 2007 Beta 2 Escrow Update |
| 4.00.5578.0000 |
|
SCCM 2007 Beta 2 with a hotfix |
| 4.00.5578.0002 |
|
SCCM 2007 RC0 Preview |
| 4.00.5790.0000 |
|
SCCM 2007 RC0 Preview |
| 4.00.5815.0000 |
|
SCCM 2007 RC0 |
| 4.00.5924.0000 |
|
SCCM 2007 escrow |
| 4.00.5931.0001 |
|
SCCM 2007 RTM |
| 4.00.6086.1000 |
|
SCCM 2007 SP1 (prerelease) |
| 4.00.6221.1000 |
|
SCCM 2007 SP1 |
| 4.00.6221.1193 |
|
FIX for SCCM 2007 SP1 and SP2 |
| 4.00.6425.2000 |
|
SCCM 2007 SP2 beta |
| 4.00.6468.2001 |
|
SCCM 2007 SP2 RC |
| 4.00.6487.2000 |
|
SCCM 2007 SP2 |
| 4.00.6487.2111 |
|
FIX for SCCM 2007 SP1 and SP2 |
| 4.00.6487.2157 |
|
SCCM 2007 SP2 R3 |
| 4.00.6487.2207 |
2012, December 03 |
FIX for SCCM 2007 SP2 |
| 4.00.6487.2700 |
|
SCCM SP2 R2 with ICP2 |
| 4.00.6487.2857 |
|
SCCM SP2 R3 with ICP2 |
SMS 2003
| Build Number |
Release Date |
Description |
| 2.50.2726.0020 |
– |
SMS 2003 RTM |
| 2.50.3174.1018 |
2004, September 10 |
SMS 2003 SP1 |
| 2.50.4160.2000 |
2006, February 13 |
SMS 2003 SP2 |
| 2.50.4253.3000 |
2007, May 2 |
SMS 2003 SP3 |
SMS 2.0
| Build Number |
Release Date |
Description |
| 2.00.1239.0000 |
– |
SMS 2.0 RTM |
| 2.00.1380.1000 |
– |
SMS 2.0 SP1 |
| 2.00.1493.2000 |
– |
SMS 2.0 SP2 |
| 2.00.1493.3000 |
– |
SMS 2.0 SP3 |
| 2.00.1493.4000 |
– |
SMS 2.0 SP4 |
| 2.00.1493.5000 |
– |
SMS 2.0 SP5 |
See how SnaPatch can help with Windows update deployment, further extending your SCCM infrastructure and giving you back more time with your family.
How to check what version of SCCM you are using?
To check the build number of SCCM, you can go to the SCCM Console and click on the “Administration” tab. Then, right-click on “Site Configuration” and select “Sites.” Next, select the site you want to check and click on “Properties.”
In the “Site Properties” window, you can see the build number under the “General” tab in the “Site version” section. The build number is listed as “Version X.0.YYYY.ZZZZ.”
It’s important to keep track of the build numbers for SCCM because Microsoft releases regular updates and hotfixes for SCCM that fix bugs and improve performance. By staying up-to-date with the latest build number, you can ensure that you have the latest features and fixes for SCCM.
In addition, Microsoft also releases new versions of SCCM every few years. The latest version as of the knowledge cutoff date of this response is SCCM 2110. Each new version typically includes significant updates and improvements to the product.
Understanding the build numbers of SCCM is crucial for maintaining a secure, stable, and up-to-date environment. By regularly checking for updates and staying up-to-date with the latest build numbers, you can ensure that your SCCM environment is functioning optimally.

by Mark | Jun 19, 2016 | Patch Management, Patch Releases
The following seventeen Patch Tuesday updates / patches have been released by Microsoft for the June 2016 Update deployment.
Are you ready to start deploying and remove the patching risk using SnaPatch Patch Management Software?
MS16-063 – Critical
Cumulative Security Update for Internet Explorer (3163649)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-068 – Critical
Cumulative Security Update for Microsoft Edge (3163656)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than users with administrative user rights.
MS16-069 – Critical
Cumulative Security Update for JScript and VBScript (3163640)
This security update resolves vulnerabilities in the JScript and VBScript scripting engines in Microsoft Windows. The vulnerabilities could allow remote code execution if a user visits a specially crafted website. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited these vulnerabilities could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-070 – Critical
Security Update for Microsoft Office (3163610)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-071 – Critical
Security Update for Microsoft Windows DNS Server (3164065)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker sends specially crafted requests to a DNS server.
MS16-072– Important
Security Update for Group Policy (3163622)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker launches a man-in-the-middle (MiTM) attack against the traffic passing between a domain controller and the target machine..
MS16-073 – Important
Security Update for Windows Kernel-Mode Drivers (3164028)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application.
MS16-074 – Important
Security Update for Microsoft Graphics Component (3164036)
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow elevation of privilege if a user opens a specially crafted application.
MS16-075 – Important
Security Update for Windows SMB Server (3164038)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to the system and runs a specially crafted application.
MS16-076 – Important
Security Update for Netlogon (3167691)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker with access to a domain controller (DC) on a target network runs a specially crafted application to establish a secure channel to the DC as a replica domain controller.
MS16-077– Important
Security Update for WPAD (3165191)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if the Web Proxy Auto Discovery (WPAD) protocol falls back to a vulnerable proxy discovery process on a target system.
MS16-078 – Important
Security Update for Windows Diagnostic Hub (3165479)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application.
MS16-079 – Important
Security Update for Microsoft Exchange Server (3160339)
This security update resolves vulnerabilities in Microsoft Exchange Server. The most severe of the vulnerabilities could allow information disclosure if an attacker sends a specially crafted image URL in an Outlook Web Access (OWA) message that is loaded, without warning or filtering, from the attacker-controlled URL.
MS16-080 – Important
Security Update for Microsoft Windows PDF (3164302)
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted .pdf file. An attacker who successfully exploited the vulnerabilities could cause arbitrary code to execute in the context of the current user. However, an attacker would have no way to force a user to open a specially crafted .pdf file.
MS16-081 – Important
Security Update for Active Directory (3160352)
This security update resolves a vulnerability in Active Directory. The vulnerability could allow denial of service if an authenticated attacker creates multiple machine accounts. To exploit the vulnerability an attacker must have an account that has privileges to join machines to the domain.
MS16-082 – Important
Security Update for Microsoft Windows Search Component (3165270)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow denial of service if an attacker logs on to a target system and runs a specially crafted application.
MS16-083 – Critical
Security Update for Adobe Flash Player (3167685)
This security update resolves vulnerabilities in Adobe Flash Player when installed on all supported editions of Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT 8.1, and Windows 10.
















