by Mark | May 30, 2023 | Azure, Azure Blobs, Azure Disks, Azure FIles, Azure Queues, Azure Tables, Blob Storage, Cloud Storage, Cloud Storage Manager, Storage Accounts
Azure Storage SAS Tokens
Azure Storage offers a robust set of data storage solutions including Blob Storage, Queue Storage, Table Storage, and Azure Files. A critical component of these services is the Shared Access Signature (SAS), a secure way to provide granular access to Azure Storage services. This article explores the intricacies of Azure Storage SAS Tokens.
Introduction to Azure Storage SAS Tokens
Azure Storage SAS tokens are essentially strings that allow access to Azure Storage services in a secure manner. They are a type of URI (Uniform Resource Identifier) that offer specific access rights to Azure Storage resources. They are a pivotal part of Azure Storage and are necessary for most tasks that require specific access permissions.
Types of SAS Tokens
There are different types of SAS tokens, each serving a specific function.
Service SAS
A Service SAS (Shared Access Signature) is a security token that grants limited access permissions to specific resources within a storage account. It is commonly used in Microsoft Azure’s storage services, such as Azure Blob Storage, Azure File Storage, and Azure Queue Storage.
A Service SAS allows you to delegate access to your storage resources to clients without sharing your account access keys. It is a secure way to control and restrict the operations that can be performed on your storage resources by specifying the allowed permissions, the time duration for which the token is valid, and the IP addresses or ranges from which the requests can originate.
By generating a Service SAS, you can provide temporary access to clients or applications, allowing them to perform specific actions like reading, writing, or deleting data within the specified resource. This approach helps enhance security by reducing the exposure of your storage account’s primary access keys.
Service SAS tokens can be generated using the Azure portal, Azure CLI (Command-Line Interface), Azure PowerShell, or programmatically using Azure Storage SDKs (Software Development Kits) in various programming languages.
It’s important to note that a Service SAS is different from an Account SAS. While a Service SAS grants access to a specific resource, an Account SAS provides access to multiple resources within a storage account.
Account SAS
An Account SAS (Shared Access Signature) is a security token that provides delegated access to multiple resources within a storage account. It is commonly used in Microsoft Azure’s storage services, such as Azure Blob Storage, Azure File Storage, and Azure Queue Storage.
Unlike a Service SAS, which grants access to specific resources, an Account SAS provides access at the storage account level. It allows you to delegate limited permissions to clients or applications to perform operations across multiple resources within the storage account, such as reading, writing, deleting, or listing blobs, files, or queues.
By generating an Account SAS, you can specify the allowed permissions, the time duration for which the token is valid, and the IP addresses or ranges from which the requests can originate. This allows you to control and restrict the actions that can be performed on the storage account’s resources, while still maintaining security by not sharing your account access keys.
Account SAS tokens can be generated using the Azure portal, Azure CLI (Command-Line Interface), Azure PowerShell, or programmatically using Azure Storage SDKs (Software Development Kits) in various programming languages.
It’s worth noting that an Account SAS has a wider scope than a Service SAS, as it provides access to multiple resources within the storage account. However, it also carries more responsibility since a compromised Account SAS token could potentially grant unauthorized access to all resources within the account.
Ad hoc SAS
Ad Hoc SAS (Shared Access Signature) refers to a dynamically generated SAS token that provides temporary and limited access to specific resources. Unlike a regular SAS token, which is typically created and configured in advance, an Ad Hoc SAS is generated on-demand and for a specific purpose.
The term “ad hoc” implies that the SAS token is created as needed, usually for short-term access requirements or specific scenarios where immediate access is necessary. It allows you to grant time-limited permissions to clients or applications for performing certain operations on designated resources within a storage account.
Ad Hoc SAS tokens can be generated using the appropriate APIs, SDKs, or command-line tools provided by the cloud storage service. When generating an Ad Hoc SAS, you specify the desired permissions, expiration duration, and optionally other restrictions such as IP addresses or protocol requirements.
The flexibility of Ad Hoc SAS tokens makes them particularly useful when you need to grant temporary access to resources without the need for long-term keys or complex authorization mechanisms. Once the token expires, the access granted by the SAS token is no longer valid, reducing the risk of unauthorized access.
Working of SAS Tokens
A SAS token works by appending a special set of query parameters to the URI that points to a storage resource. One of these parameters is a signature, created using the SAS parameters and signed with the key used to create the SAS. Azure Storage uses this signature to authorize access to the storage resource
SAS Signature and Authorization
In the context of Azure services, a SAS token refers to a Shared Access Signature token. SAS tokens are used to grant limited and time-limited access to specified resources or operations within an Azure service, such as storage accounts, blobs, queues, or event hubs.
When you generate a SAS token, you define the permissions and restrictions for the token, specifying what operations can be performed and the duration of the token’s validity. This allows you to grant temporary access to clients or applications without sharing your account’s primary access keys or credentials.
SAS tokens consist of a string of characters that include a signature, which is generated using your account’s access key and the specified permissions and restrictions. The token also includes other information like the start and expiry time of the token, the resource it provides access to, and any additional parameters you define.
By providing a client or application with a SAS token, you enable them to access the designated resources or perform specific operations within the authorized time frame. Once the token expires, the access is no longer valid, and the client or application would need a new token to access the resources again.
SAS tokens offer a secure and controlled way to delegate limited access to Azure resources, ensuring fine-grained access control and minimizing the exposure of sensitive account credentials.
What is a SAS Token
A SAS token is a string generated on the client side, often with one of the Azure Storage client libraries. It is not tracked by Azure Storage, and one can create an unlimited number of SAS tokens. When the client application provides the SAS URI to Azure Storage as part of a request, the service checks the SAS parameters and the signature to verify its validity
When to Use a SAS Token
SAS tokens are crucial when you need to provide secure access to resources in your storage account to a client who does not have permissions to those resources. They are commonly used in a scenario where usersread and write their own data to your storage account. In such cases, there are two typical design patterns:
- Clients upload and download data via a front-end proxy service, which performs authentication. While this allows for the validation of business rules, it can be expensive or difficult to scale, especially for large amounts of data or high-volume transactions.
- A lightweight service authenticates the client as needed and then generates a SAS. Once the client application receives the SAS, it can directly access storage account resources. The SAS defines the access permissions and the interval for which they are allowed, reducing the need for routing all data through the front-end proxy service.
A SAS is also required to authorize access to the source object in a copy operation in certain scenarios, such as when copying a blob to another blob that resides in a different storage account, or when copying a file to another file in a different storage account. You can also use a SAS to authorize access to the destination blob or file in these scenarios
Best Practices When Using SAS Tokens
Using shared access signatures in your applications comes with potential risks, such as the leakage of a SAS that can compromise your storage account, or the expiration of a SAS that may hinder your application’s functionality. Here are some best practices to mitigate these risks:
- Always use HTTPS to create or distribute a SAS to prevent interception and potential misuse.
- Use a User Delegation SAS when possible, as it provides superior security to a Service SAS or an Account SAS.
- Have a revocation plan in place for a SAS to respond quickly if a SAS is compromised.
- Configure a SAS expiration policy for the storage account to specify a recommended interval over which the SAS is valid.
- Create a Stored Access Policy for a Service SAS, which allows you to revoke permissions for a Service SAS without regenerating the storage account keys.
- Use near-term expiration times on an Ad hoc SAS, so even if a SAS is compromised, it’s valid only for a short time
Conclusion
In conclusion, Azure Storage SAS Tokens play a vital role in providing secure, granular access to Azure Storage services. Understanding the different types of SAS tokens, how they work, and best practices for their use is critical for managing access to your storage account resources effectively and securely.
Frequently Asked Questions
| FAQs |
Answers |
| 1 |
What is a Shared Access Signature (SAS)? |
A SAS is a signed URI that points to one or more storage resources. The URI includes a token that contains a special set of query parameters. The token indicates how the resources may be accessed by the client |
| 2 |
What are the types of SAS? |
There are three types of SAS: Service SAS, Account SAS, and User Delegation SAS. Service and Account SAS are secured with the storage account key. User Delegation SAS is secured with Azure AD credentials |
| 3 |
How does a SAS work? |
A SAS works by including a special set of query parameters in the URI, which indicate how the resources may be accessed. When a request includes a SAS token, that request is authorized based on how that SAS token is signed. The access key or credentials that you use to create a SAS token are also used by Azure Storage to grant access to a client that possesses the SAS |
| 4 |
When should I use a SAS? |
Use a SAS to give secure access to resources in your storage account to any client who does not otherwise have permissions to those resources. It’s particularly useful in scenarios where clients need to read and write their own data to your storage account and when copying a blob to another blob, a file to another file, or a blob to a file |
| 5 |
What are the best practices when using SAS? |
Always use HTTPS to create or distribute a SAS, use a user delegation SAS when possible, have a revocation plan in place, configure a SAS expiration policy for the storage account, create a stored access policy for a service SAS, and use near-term expiration times on an ad hoc SAS service SAS or account SAS |

by Mark | May 29, 2023 | Azure, Carbon, Cloud Computing, Deployment, HyperV, Microsoft HyperV, VMWare
The rapid technological advancements in the last decade led to a massive migration of data and applications from on-premise environments to the cloud. While this cloud migration trend dominated the IT world, a recent paradigm shift has emerged that’s moving in the opposite direction – ‘Cloud Reverse Migration’ or ‘Cloud Repatriation’. This burgeoning movement towards cloud repatriation has piqued the interest of many, prompting a need for a comprehensive exploration of this concept, its driving factors, and the tools that facilitate it.
Understanding Cloud Reverse Migration
Cloud Reverse Migration, also known as Cloud Repatriation, is the strategic move of transferring digital data, operations, applications, or services from a cloud environment back to its original on-premise location or to an alternate private data center. Contrary to some misconceptions, this migration process does not denote the failure of cloud computing; instead, it is a strategic response to the evolving needs of businesses and a reflection of the realization that not all workloads are suited for the cloud.
The Rising Trend of Cloud Repatriation
While the benefits of cloud computing – flexibility, scalability, and cost savings, to name a few – remain valid and significant, an increasing number of businesses are reconsidering their digital strategies and migrating their operations back on-premises. This trend, known as Cloud Repatriation, is becoming increasingly prevalent across different sectors for a multitude of reasons.
Reasons for Cloud Reverse Migration
Financial Considerations
At first glance, cloud services may appear to be a more cost-efficient alternative due to the reduced upfront costs and the promise of predictable recurring expenses. However, the reality is often more complicated. The ongoing costs of cloud services, which include data transfer fees and charges for additional services, can accumulate rapidly, turning what initially seemed like a cost-saving move into a financial burden. For some businesses, investing in and maintaining in-house infrastructure can be more cost-effective over the long term.
Data Security and Control
With data breaches and cyberattacks becoming more sophisticated and commonplace, organizations are increasingly concerned about their data’s security. While cloud service providers have robust security measures in place, storing sensitive data off-premises often results in companies feeling they have less control over their data protection strategies. By migrating data back on-premise, organizations can regain control and implement security measures tailored to their unique requirements.
Performance and Latency Issues
Despite the cloud’s advantages, certain applications, particularly those requiring real-time data processing and low latency, can face performance issues in a cloud environment. Factors such as network congestion, physical distance from the data center, and shared resources can result in slower response times. As such, for applications where speed is paramount, on-premises solutions often prove superior.
Compliance and Regulatory Concerns
Certain industries, such as healthcare and finance, are subject to strict data management regulations. These industries often need to keep their data on-premises to comply with data sovereignty laws and privacy regulations. In such cases, cloud reverse migration becomes a necessary step towards ensuring compliance and avoiding hefty penalties.

Carbon: Your Reliable Partner for Cloud Reverse Migration
When it comes to facilitating the cloud repatriation process, the right tools can make a world of difference. Carbon, a software tool developed by SmiKar, is specifically designed to streamline the process of migrating Azure Virtual Machines (VMs) back to an on-premise environment, either on VMware or Hyper-V. With its user-friendly interface and impressive features, Carbon simplifies what could otherwise be a complex process.
Comprehensive VM Management
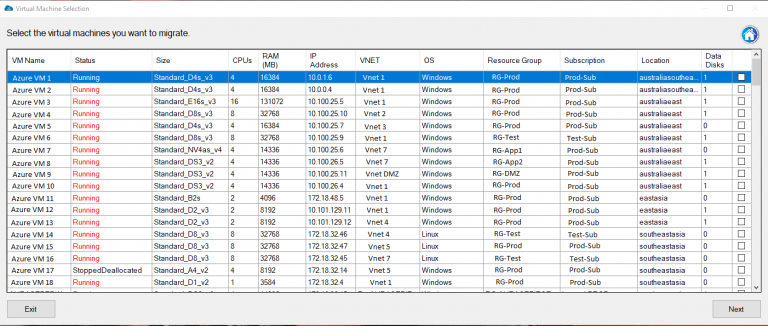
Carbon’s comprehensive VM management is one of its key features. With Carbon, users gain a detailed understanding of their Azure VMs – including VM name, status, size, number of CPUs, memory allocation, IP address, VNET, operating system, resource group, subscription name, location, and more. This detailed information aids users in making informed decisions about which VMs to migrate and how best to configure them in their on-premise environment.
Easy Migration and Conversion Process
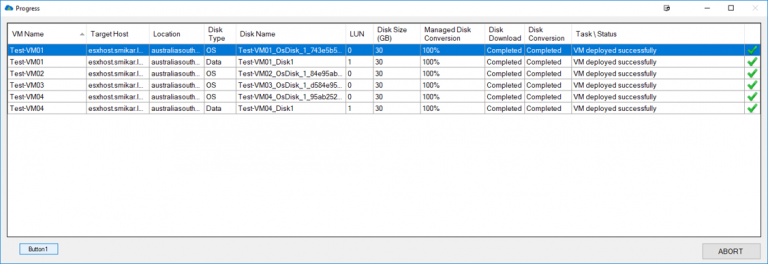
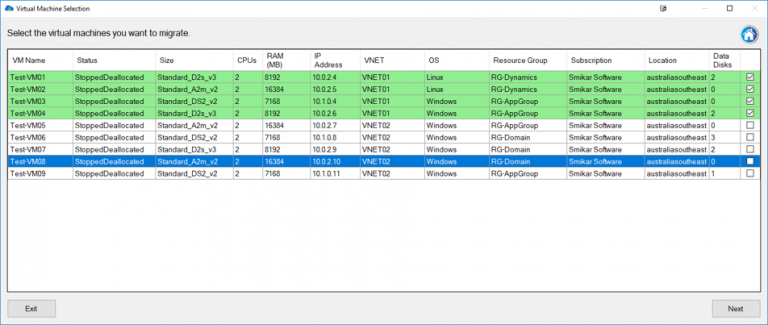
One of Carbon’s greatest strengths is its ability to simplify the migration and conversion process. By integrating seamlessly with VMware or Hyper-V environments, Carbon enables users to replicate and convert their Azure VMs to their chosen on-premise hypervisor with just a few clicks. The software sets up replicated Azure VMs with the same CPU, memory, and disk configurations, ensuring a smooth transition back to the on-premise environment.
Automatic Configuration and Email Notifications
To help users stay informed about the progress of their migration, Carbon offers automatic configuration and email notifications. These notifications can alert users to any changes in their VMs’ status, allowing them to monitor the migration process more effectively.
Customizable User Interface
Recognizing that each user has unique preferences, Carbon provides a customizable interface that allows users to adjust settings to suit their needs. Whether users prefer a particular hypervisor, datastore, or Azure subscription, Carbon offers the flexibility to accommodate these preferences, making the migration process as straightforward and user-friendly as possible.
How Carbon Streamlines Cloud Reverse Migration
Carbon’s streamlined process for migrating Azure VMs back to on-premise infrastructure has brought ease and simplicity to a typically complex task. By providing detailed VM information, an easy-to-navigate migration process, automatic configuration, and email notifications, along with a customizable interface, Carbon enables businesses to execute a smooth and successful cloud reverse migration.
Conclusion
Cloud reverse migration is a growing trend among businesses seeking to address cloud computing’s limitations. Whether driven by financial considerations, data security and control concerns, performance issues, or regulatory compliance, the move towards cloud repatriation has become an increasingly viable option for many organizations. With tools like SmiKar’s Carbon, this process is made significantly more manageable, providing businesses with a path to successfully navigate their journey back to on-premise infrastructure.
Reverse Cloud Migration FAQs
| Number |
Question |
Answer |
| 1 |
What is Cloud Reverse Migration? |
Cloud Reverse Migration, also known as Cloud Repatriation, is the process of moving data, operations, applications, or services from a cloud environment back to its original on-premise location or to a private data center. |
| 2 |
Why are businesses opting for Cloud Repatriation? |
Businesses are opting for Cloud Repatriation for several reasons. These can include financial considerations, data security and control, performance and latency issues, and regulatory compliance concerns. |
| 3 |
What are some common issues businesses face with cloud-based solutions? |
Common issues include unexpected costs, lack of control over data security, performance issues especially with applications that require real-time data processing and low latency, and compliance issues in industries with strict data regulations. |
| 4 |
How can Cloud Reverse Migration address these issues? |
Cloud Reverse Migration allows businesses to regain control over their data, potentially reduce costs, improve application performance, and ensure compliance with industry regulations. |
| 5 |
What is Carbon and how does it support Cloud Reverse Migration? |
Carbon is a reverse cloud migration tool. It streamlines the process of migrating Azure Virtual Machines (VMs) back to an on-premise environment, either on VMware or Hyper-V. It offers comprehensive VM management, easy migration and conversion, automatic configuration and email notifications, and a customizable user interface. |
| 6 |
What are the key features of Carbon for cloud reverse migration? |
Key features of Carbon include comprehensive VM management, simplified migration and conversion process, automatic configuration and email notifications, and a customizable user interface to adjust settings to user preferences. |
| 7 |
How does Carbon ease the process of cloud reverse migration? |
Carbon eases the process of cloud reverse migration by offering a detailed view of Azure VMs, enabling seamless migration and conversion, providing automatic notifications about the migration process, and allowing users to customize the software to their preferences. |
| 8 |
What types of businesses can benefit from using Carbon for Cloud Reverse Migration? |
Businesses of all sizes and across various sectors can benefit from Carbon, especially those looking to move their Azure VMs back to on-premise environments due to financial, security, performance, or compliance reasons. |
| 9 |
How does Carbon ensure a seamless transition from the cloud to on-premise environments? |
Carbon ensures a seamless transition by integrating with your on-premise VMware or Hyper-V environments. It replicates and converts Azure VMs to the chosen on-premise hypervisor, maintaining the same CPU, memory, and disk configurations. |
| 10 |
Can Carbon assist in managing costs during Cloud Reverse Migration? |
By providing comprehensive details about Azure VMs and offering a simplified migration process, Carbon can help businesses make informed decisions, potentially helping to manage costs associated with Cloud Reverse Migration. |

by Mark | May 25, 2023 | Azure, Azure FIles, Cloud Storage, Cloud Storage Manager, Storage Accounts
Your Key to Fortifying Data Storage and Accessibility in 2023
In the ever-evolving landscape of cloud computing, data redundancy is no longer just an option but a must-have feature for any business looking to fortify its data storage and accessibility. One of the most recent additions to the world of data redundancy is Azure Files’ Geo-Redundancy feature, a 2023 release that’s set to take the world of cloud storage by storm.
What is Azure Files Geo-Redundancy?
To understand Azure Files Geo-Redundancy, let’s first delve into the basics. Azure Files is a managed file share service provided by Microsoft Azure, offering secure and highly available network file shares accessible via the Server Message Block (SMB) protocol. Geo-Redundancy, on the other hand, refers to the replication of data across different geographical regions for the purpose of data protection and disaster recovery.
Azure Files Geo-Redundancy allows for multiple copies of your storage account data to be maintained, ensuring high durability and availability. If your primary region becomes unavailable for any reason, an account failover can be initiated to the secondary region, allowing for seamless business continuity.
GRS and GZRS: Enhancing Your Data Redundancy
Azure Files Geo-Redundancy offers two types of storage options, each with its unique advantages. Geo-Redundant Storage (GRS) makes three synchronous copies of your data within a single physical location in the primary region, and then makes an asynchronous copy to a single physical location in the secondary region. On the other hand, Geo-Zone-Redundant Storage (GZRS) copies your data synchronously across three Azure availability zones in the primary region before making an asynchronous copy to a physical location in the secondary region.
One important distinction to note is that Azure Files does not support read-access geo-redundant storage (RA-GRS) or read-access geo-zone-redundant storage (RA-GZRS). Consequently, the file shares won’t be accessible in the secondary region unless a failover occurs.
Boosting Performance and Capacity with Large File Shares
Another standout feature of Azure Files Geo-Redundancy is its ability to support large file shares. When enabled in conjunction with GRS and GZRS, the capacity per share can increase up to 100 TiB – a whopping 20 times increase from the previous limit of 5 TiB. Additionally, maximum IOPS per share can reach up to 20,000 IOPS, and the maximum throughput per share can reach up to 300 MiB/s. These enhancements significantly improve the performance of your file shares, making them more suitable for data-intensive applications and workloads
Where is Azure Files Geo-Redundancy Available?
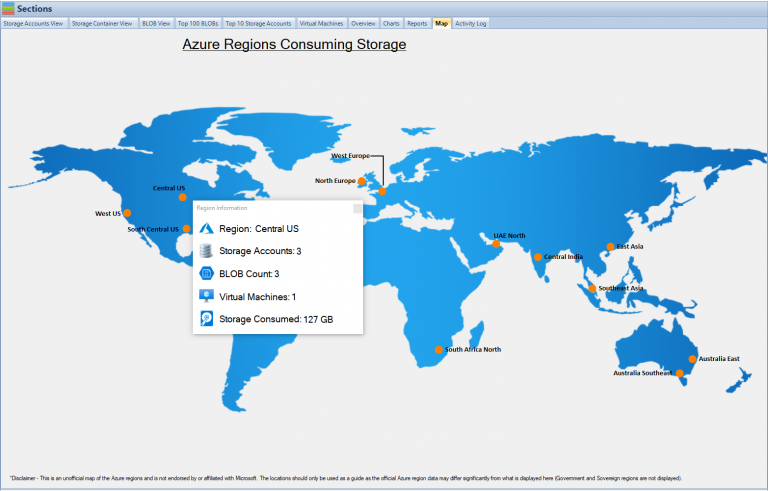
As of 2023, Azure Files Geo-Redundancy for large file shares is available in a wide range of regions, including multiple locations in Australia, China, France, Germany, Japan, Korea, South Africa, Sweden, the United Arab Emirates, the United Kingdom, and the United States. This extensive coverage provides businesses with the flexibility to choose the most appropriate locations for their data storage based on their specific needs and compliance requirements
Getting Started with Azure Files Geo-Redundancy
Ready to fortify your data storage with Azure Files Geo-Redundancy? The registration process is simple and can be done via the Azure portal or PowerShell. Once you’re registered, you can easily enable geo-redundancy and large file shares for new and existing standard SMB file shares
The Snapshot and Sync Mechanism
To ensure consistency of file shares when a failover occurs, Azure creates a system snapshot in the primary region every 15 minutes, which is then replicated to the secondary region. The Last Sync Time (LST) property on the storage account indicates the last time data from the primary region was successfully written to the secondary region. However, due to potential geo-lag or other issues, the latest system snapshot in the secondary region might be older than 15 minutes. It’s also important to note that the Last Sync Time isn’t updated if no changes have been made on the storage account, and its calculation can time out if the number of file shares exceeds 100 per storage account
Considerations for Failover
When planning for a failover, there are a few key considerations to keep in mind. Firstly, a failover will be blocked if a system snapshot doesn’t exist in the secondary region. Secondly, file handles and leases aren’t retained on failover, requiring clients to unmount and remount the file shares. Lastly, the file share quota might change after failover as it’s based on the quota that was configured when the system snapshot was taken in the primary region
Practical Use Cases
Azure Files Geo-Redundancy offers myriad benefits that apply to various business scenarios. For organizations dealing with large datasets, the enhanced capacity and performance limits with large file shares can significantly improve their data management capabilities. Companies operating in multiple geographical locations can also benefit from the wide regional availability of the service, allowing them to maintain data proximity and potentially meet certain compliance and regulatory requirements.
Azure Files Geo-Redundancy is a promising new addition to the world of cloud storage, providing businesses with an effective tool to enhance their data redundancy and resilience. With its robust features and capabilities, it’s set to pave the way for more secure, reliable, and efficient data storage in the cloud.
So, whether you’re a small business looking to safeguard your data or a large enterprise aiming to optimize your data infrastructure, Azure Files Geo-Redundancy is a feature worth exploring. Its potential to enhance data storage, accessibility, and redundancy makes it a game-changing solution in the ever-evolving landscape of cloud computing.
Conclusion
Azure Files’ new geo-redundancy feature further enhances the utility of Cloud Storage Manager, a tool that can help users manage their Azure file shares efficiently and cost-effectively. As a fully managed cloud-native file sharing service, Azure Files is designed to be always on and accessible via the standard Server Message Block (SMB) protocol. However, native file share management is an area where it lacks. This is where Cloud Storage Manager shines, providing the necessary tools and interfaces to manage your Azure Files storage with ease. Thus, with the addition of geo-redundancy to Azure Files, Cloud Storage Manager becomes an even more invaluable tool in managing the increased complexity and unlocking the potential cost savings that come with larger, geo-redundant file shares.
In the digital era, data is a business’s most valuable asset. The ability to protect and access that data, especially during unexpected events, is critical. This is where Azure Files Geo-Redundancy shines, offering businesses a robust and flexible solution to secure their data and ensure its availability across different geographical regions. As we move forward, we can only expect Azure Files Geo-Redundancy to become an even more integral part of businesses’ data management strategies, setting the standard for high availability, durability, and security in cloud storage.

by Mark | May 24, 2023 | Azure, Carbon, HyperV, IAAS, Microsoft HyperV, VMWare
Understanding Cloud Repatriation
In the modern digital age, the migration of data and applications to the cloud has been a significant trend, prompted by the promise of increased efficiency, scalability, and reduced IT costs. Cloud services such as Microsoft’s Azure Cloud have become increasingly popular, offering a host of services including computing power, storage solutions, and advanced analytics. But as with any technology, the cloud has its limitations, and businesses are beginning to realize that not all applications and workloads are suited to the cloud environment. This has given rise to a new trend – cloud repatriation.
Cloud repatriation, sometimes referred to as de-clouding, is the process of moving workloads and data back from the cloud to on-premise or local data centers. While it may seem counter-intuitive in the age of digital transformation, many businesses are finding it a necessary step to maintain control over their data, reduce costs, and overcome performance issues associated with the cloud. This process of migrating back to an on-premise environment from Azure Cloud is what we refer to as Azure Cloud Repatriation.
The concept of Cloud Repatriation
Cloud repatriation is not a new phenomenon but has gained significant attention recently. The initial appeal of the cloud was undeniable, with its promise of unlimited scalability, reduced hardware costs, and access to advanced technologies. However, as businesses dived into the cloud, certain issues began to surface. Some companies found their cloud expenditures spiraling out of control, while others discovered that their specific workloads didn’t perform as well in the cloud as they did on-premise. Then there were issues related to compliance and data sovereignty.
All these factors combined, led businesses to rethink their cloud strategies and consider the option of cloud repatriation. But why are businesses considering cloud repatriation, you might ask? Well, there are several factors at play here. Cost considerations, the need for greater control, security concerns, and performance issues are some of the leading drivers for businesses to move their workloads back on-premise. However, the process of repatriation is not straightforward.
There are several challenges that businesses need to overcome. It requires careful planning, selecting which workloads to move, preparing the on-premise environment, and actually moving the data and applications. It’s not just a simple case of ‘lifting and shifting’. It involves considerable time and resources and needs to be done in a manner that minimizes business disruption.
In the next few paragraphs, we will delve into the Azure Cloud, understand its benefits and common use cases, and why businesses might want to move away from it to an on-premise environment. We will then explore the process of Azure Cloud Repatriation and how businesses can simplify it with the help of Carbon, a software tool developed by SmiKar.

A deep dive into Azure Cloud
Microsoft Azure is a comprehensive set of cloud services that organizations use to build, deploy, and manage applications through Microsoft’s global network of datacenters. Fully integrated with Microsoft’s software offerings, it provides a robust platform that enables organizations to take advantage of the flexibility and efficiency of cloud computing. This includes scalable computing power, vast storage solutions, and advanced analytics and AI services that allow businesses to transform their operations and achieve their strategic objectives.
While it’s renowned for its PaaS capabilities, Azure also excels in its IaaS offerings. It supports a wide range of programming languages, tools, and frameworks, both Microsoft-specific and third-party, offering a flexible and friendly environment for developers. Besides, it provides robust security with its Security Center, a unified infrastructure security management system that strengthens the security posture of data centers and provides advanced threat protection.
With the help of Azure, businesses have been able to scale their operations, build and deploy a variety of applications, manage data effectively, and gain insights to make data-driven decisions. Whether it’s computing power they need, a place to store massive amounts of data, or advanced analytics and AI capabilities, Azure has been the go-to cloud platform for many businesses.
Benefits of Azure Cloud
One of the most significant benefits of Azure is its seamless integration with other Microsoft products, making it an ideal choice for organizations heavily invested in Microsoft technologies.
It also offers substantial cost savings by eliminating the need to invest in and maintain on-premise hardware. With its scalability, businesses can easily scale up or down their resources based on their needs, paying only for what they use. In terms of security, Azure provides robust security measures, with security analytics and threat intelligence built into the platform. It also offers tools for regulatory compliance, making it an attractive option for businesses in regulated industries.
Lastly, Azure’s global footprint with data centers worldwide allows businesses to deploy their applications close to their customers, reducing latency, and improving user experience.
Common use cases of Azure Cloud
Azure is often used for data backup and disaster recovery due to its reliability and robustness. It’s also commonly used for building, deploying, and managing applications and services, thanks to its PaaS offerings. Additionally, businesses use Azure for data analytics and artificial intelligence, utilizing its advanced capabilities to gain insights and make data-driven decisions. In many instances, Azure also supports the shift towards a remote work environment by providing a secure and scalable platform for virtual desktops and collaboration tools.

Why migrate from Azure Cloud to On-premise?
Azure is often used for data backup and disaster recovery due to its reliability and robustness. It’s also commonly used for building, deploying, and managing applications and services, thanks to its PaaS offerings. Additionally, businesses use Azure for data analytics and artificial intelligence, utilizing its advanced capabilities to gain insights and make data-driven decisions.
In many instances, Azure also supports the shift towards a remote work environment by providing a secure and scalable platform for virtual desktops and collaboration tools.
The need for control and security
One of the primary reasons for Azure repatriation is the need for more control over data and infrastructure. With Azure, while Microsoft takes care of the underlying infrastructure, businesses may feel they lack control over their environment. This can be a significant concern, especially for businesses in highly regulated industries or those dealing with sensitive data. On-premise environments provide businesses with complete control over their data, including where it’s stored, who can access it, and how it’s protected.
Similarly, while Azure provides robust security measures, some businesses might still prefer the security of having their data on-premise. This could be due to specific regulatory requirements or simply a preference for having physical control over their data.
Cost considerations
While cloud services offer the promise of reducing IT costs, the reality can be quite different. Depending on the usage pattern and the specific workloads, the costs of running services on Azure can quickly add up. These can include not just the costs of compute and storage, but also network costs, and the costs of other Azure services. For businesses with stable and predictable workloads, it might be more cost-effective to host these workloads on-premise, even when considering the costs of purchasing and maintaining hardware.
Performance and latency
While Azure’s global footprint allows businesses to deploy their applications close to their customers, there might still be performance issues or latency, especially for businesses serving a local or specific geographic market. In such cases, hosting the applications on-premise might provide a better user experience.

The Process of Azure Cloud Repatriation
The process of repatriating workloads from Azure Cloud to on-premise environments can be complex and requires careful planning.
Planning for Repatriation
Before initiating the repatriation process, businesses need to thoroughly evaluate their workloads and identify which ones would benefit from being on-premise. They need to consider the costs, performance requirements, and security and compliance requirements of these workloads.
Selecting VMs for Repatriation
Once the workloads have been identified, the next step is to select the Virtual Machines (VMs) on Azure that host these workloads. These VMs would need to be replicated and migrated back to the on-premise environment.
Preparing the on-premise environment
Finally, before the repatriation can begin, the on-premise environment needs to be prepared. This includes setting up the necessary hardware, configuring the network, and setting up the virtualization platform, whether it’s VMware or Hyper-V.
This process, while necessary, can be time-consuming and complex, especially for businesses with large numbers of VMs or complex applications. This is where Carbon, a software tool developed by SmiKar, can help.

Aiding Azure Repatriation: The Carbon Solution
Carbon is a solution designed specifically to assist with the process of Azure cloud repatriation. It offers businesses a comprehensive and streamlined process for migrating Azure Virtual Machines (VMs) back to an on-premise environment, either on VMware or Hyper-V. It simplifies and automates the traditionally complex and time-consuming process of cloud repatriation, reducing the risk of errors and minimizing disruption to the business.
Introduction to Carbon
Carbon is a feature-rich software tool that facilitates the effective management of Azure VMs, providing a level of detail that enables users to make informed decisions about which VMs to migrate and how to configure them in their on-premise environment. Carbon provides information such as VM name, status, size, number of CPUs, memory allocation, IP address, VNET, operating system, resource group, subscription name, location, and more.
Moreover, Carbon offers an easy and efficient migration and conversion process. It integrates seamlessly with VMware or Hyper-V environments, enabling users to replicate and convert their Azure VMs to their preferred on-premise hypervisor with just a few clicks. The software sets up replicated Azure VMs with the same CPU, memory, and disk configurations, ensuring a smooth transition back to the on-premise environment.
Features of Carbon for Azure VM Repatriation
One of the most impressive features of Carbon is its capability to provide comprehensive VM management. With its easy-to-navigate and customizable interface, users can adjust settings according to their preferences, such as their preferred hypervisor, datastore, and Azure subscription. This degree of customization ensures a smooth and efficient repatriation process, tailored to meet the specific needs of each business.
In addition to its VM management features, Carbon also offers automatic configuration and email notifications to keep users updated about the progress and completion of their migration. This feature ensures that businesses can monitor their repatriation process closely and intervene if necessary, further enhancing the efficiency and reliability of the repatriation process.
How Carbon simplifies Azure Repatriation
The complexity of Azure repatriation can often act as a barrier for many businesses. However, Carbon seeks to simplify this process and make it more accessible. By offering detailed information about Azure VMs and providing a simple and intuitive migration process, Carbon significantly reduces the time and resources required for repatriation.
The software’s ability to integrate with VMware or Hyper-V environments also makes it an excellent solution for businesses using these platforms, as it allows them to replicate and convert their Azure VMs easily. This seamless integration ensures that businesses can maintain the integrity and functionality of their VMs throughout the repatriation process, resulting in minimal disruption and a smooth transition back to the on-premise environment.
Carbon is a powerful tool for any business considering Azure repatriation. With its comprehensive features and user-friendly interface, it significantly simplifies the process, making it a less daunting task and enabling businesses to regain control of their workloads more efficiently.

Conclusion
Azure cloud repatriation is a strategic move that many businesses are considering in today’s dynamic digital landscape. While Azure offers numerous benefits, the need for greater control, cost considerations, and performance and latency issues often necessitate a shift back to on-premise environments. With careful planning and the right tools, this transition can be smooth and efficient. Carbon by SmiKar simplifies this process, making Azure repatriation an attainable goal for businesses worldwide.
FAQs
Q1: What is Azure Cloud Repatriation?
Azure Cloud Repatriation refers to the process of moving workloads and data back from the Azure cloud to on-premise infrastructure. This process is often initiated due to a need for more control, cost considerations, and performance and latency issues.
Q2: What factors should be considered when planning for Azure repatriation?
When planning for Azure repatriation, businesses need to consider the costs, performance requirements, and security and compliance requirements of their workloads. They also need to select the appropriate Virtual Machines (VMs) and prepare their on-premise environment for migration.
Q3: How does Carbon assist with Azure repatriation?
Carbon is a software tool that offers detailed information about Azure VMs and provides an easy and efficient migration and conversion process. It integrates seamlessly with VMware or Hyper-V environments and provides automatic configuration and email notifications to keep users updated about their migration process.
Q4: What are the key features of Carbon?
Some key features of Carbon include comprehensive VM management, easy migration and conversion process, seamless integration with VMware or Hyper-V environments, automatic configuration and email notifications, and a customizable interface that allows users to adjust settings according to their preferences.

by Mark | May 24, 2023 | Azure, Cloud Computing
A Tale of Two Directories
When it comes to identity and access management solutions, two names that often come up are Active Directory (AD) and Azure Active Directory (AAD). While many people are familiar with AD, AAD is still a relatively new concept to some. In this article, we will take a deep dive into both directories and explore their similarities, differences, pros, cons, and everything in between.
What is Active Directory?
Active Directory is Microsoft’s on-premises directory service that authenticates and authorizes all users and computers within an organization. It provides single sign-on (SSO) access to network resources such as files, folders, printers, applications, etc. AD stores user account information like usernames and passwords in a centralized database that can be managed by IT administrators. Since its release in 1999 as a part of Windows 2000 Server edition, AD has been one of the most widely used directory services for organizations big and small alike.
What is Azure Active Directory?
Azure Active Directory is Microsoft’s cloud-based directory service that offers identity and access management for cloud-native applications. It provides authentication services for web applications as well as SSO integration with other Microsoft cloud services like Office 365 or Dynamics 365. Launched in 2010 alongside Windows Azure platform at PDC10 event in Redmond WA USA Azure AD was first designed to be used with Microsoft’s Cloud solutions but over time it has expanded its usage beyond the Microsoft ecosystem allowing organizations to manage SaaS application authentication across multiple platforms from AWS to Salesforce.
Why Compare Active Directory with Azure Active Directory?
Both directories serve the same purpose- providing identity and access management solutions- but they operate differently based on where they are deployed. Many organizations rely solely on AD since it has been around much longer and is the more established directory service.
However, as cloud adoption continues to rise, companies that are migrating to the cloud or already use cloud applications need a directory that can provide authentication and authorization for their web-based apps. Comparing AD and AAD side-by-side will help you make an informed decision about which directory service to use, depending on your organization’s requirements.
While both solutions have their strengths and weaknesses, choosing one over the other will depend on several factors such as size of the organization, budget constraints, security requirements, IT team’s expertise level etc. In the next section of this article, we will discuss the high-level differences between AD and AAD.
Active Directory vs. Azure Active Directory
High-Level Overview
The Key Differences Between the Two
Active Directory (AD) and Azure Active Directory (Azure AD) are both directory services from Microsoft, but they differ significantly in terms of their architecture, features, and capabilities. One of the main differences between the two is that AD is an on-premises solution while Azure AD is a cloud-based solution. This means that with AD, all of your data and resources are stored on servers within your organization’s network.
With Azure AD, however, all resources are managed in the cloud and can be accessed from anywhere with an internet connection. Another key difference between the two is that AD is primarily designed to manage devices and users within an organization’s network environment while Azure AD extends that management to cloud-based applications.
The Advantages and Disadvantages of Each
AD has several advantages over Azure AD. First, it offers greater control over user authentication and security. Since all data resides on-premise behind a firewall, IT teams can better manage access to sensitive information by defining granular access policies for each user or group. Secondly, since AD was designed for on-premises use cases only, it remains a more mature product with more robust features such as Group Policy Objects (GPOs).
GPOs enable administrators to define how system settings should be managed across an organization’s entire network. However, one major disadvantage of using only AD is that as more organizations adopt cloud-first strategies for their businesses or transition to remote work environments; managing identities becomes cumbersome.
Azure Active Directory also has its advantages over traditional Active Directory. For one thing, it provides cloud identity management which makes it easier for employees to work remotely without compromising security protocols.
This feature grants access from any location via an internet connection securely. Another advantage is SSO (Single Sign-On) capabilities that come with Azure AD. SSO allows users to log in once, and then access all authorized applications without the need to repeatedly enter usernames and passwords.
However, one disadvantage of using Azure AD is that it may not be a good fit for organizations with many legacy applications that do not support modern authentication protocols. Active Directory (AD) is better suited for on-premises environments while Azure AD is better suited for cloud-based environments.
The decision between the two mainly depends on an organization’s specific needs. Nonetheless, hybrid identity management using both solutions can provide a balance between control and flexibility.
Managing Users and Devices
How user and device management differs between the two
Active Directory and Azure Active Directory differ in their approach to user and device management. Active Directory is primarily an on-premises solution, while Azure AD is a cloud-based solution.
This means that managing users and devices in Active Directory typically involves using a combination of Group Policy Objects (GPOs) and a local Active Directory domain controller, while in Azure AD, user and device management is done entirely through the cloud-based Azure portal. One of the biggest differences between the two solutions is the way that users and devices are added to each directory.
In Active Directory, users are typically added manually through the Active Directory Users and Computers (ADUC) tool or imported from a CSV file. Devices can be joined to an on-premises domain using either manual or automated methods.
In contrast, adding users in Azure AD can be done through multiple methods including PowerShell scripting or Azure AD Connect sync with on-premises AD environments. Similarly, devices can be registered with Azure AD using various methods including Intune device management.
Benefits of managing users and devices in Azure AD
Managing users and devices through Azure AD brings several distinct benefits over traditional on-premises solutions like Active Directory. One of these benefits is flexibility – since everything is managed through the cloud portal, administrators can manage their environment from anywhere with internet access without needing VPN connections or RD sessions into servers. Another benefit of using Azure AD for user/device management comes from its integration with other Microsoft services such as Office 365 or Dynamics 365.
When integrated with these services, administrators gain access to additional features such as conditional access policies (CAPs) that allow them to control who has access to which resources based on factors such as location or device type. Managing users/devices through Azure AD offers better security than traditional on-premises solutions.
With Azure AD, administrators can leverage features like multi-factor authentication (MFA), conditional access policies, and identity protection to secure their environment against cyber threats. Plus, with cloud-based management, updates and patches are automatically pushed out ensuring the latest security protocols are in place.
While Active Directory is still a widely used solution for user and device management in large enterprises, Azure AD offers several benefits that make it an attractive option for organizations looking to move their infrastructure to the cloud. By providing flexible access anywhere with an internet connection, integration with other Microsoft services such as Office 365 or Dynamics 365, and better security protocols like MFA and conditional access policies – it’s clear why Azure AD is becoming an increasingly popular choice for modern businesses.
Authentication and Security Features
Comparison of authentication methods used by both ADs
Authentication is the process of verifying the identity of a user or device attempting to access a system. Active Directory uses Kerberos as its primary authentication protocol.
Kerberos is a ticket-granting system that allows users to authenticate once and then access resources without having to re-enter login credentials for each new request. Azure Active Directory, on the other hand, supports multiple authentication protocols such as OAuth 2.0, OpenID Connect, and SAML 2.0.
It also provides multi-factor authentication (MFA) options like SMS verification, phone call verification, and mobile app-based verification. This means that Azure AD has more flexible authentication options than Active Directory.
Security features unique to Azure AD
Azure AD offers several security features unique to its platform. One of these features is Conditional Access which allows administrators to control who can access an organization’s resources based on certain conditions like device type or location.
Another feature offered by Azure AD is Identity Protection which detects potential security threats like risky sign-ins or compromised credentials and takes appropriate action to prevent unauthorized access. Azure AD also provides Privileged Identity Management (PIM) which allows administrators to manage and monitor privileged identities within their organization.
PIM enables just-in-time administration of privileged roles, reducing the risk of accidental misuse or intentional abuse. Additionally, Azure AD supports integration with third-party security solutions through Microsoft’s Intelligent Security Graph which helps organizations detect and respond to potential security threats in real-time.
While both Active Directory and Azure Active Directory have strong authentication mechanisms at their core, Azure AD offers more flexibility and granular control over user access through its support for multiple protocols including MFA options. Moreover, its advanced suite of security features like Conditional Access, Identity Protection and PIM provide greater protection against modern-day security threats.
Integration with Other Microsoft Services
One Integration to Rule Them All
Active Directory and Azure Active Directory both offer seamless integration with other Microsoft services. For organizations using Office 365 or Dynamics 365, this integration can be particularly useful.
Users can use their existing credentials to log in to these services without having to remember multiple usernames or passwords. In addition, administrators can easily manage access and permissions for these services through either AD platform.
The Benefits of Azure AD Integration
One benefit of using Azure AD for Microsoft service integration is the ability to extend identity management beyond the organization’s borders. This means that third-party partners or vendors can also access certain applications or data using their own existing credentials.
This feature can be especially beneficial for companies that work with contractors or freelancers who need temporary access. In addition, Azure AD also offers more robust security features than traditional Active Directory.
For example, conditional access policies allow administrators to set specific conditions that must be met before a user is granted access to certain resources. This extra layer of security helps prevent unauthorized access from potential threats.
The Benefits of Active Directory Integration
Traditional Active Directory also offers benefits when it comes to Microsoft service integration. One such benefit is the ability to manage Group Policy Objects (GPOs) across all domain-joined computers in an organization. GPOs allow administrators to enforce specific security settings on all devices within the network, helping ensure compliance and protect against potential threats.
Another benefit is compatibility with older applications that may not yet have full Azure AD integration capabilities. While most modern applications are compatible with both AD platforms, there may still be legacy applications within an organization that require traditional Active Directory for proper authentication and authorization.
Which One Is Best?
Ultimately, whether an organization chooses Active Directory or Azure Active Directory for Microsoft service integration depends largely on their specific needs and use cases. While Azure AD offers more robust security features and the ability to extend identity management outside of the organization, traditional Active Directory offers compatibility with older applications and better GPO management. If an organization primarily uses newer Microsoft services and applications, Azure AD may be the better choice.
However, if there are still legacy systems or older applications in use, traditional Active Directory may still be necessary. Ultimately, it’s important for organizations to carefully consider their specific needs before making a decision on which AD platform to use for Microsoft service integration.
Cost Considerations
When it comes to choosing between Active Directory (AD) and Azure Active Directory (AAD), one of the most important factors to consider is cost. Both ADs have different pricing models, so it’s essential to understand what you’re paying for and how much it will cost. In this section, we’ll cover the pricing models for both ADs and the factors that may influence your costs.
Comparison of Pricing Models for Both ADs
Active Directory is available as part of Windows Server. Therefore, if you have Windows Server deployed on-premises, you already have access to Active Directory at no additional cost. However, there are still costs associated with deploying and managing Active Directory on-premises, such as hardware costs and maintenance costs.
In contrast, Azure Active Directory is a cloud-based service that requires a subscription. You can choose from several subscription plans based on your organization’s needs.
For example, if you only need basic user management features like single sign-on (SSO) and multi-factor authentication (MFA), the “Azure AD Free” plan may be suitable for your organization and comes at no cost. If you require more advanced features such as identity governance or privileged access management, then you’ll need to subscribe to one of the paid plans like “Azure AD Premium P1” or “Azure AD Premium P2.” The pricing for these plans ranges from around $6 per user per month to $15 per user per month.
Factors That May Influence Cost Considerations
The specific needs of your organization will determine which plan best suits it and how much it will cost. Some factors that may influence your costs include:
-
- The number of users in your organization: The more users you have, the higher the cost will be.
-
- The level of security you require: More advanced security features like conditional access and identity protection come at a higher cost.
-
- Whether your organization operates solely on-premises or in the cloud: If you have on-premises applications, you may require a hybrid AD solution which comes at an additional cost.
-
- Whether you need integration with other Microsoft services like Office 365, Dynamics 365, etc.: Some plans include access to these services while others do not.
Keep in mind that the pricing models for both Active Directory and Azure Active Directory are subject to change. Before making a final decision, it’s essential to check for any updates related to pricing and subscription plans.
Additionally, consider other factors such as ease of use and management when selecting between ADs Choosing between Active Directory and Azure Active Directory is not just about comparing their features but also considering their costs.
While AD is available at no additional cost if you have Windows Server installed on-premises, there are still associated costs. Azure AD requires a subscription plan that depends on your organization’s specific needs.
Factors such as the number of users in your organization or the level of security required can influence your costs. Ultimately, it’s best to compare both pricing models thoroughly before making a decision.
Hybrid Identity Management
The Small Detail that Can Make a Big Difference
The Hybrid Identity Management Solution in Active Directory and Azure Active Directory
Hybrid identity management is a lesser-known, but increasingly important feature of both Active Directory and Azure Active Directory. It refers to the synchronization of on-premises identity infrastructure with cloud-based identity providers. This allows users to access resources on-premises as well as in the cloud, using their usual credentials.
In the case of Active Directory, hybrid identity management is provided by Azure AD Connect. This tool synchronizes user information from an on-premise AD instance to an Azure AD instance in the Cloud.
On the other hand, Azure AD provides a comprehensive hybrid identity management solution that includes seamless synchronization with several third-party authentication providers such as Okta, Ping Federate, and more. Additionally, it includes features that enable federation between on-premises identities and cloud services like Office 365.
The Benefits of Hybrid Identity Management
Hybrid identity management offers several benefits for organizations looking to move towards cloud-based environments while still maintaining their existing on-premise infrastructure:
– Single Sign-On across all networks: Users can sign in once and access all network resources without having to enter their credentials again.
– Security: Passwords are synchronized across both environments so users only need one set of credentials.
– Scalability: The ability to scale users up or down based on changing organizational needs.
How To Deploy Hybrid Identity Management Solutions
If you want to deploy hybrid identity solutions for your organization, first determine which solution best fits your business needs then follow these steps: 1. Plan your environment
2. Install Azure AD connect (in the case of Active Directory) or Azure AD (for cloud-based identity management)
3. Connect to your on-premises Active Directory environment
4. Configure synchronization between on-premises Active Directory and Azure AD 5. Test synchronization and resolve any issues
The Differences in Group Policy Objects between Active Directory and Azure Active Directory
What Group Policy Objects (GPOs) Do?
Group Policy Objects or GPOs are configuration settings that apply to user accounts and groups or computers within an organization’s network. They are meant to enforce security, set up networking parameters, configure software settings, etc.
In the case of Active Directory, GPOs are used to configure settings for domain-joined machines such as password policies, remote access permissions, firewall settings, and more. However, in the case of Azure AD: while there are no GPOs per se, there are similar features called Conditional Access policies that can be configured in a similar way.
The Differences Between AD and AAD Regarding GPOs
There are several differences between how GPOs work in AD versus AAD: – While GPO editing is done through the GUI on domain controllers for AD; this functionality does not exist for AAD because it is a cloud-based solution.
– In contrast to AD where all users can use the same set of policies; in AAD different user groups can be assigned specific policies based on their needs. – Whereas an average IT person with appropriate permissions can create or edit GPO objects in AD; creating Conditional Access Policies requires global administrator rights.
The Benefits of Conditional Access Policies over Traditional GPO Management
Conditional Access Policies in Azure AD offer several advantages over traditional GPO management: – Location-based access: Controls and restricts access to network resources based on the location of the user requesting access.
– Device compliance: Ensures that devices accessing network resources are compliant with organizational policies by checking if encryption, password requirements, etc., are met. – Granular control: Allows administrators to configure policies based on device type, user group, application being accessed, etc.
Both AD and AAD offer solutions for configuring settings across an organization’s network. However, there are some key differences between the two systems in terms of how they manage Group Policy Objects.
While AD provides a more traditional approach through GPOs that can be edited through the GUI on domain controllers; Azure AD provides a cloud-based solution that leverages Conditional Access Policies to provide granular control over network access. Ultimately, each solution has its own strengths and weaknesses depending on the business needs of an organization.
Conclusion
Summary of key points discussed throughout the comparison
Active Directory (AD) and Azure Active Directory (AAD) are both powerful tools for managing users, devices, and security in an organization. AD is an on-premise solution that provides a wide range of capabilities for managing resources within the local network.
AAD is a cloud-based solution that offers similar capabilities to AD but with the added benefit of being accessible from anywhere with an internet connection. When it comes to managing users and devices, AAD offers several benefits over AD. For example, AAD allows administrators to manage devices remotely, provides single sign-on functionality for web-based applications, and supports multi-factor authentication out of the box.
However, AD still provides more granularity when it comes to Group Policy Objects (GPOs) compared to AAD. Both AD and AAD offer robust authentication and security features.
However, AAD has a unique advantage in that it can integrate with other Microsoft services such as Office 365 and Dynamics 365. This allows organizations using these services to take advantage of seamless access control across their entire Microsoft ecosystem.
Final thoughts on which AD may be best suited for certain organizations or scenarios
Ultimately, the decision between using AD or AAD will depend on several factors such as organizational size, budget constraints, need for mobility/accessibility from anywhere in the world and level of complexity required for device management. Organizations that require extensive control over their resources may find that AD is better suited for them due to its granular GPO functionality.
Moreover small scale organizations who do not have many resources can opt for Azure Active Directory due to its cost-effective nature coupled with ease-of-use without having an on-premise infrastructure. On the other hand larger organizations with distributed workforce might find Azure Active Directory more ideal due its cloud-first design choices which ensures that users can access resources from anywhere in the world so long as they have an internet connection.
Overall, both AD and AAD are powerful tools for managing resources in an organization. The choice largely depends on specific organizational needs, size, complexity of resource management required, and budget constraints.

by Mark | May 23, 2023 | Azure, Cloud Computing, Cloud Storage
Microsoft Azure is often hailed for its “limitless potential” and “unlimited possibilities”. But what does that mean in practical terms? How can Azure transform your business operations and why is it worth your attention? In this article, we’ll delve into these questions and illustrate the value of Azure through four key applications that can enhance your business operations and provide tangible benefits.
Understanding Azure
At its heart, Azure is a versatile public cloud computing platform. It offers a range of solutions, such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). These solutions can be used for a multitude of services like analytics, virtual computing, storage, and networking, to name a few. Azure can either replace or supplement your on-premise servers, depending on your business needs.
Let’s consider some of the standout features of Azure:
-
-
- Microsoft Azure – IaaS, PaaS, and SaaS: This trio of services allows you to choose the level of control you want over your IT infrastructure, platforms, and software.
-
- Flexible: Azure allows you to scale your compute resources up and down as required, ensuring that you only pay for what you use.
-
- Open: Azure supports almost any operating system (OS), language, tool, or framework, facilitating seamless integration with your existing systems.
-
- Reliable: Azure boasts a 99.95% availability Service Level Agreement (SLA) and offers round-the-clock technical support.
-
- Global: Azure’s data is housed in geo-synchronous data centers, ensuring fast and reliable access regardless of your location.
-
- Economical: With Azure, you only pay for the resources you use, making it a cost-effective solution for businesses of all sizes.
Azure in Action: Four Key Applications
Enhancing and Implementing Backup and Disaster Recovery
Azure is an excellent tool for backup and disaster recovery, thanks to its flexibility, advanced site recovery capabilities, and built-in integration. Being a cloud-based solution, Azure can back up your data in almost any language, on any OS, and from any location. You also have the flexibility to set your backup schedule as per your business requirements – daily, weekly, monthly, or otherwise.
While tape backup systems have their place, they have limited capabilities when used as a standalone backup and disaster recovery solution. Azure site recovery enhances your tape backup with offsite replication, minimal onsite maintenance, and up to ninety-nine years of data retention. It also reduces both capital investment and operational costs. Azure ensures data safety by storing three copies of your data in three different locations within the data center, and another three copies in a remote Azure data center.
If you’re operating in a Windows virtual environment, Azure’s built-in integration for additional backup provides a quick and efficient solution. Azure site recovery integrates with System Center and HyperV architectures, creating a robust and seamless cohesion between Azure, System Center, and HyperV.
Hosting and Developing Web and Mobile Apps
Azure provides an excellent platform for hosting, developing, or managing web or mobile apps.
Whether you’re looking for a platform to host, develop, or manage web or mobile apps, Azure has got you covered. Its features enable your apps to be self-sufficient and adaptive. This includes automatic patch management for your virtual machines, which allows you to devote less time to infrastructure management and more time to enhancing your apps. Azure also offers continuous deployment support to streamline ongoing code updates.
Azure’s AutoScale feature, built into Azure Web Apps, adjusts your resources automatically based on customer web traffic. This ensures that you have the necessary resources during high-traffic periods and saves money during off-peak times.
Moreover, Azure can seamlessly link your web app to an on-premise app. This connectivity allows both employees and partners to securely access resources inside your firewall, which would otherwise be challenging to access externally.
Distributing and Supplementing Active Directory
Azure can integrate with your Active Directory (AD), enhancing your identity and access capabilities. This integration extends your Domain Name System’s (DNS) global reach, centralizes management, and bolsters security.
Azure allows you to globally distribute an AD environment that is direct connect enabled. No other cloud provider can extend the reach of your domain controller and consolidate AD management like Azure.
For organizations with multiple locations or those using on-premise apps or cloud apps like Microsoft 365, integrating Active Directory with Azure becomes a central tool for managing and maintaining access to all these tools.
Azure also supports multi-factor authentication, adding an extra layer of security to your data and applications without causing any inconvenience to your users. It also allows for easy implementation of single sign-on for Windows, Mac, Android, and iOS cloud apps.
Innovating with IoT Industry Solutions
The scalability, flexibility, and security of Microsoft Azure make it an excellent resource for companies moving toward Internet of Things (IoT) solutions. Azure allows you to connect your devices to the cloud using solutions that integrate with your existing infrastructure, enabling you to start collecting new data about your company.
The Azure IoT Hub lets you monitor and manage billions of devices and gain insights that can help you make better business decisions, enhance customer experiences, reduce complexity, lower costs, and expedite development.
The enhanced security of Azure is a significant asset for IoT solutions, which often have security gaps that hackers can exploit. Azure provides other benefits like remote monitoring, predictive maintenance, and analytics.
Getting started with Azure IoT is easy with Azure IoT solution accelerators. These preconfigured templates are customizable to your needs and help you hit the ground running with your IoT initiatives.
Your Azure Journey
The above four applications are just the tip of the iceberg when it comes to what Azure can do for your business. Azure is a treasure trove of cloud-computing potential that you can leverage in almost any way imaginable.
If you’re ready to explore these services, you can start with a trial and $200 in Azure credits. You can also get an idea of the cost by using the pricing calculator. If you have questions about other ways you could use Azure or need help implementing a service, consider reaching out to a sales engineer who can help you plan and implement the right tools to meet your needs.