by Mark | Aug 18, 2016 | Deployment, Errors, Fixes, Security
Microsoft August Patch Tuesday Release Causes Printing Issues: How to Fix it
Are you experiencing printing problems on your Windows PC after installing the latest security updates from Microsoft? If yes, then you are not alone. Two recent patches released by Microsoft, KB3177725 and KB3176493, seem to be causing printing issues on multiple Windows versions. In this article, we will discuss the details of this issue and how to fix it.
What are KB3177725 and KB3176493?
KB3177725 and KB3176493 are two security updates released by Microsoft in its August Patch Tuesday Release. These updates were designed to patch security vulnerabilities that could allow remote code execution on Windows 7, 8, 8.1, 10, and server editions of their software, including Windows server 2008, 2008 R2, 2012, and 2012 R2.

What is the issue caused by these updates?
The issue caused by these updates is the inability to print more than one page at a time. Some users have reported that it corrupts all print jobs with an error. Initially, Microsoft claimed that the problem was due to incompatibility issues between Windows and Printer Drivers. However, the company later acknowledged that the issue was caused by these two updates.

What is the fix for this issue?
UPDATE: Previously we mentioned the only work around is to uninstall either or both KB3177725 and KB3176493.
Well Microsoft have come through and have released another patch that will fix the issues caused by these two security updates. KB3187022 – Print functionality is broken after any of the MS16-098 security updates are installed
Patch is available to download from the Microsoft site https://support.microsoft.com/en-us/kb/3187022
There has been other issues this month, caused by the August Security Patches. Microsoft Patch KB3179575 causing authentication issues with Windows 2012 servers and KB3176934 breaks Windows 10 Powershell
If you are a SnaPatch customer, you are in luck. SnaPatch allows you to quickly and easily roll back your virtual machines to the prior security update deployment snapshot, thereby avoiding further issues. To learn more about what SnaPatch offers and how it can help you avoid similar issues, click the link provided.
In conclusion, if you are experiencing printing issues on your Windows PC after installing the latest security updates from Microsoft, then you are not alone. The patches causing these problems are KB3177725 and KB3176493. However, Microsoft has released a fix for this issue in the form of KB3187022. We recommend that you download and install this patch to resolve the issue.

by Mark | Aug 11, 2016 | Fixes, Patch Management, Patch Releases, SCCM, Security
MICROSOFT’S August 2016 PATCH RELEASES
The following nine Patch Tuesday updates / patches have been released by Microsoft for the August 2016 Update deployment.
Are you ready to start deploying and remove the patching risk using SnaPatch Patch Management Software?
MS16-095 – Critical
Cumulative Security Update for Internet Explorer (3177356)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-096 – Critical
Cumulative Security Update for Microsoft Edge (3177358)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than users with administrative user rights.
MS16-097 – Critical
Security Update for Microsoft Graphics Component (3177393)
This security update resolves vulnerabilities in Microsoft Windows, Microsoft Office, Skype for Business, and Microsoft Lync. The vulnerabilities could allow remote code execution if a user either visits a specially crafted website or opens a specially crafted document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS16-098– Critical
Security Update for Windows Kernel-Mode Drivers (3178466)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application that could exploit the vulnerabilities and take control of an affected system.
MS16-099 – Critical
Security Update for Microsoft Office (3177451)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS16-100 – Important
Security Update for Secure Boot (3179577)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow security feature bypass if an attacker installs an affected boot manager and bypasses Windows security features.
MS16-101 – Important
Security Update for Windows Authentication Methods (3178465)
This security update resolves multiple vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow elevation of privilege if an attacker runs a specially crafted application on a domain-joined system.
MS16-102 – Critical
Security Update for Microsoft Windows PDF Library (3182248)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user views specially crafted PDF content online or opens a specially crafted PDF document. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
MS16-103– Important
Security Update for ActiveSyncProvider (3182332)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow information disclosure when Universal Outlook fails to establish a secure connection.

by Mark | Jul 12, 2016 | Errors, Fixes, How To, VMWare
VMWare PowerCLI Installation Failed
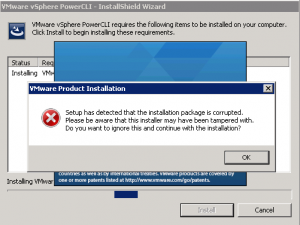
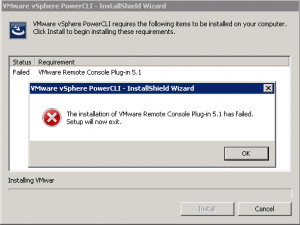
If you are installing VMWare’s PowerCLI for remote administration of your VMWare farm, or for SnaPatch or Snapshot Master you may at times receive the following error, “Setup has detected that the installation package is corrupted. Please be aware that this installer may have been tampered with.” One of the possible causes for this is that the root certificate for VeriSign isnt installed on your computer. There are a few ways to fix this issue, one is to download the root certificate from VeriSign themselves and then to install it to the local computer account under Third-Party Root Certification Authorities-Certificates, or to export it from the VMWare PowerCLI installation package.
VMWare PowerCLI setup error
These screenshots show the error you would receive while trying to install the VMWare PowerCLI installer.
How to Manually install the root certificate
First off we will see if the root certificate is in fact already installed or not. From a command prompt type mmc.exe to open up the Microsoft Management Console.
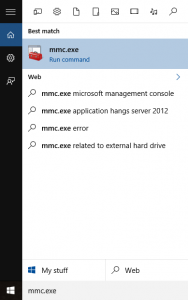
Now go to File, then Add/Remove Snap-in
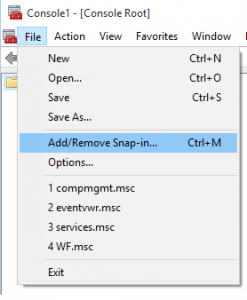
Next we have to choose the Certificates addin. Highlight Certificates then click on Add.
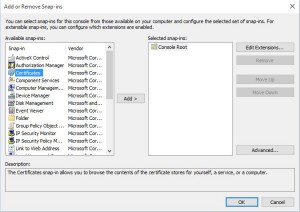
You will now need to select Computer Account and then click Next.
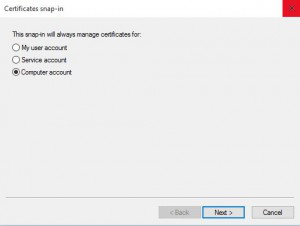
Choose Local Computer for the location that this snap-in will manage then click Next.
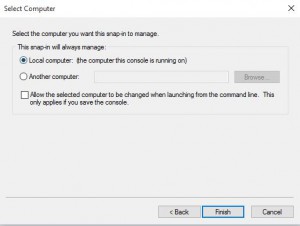
Now click OK and the Certificates Snap-in will be available.
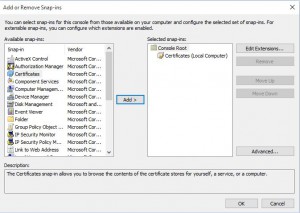
Expand Certificates, then Third-Party Root Certification Authorities and finally Certificates. You will now need to look for the Root Certificate, VeriSign Class 3 Public Primary Certification Authority – G5. In this example you can see that the certificate is installed. If it isnt installed you can download and install the certificate to the shown location. If you cannot download the root certificate it is possible to import the certificate from the VMWare PowerCLI installation package, as shown in further steps.
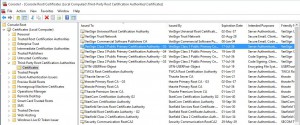
How to import the certificate from the VMWare package
Now you will need to export the Root Certificate from the VMWare PowerCLI installation package. To do so, locate the EXE file and right click it then choose properties.
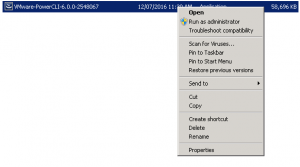
Change the tab to Digital Signatures then click Details.
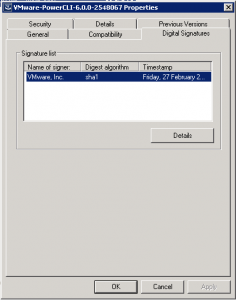
As you can see in this example, “the certificate in the signature cannot be verified”. Click View Certificate to proceed.
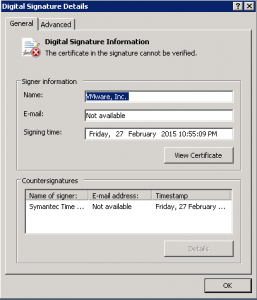
Change to the Certification Path tab and make sure you select the top of the certification path. In this example, you can see it highlighted as VeriSign Class 3 Public Primary Certification Authority – G5. Once selected click View Certificate.
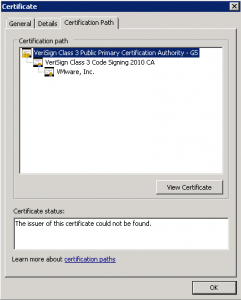
Again, in the next window go to the Details tab then click Copy to File.
The Certificate Export Wizard starts next. Click on Next to proceed with the Wizard.
Leave the Format as DER and then click on Next.
Choose the location and filename where you want to save the exported certificate and then click Next.
You can now click Finished and the Certificate Export Wizard will then close.
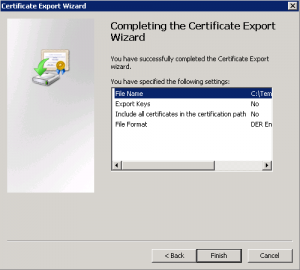
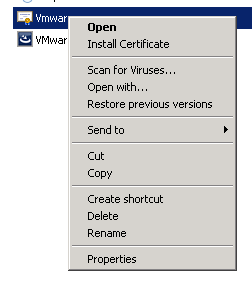
Next we need to import the VeriSign Root Certificate to the correct location. Right click the exported certificate and select Install Certificate.
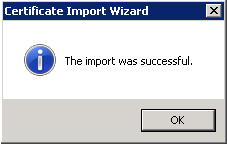
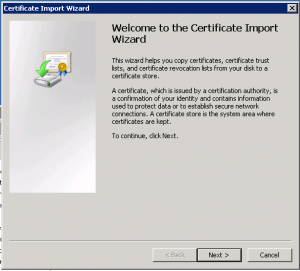
The Certificate Import Wizard now starts. Click Next.
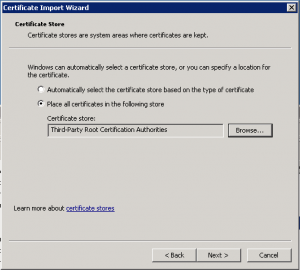
Select Place all certificates in the following store and then choose Third-Party Root Certification Authorities. Click Next when ready to do so.
Now click Finish.
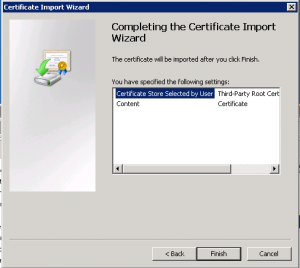
The Root Certificate from VeriSign should now have installed in to the correct location and you can then restart the installation of VMWare PowerCLI.