Navigating Common Azure Files Issues and Solutions
Azure Files is a cornerstone of modern cloud-based file sharing. As IT professionals dive deeper into its offerings, several challenges may arise. This guide provides an in-depth look into these challenges and elucidates their solutions.
1. Performance Bottlenecks in Azure Files
Azure Files boasts a multitude of performance tiers, but selecting the ideal tier can become a daunting task without proper knowledge.
Solution:
- Benchmarking: Before deploying Azure Files, set benchmarks based on the needs of your application. Monitor these benchmarks against the actual performance metrics. If the two don’t align, reassess your tier selection using insights from the Azure File Storage Performance Tiers.
- Monitoring Tools: Azure Monitor and Azure Storage metrics provide invaluable insights into performance. Set up automated alerts for anomalies that could indicate misconfigurations or the need for a tier upgrade.
- Storage Best Practices: Ensure files and data are structured in a way that maximizes retrieval times. This might involve reorganizing directories or ensuring a balanced distribution of files.
2. Complexities in Setting Up Azure Files
Setting up Azure Files requires a meticulous approach to guarantee optimal functionality.
Solution:
- Guided Tutorials: Relying on comprehensive tutorials ensures that no step is overlooked. The how-to guide for Azure Files provides a detailed setup process.
- Automation: Azure Resource Manager (ARM) templates streamline deployment by allowing for the automation of setups, ensuring consistent configurations across deployments.
- Security Best Practices: Ensure that shared access signatures (SAS) and network security groups (NSG) are appropriately configured to maintain a balance between accessibility and security.
3. Cost Management in Azure Files
Without vigilant management, costs associated with Azure Files can quickly mount.
Solution:
- Regular Clean-ups: Implement a lifecycle management policy. Regularly analyze and remove outdated files, redundant snapshots, and other non-essential data. Tools like Azure Advisor can recommend cost-saving measures.
- Optimize Snapshots: Snapshots, though crucial for data integrity, can inflate costs. Ensure they’re only taken when necessary, and consider automating their retention and deletion. Dive deeper into how you can economize with Azure Files.
- Leverage Reserved Capacity: By predicting your storage needs, you can opt for reserved capacity, which offers cost benefits over pay-as-you-go models.
4. Differentiating Azure Blob Storage from Azure Files
Misunderstanding the distinction between these services can lead to inefficient deployments.
Solution:
- Education: Regular training sessions or workshops can be invaluable. IT professionals should understand the nuances between Azure Blob Storage and Azure File Storage. For instance, while Azure Files offers SMB protocols and is ideal for shared access, Blob Storage is geared towards vast amounts of unstructured data.
- Deployment Strategies: Depending on the use case, Azure Blob Storage might be a more cost-effective solution, especially for large-scale, unstructured data. Ensure the team knows when to leverage each service.
5. Troubleshooting Azure File Sync Issues
Azure File Sync keeps your data consistent across on-premises and cloud environments. However, it can sometimes falter, leading to synchronization issues or data discrepancies.
Solution:
- Sync Agent Updates: Ensure your Azure File Sync agents are up-to-date. Older versions might not only have vulnerabilities but can also lead to compatibility issues. Regularly visit the Azure File Sync guide for the latest updates and best practices.
- Conflict Resolution: Implement a robust conflict resolution strategy. When data is edited in multiple locations simultaneously, conflicts can arise. Azure offers conflict detection, but it’s up to the administrators to decide on resolution strategies.
- Monitoring & Logging: Use Azure Monitor to keep tabs on the sync health. Whenever there’s a hiccup, logs can offer a detailed view of what went wrong, enabling swift resolution.
6. Ensuring Data Security in Azure Files
As with all cloud services, security is paramount. Azure Files is no exception.
Solution:
- Role-Based Access Control (RBAC): Implement RBAC to define who can access what. This ensures that only authorized personnel can view or modify data.
- Encryption: Azure Files offers encryption both in transit and at rest. Always keep these features activated to safeguard your data from prying eyes.
- Audit Trails: Set up logging to keep a record of who accessed what and when. In case of a breach or unexpected modification, these logs can be invaluable in tracing back the events.
7. Managing Azure Storage Accounts Efficiently
Storage accounts are foundational to Azure Files. However, improper management can lead to inefficiencies.
Solution:
- Optimal Storage Type Selection: Depending on your workload, choosing between premium or standard storage can have a significant impact on performance and cost. Learn the specifications and limitations of each through guides like Azure Storage Accounts Size.
- Regular Audits: Periodically review the storage accounts to weed out any inactive or redundant data. Tools such as Azure Storage Explorer can assist in this endeavor.
- Leverage Lifecycle Management: Azure offers lifecycle management policies that automatically transition data to cooler storage or even delete it after a certain period.
8. Efficiently Handling Azure Blobs
Azure Blob Storage, though different from Azure Files, often finds its way into related workflows.
Solution:
- Size Management: Keeping tabs on the size of individual blobs and containers ensures you don’t run into performance issues or unforeseen costs. Tools that provide insights into Azure Blob Container Size and the largest Azure Blobs can be instrumental.
- Blob Tiering: Regularly evaluate and modify blob access tiers. Infrequently accessed data should be moved to cooler tiers, like Azure Blob Cool or Archive, to save on storage costs.
- Data Archival: If certain blobs are no longer necessary but need retention for compliance reasons, consider moving them to Azure Blob Archive tier, which is more cost-effective for long-term storage.
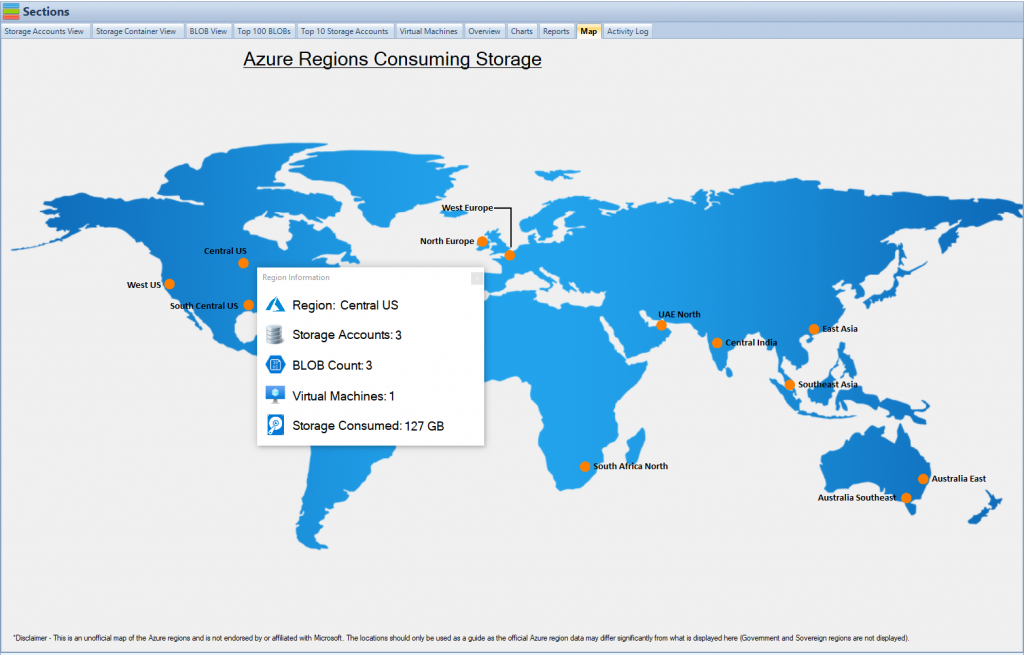
9. Choosing Between Azure Blob Storage and Azure File Storage
When it comes to storing large datasets, professionals often waver between Azure Blob Storage and Azure File Storage. Each has its unique set of strengths.
Solution:
- Understand Use Cases: Azure Blob Storage is optimized for massive, unstructured data. Think videos, backups, or large datasets. Azure File Storage, on the other hand, shines for hierarchical datasets and shared access needs, much like a traditional file system. Evaluate your primary needs using this comparison guide.
- Integration Needs: If your infrastructure leans heavily on applications requiring SMB or NFS protocols, Azure File Storage is the way to go. For web-based applications or analytics, Blob Storage might be more apt.
10. Navigating Azure File Share Permissions
Ensuring secure and appropriate access to Azure File Shares is crucial. Improper configurations can lead to data breaches or operational hiccups.
Solution:
- NTFS Permissions: If migrating from an on-premises file share, your NTFS permissions will remain intact. However, periodically review these permissions to ensure they align with current operational needs.
- Shared Access Signatures (SAS): Use SAS tokens to grant time-bound and specific access to Azure File Shares. They offer a fine-grained control mechanism.
11. Optimizing Costs Across Azure Storage Services
Azure offers multiple storage solutions, and managing costs across them can be a daunting task.
Solution:
- Automate Data Lifecycle: Automate the migration of data between hot, cool, and archive tiers based on data access patterns. Understand how to minimize Azure Blob Storage costs to make informed decisions.
- Monitor and Analyze: Use Azure Cost Management and Billing to keep tabs on your expenditures. Set up alerts for budget thresholds to prevent unforeseen expenses.
- Review Storage Accounts: Regularly revisit your Azure Storage Account configurations to ensure they align with your current and projected needs.
12. Addressing Azure File Share Connectivity Issues
Azure File Share offers seamless connectivity, but sometimes users might experience disruptions.
Solution:
- VPN & ExpressRoute: If accessing Azure File Shares from on-premises, consider setting up an Azure VPN or ExpressRoute for a more reliable and faster connection.
- Troubleshooting Tools: Use tools like Azure Storage Metrics and Logging to diagnose connectivity issues. They provide detailed insights into operations, allowing you to pinpoint disruptions.
13. Ensuring Data Redundancy in Azure Files
Data loss can be catastrophic. Ensuring redundancy is key to data integrity.
Solution:
- Geo-Redundant Storage (GRS): Opt for GRS to maintain copies of your data in different geographical locations. This ensures data availability even if a primary region faces outages.
- Regular Backups: While Azure Files offers built-in redundancy, consider setting up additional regular backups, especially for mission-critical data.
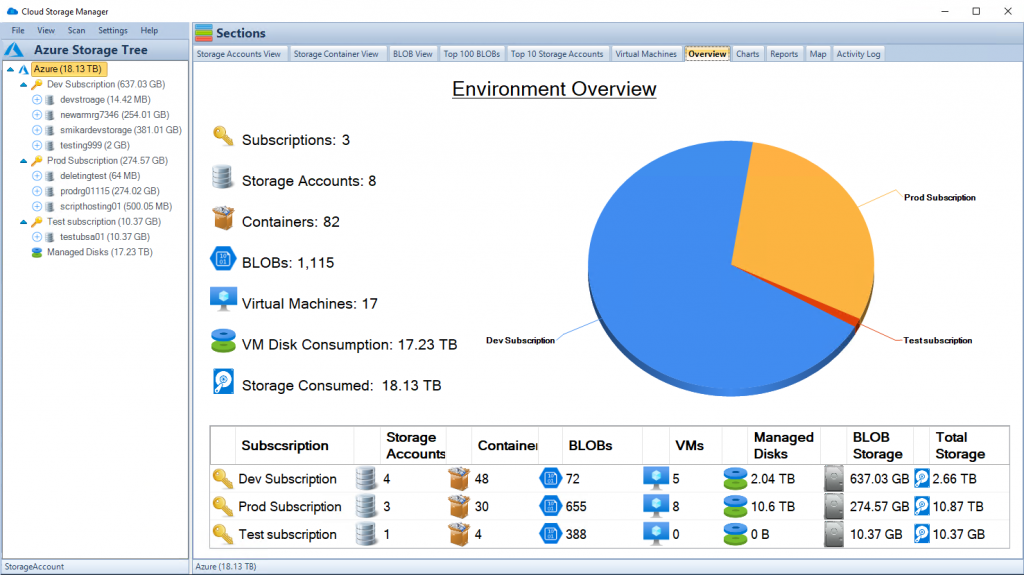
14. Ensuring Compliance and Regulatory Adherence in Azure Files
For businesses operating in regulated industries, compliance is more than a best practice; it’s a mandate.
Solution:
- Data Classification: Use Azure Information Protection to label and classify files based on sensitivity. This ensures the right level of protection is applied to specific data sets.
- Audit Logs & Reporting: Regularly check Azure Activity Logs for any unauthorized or suspicious activity. These logs can be crucial during audits or compliance checks.
- Azure Policy & Blueprints: Use Azure Policy to enforce organizational requirements. Azure Blueprints, on the other hand, allow for the creation of compliant environments, ensuring deployments align with regulatory needs.
15. Scaling Azure File Services Without Downtime
As businesses grow, so do their storage needs. Ensuring scalability without affecting operational uptime is crucial.
Solution:
- Elastic Shares: Elastic shares in Azure Files Premium tier allows for the automatic scaling of IOPS and throughput, ensuring consistent performance even during high-demand periods.
- Storage Account Limits: Be wary of the limits set on Azure storage accounts. Monitor them and consider spreading workloads across multiple accounts if nearing the thresholds.
16. Handling Large-Scale Data Migrations to Azure Files
Migrating massive amounts of data to Azure Files can be time-consuming and might lead to data loss if not done correctly.
Solution:
- Azure Data Box: For terabytes to petabytes of data, consider using Azure Data Box. It’s a secure, tamper-resistant method of transferring large datasets without relying on the network.
- Azure Storage Migration Tools: Tools such as Azure Storage Data Movement Library or AzCopy can accelerate data transfers while ensuring data integrity.
17. Dealing with Data Retrieval Latencies
Delayed data retrieval can affect business operations, leading to inefficiencies.
Solution:
- Optimized Indexing: Ensure data is structured and indexed appropriately. This reduces retrieval times, especially for large datasets.
- Premium Tier Consideration: For workloads requiring high-speed access, consider moving to Azure Files’ premium tier, which offers higher IOPS and lower latencies.
18. Protecting Against Ransomware and Malicious Attacks
The cloud environment isn’t immune to threats. Ensuring data security against ransomware and other attacks is paramount.
Solution:
- Immutable Storage: This feature ensures data cannot be deleted or modified for a set period. It’s an excellent deterrent against ransomware which often seeks to encrypt or delete data.
- Azure Backup and Azure Site Recovery: Regular backups ensure data integrity. In the face of an attack, data can be restored to its pre-attack state using these Azure services.
19. Seamless Integration with On-Premises Solutions
Many businesses operate in hybrid environments. Ensuring Azure Files integrates smoothly with on-premises solutions is essential.
Solution:
- Azure File Sync: This service syncs on-premises file servers with Azure File shares, ensuring a seamless flow of data across environments. Dive deeper with this Azure File Sync guide.
- Hybrid Connections: Azure Relay’s Hybrid Connections can be leveraged for secure, bi-directional integrations with on-premises data and applications.
20. Maintaining Azure File Shares Performance
Like any storage system, performance optimization ensures that your applications and services run smoothly.
Solution:
- Monitor Throughput: Keep a close watch on the IOPS (Input/Output Operations Per Second) and bandwidth. If you notice a drop, you might be nearing your share’s limits. Consider optimizing data or upgrading to a higher performance tier.
- Data Partitioning: Instead of a monolithic storage strategy, partition data into multiple file shares or storage accounts. This can distribute the load and enhance overall performance.
- Refer to Performance Tiers: Azure File Storage offers different performance tiers, each with its benefits. Understand the Azure File Storage Performance Tiers to make informed decisions.
21. Mitigating Azure File Service Downtime
Unplanned outages can affect business operations and result in financial losses.
Solution:
- Availability Zones: Distribute resources across different availability zones. If one zone faces outages, your system can continue functioning using resources from another zone.
- Regular Health Checks: Use Azure Monitor and Azure Health services to consistently check the health of your Azure resources.
22. Managing Costs Effectively
Azure can quickly become expensive if not managed effectively, especially when dealing with vast amounts of data.
Solution:
- Cost Analysis Tools: Use Azure Cost Management and Billing to get insights into your spending patterns. This will help identify areas where costs can be reduced.
- Optimizing Storage: Understand how to save money with Azure Files. Consider strategies such as data deduplication, compression, and choosing the right storage tier.
23. Ensuring Efficient Data Access Across Global Teams
For businesses with a global presence, data access speed and reliability become crucial.
Solution:
- Geo-Replication: Use Azure’s geo-replication features to maintain copies of your data in multiple regions, ensuring fast access for teams across the globe.
- Content Delivery Network (CDN): Integrate Azure Files with Azure CDN to cache data at various points around the world, thus reducing data access latency for global users.
24. Managing Legacy Data in Azure Files
As businesses evolve, they might end up with outdated or legacy data that still needs to be stored and accessed occasionally.
Solution:
- Archive Tier: Move old data that’s rarely accessed to Azure’s Archive Storage Tier. It’s the most cost-effective tier for data that doesn’t need frequent access.
- Data Validation: Periodically review and validate the relevance of data. Tools that highlight Azure blob files not accessed can help identify legacy data that might be ripe for archiving or deletion.
Azure Files offers a wide range of functionalities, but like any tool, its effectiveness hinges on how it’s used. By understanding and proactively addressing these challenges, IT professionals can create a robust, efficient, and cost-effective storage infrastructure. If there are more specific areas or challenges you’d like to address, please inform me.

25. Retrieving Large Azure Blobs Efficiently
As datasets grow, retrieving large blobs becomes a challenge due to longer retrieval times and potential timeouts.
Solution:
- Blob Download Strategies: Use tools such as AzCopy, which supports concurrent and segmented blob downloads, thus speeding up the process. By breaking the blob into chunks and downloading them simultaneously, you can significantly reduce retrieval times.
- Use Insights: Employ tools to find the largest Azure blobs, allowing you to be proactive in managing them, either by partitioning or optimizing them.
26. Managing Azure Blob Container Sizes
As the number of blobs grow, managing them efficiently and ensuring they do not overwhelm the container’s limits becomes crucial.
Solution:
- Monitor Container Limits: Regularly track the size and count of blobs within each container. Ensure they don’t exceed the Azure blob container size limits.
- Optimize and Partition: Consider segregating blobs into multiple containers based on criteria like data type, application, or usage frequency. This ensures better organization and manageability.
27. Simplifying Azure Storage Account Creation
Azure Storage Account is fundamental to using Azure storage services. However, setting it up optimally can sometimes be intricate.
Solution:
- Follow Step-by-Step Guides: Utilize comprehensive guides to create an Azure storage account. These guides provide a detailed walk-through, ensuring you configure settings tailored to your needs.
- Automate with Templates: For repeated deployments, use Azure Resource Manager templates to automate storage account creation with desired configurations.
28. Ensuring Data Security in Transit and at Rest
Data breaches can lead to significant losses both in terms of reputation and financial implications.
Solution:
- Encryption: Use Azure’s built-in encryption services, which encrypt data both in transit (using SSL/TLS) and at rest (using Azure Storage Service Encryption).
- Access Control: Regularly review and update shared access signatures and role-based access controls. This ensures only authorized individuals can access the data.
29. Optimizing Queries on Azure File Datasets
For businesses using Azure Files as a part of analytics or data processing workflows, efficient querying becomes essential.
Solution:
- Structured Data: When possible, structure your data in a way that’s optimized for your query patterns. This might include partitioning, indexing, or denormalizing data.
- Leverage Azure Tools: Tools like Azure Data Lake Storage and Azure Data Explorer can be integrated with Azure Files to provide more efficient query capabilities on large datasets.
Azure Files, as a versatile cloud storage solution, can effectively cater to a myriad of storage needs. However, to harness its full potential, one must continuously adapt to the challenges that emerge as data scales and business needs evolve. Should you want further insights on any other challenges or details, please let me know.
Conclusion
Azure Files is undeniably a cornerstone for many businesses venturing into the cloud, offering scalability, flexibility, and a robust set of features. But like any technology, it presents its own set of challenges. Addressing these challenges isn’t merely about troubleshooting; it’s about strategizing, anticipating, and being proactive.
From ensuring top-notch data security to optimizing performance and managing costs, the spectrum of potential issues is wide. However, as illustrated in this comprehensive guide, solutions are readily available. By leveraging Azure’s extensive toolkit and staying informed about best practices, IT professionals can not only navigate these challenges with ease but also optimize their Azure experience.
In a constantly evolving digital landscape, the true potential of Azure Files is realized by those who understand its intricacies and are equipped to tackle the challenges head-on. Stay updated, stay informed, and let Azure propel your business to new heights.
For more in-depth insights on specific Azure aspects and tools, do explore the provided links throughout this guide. Here’s to seamless cloud storage experiences with Azure Files!