
by Mark | Jun 3, 2016 | How To, Patch Releases, SCCM
KB3155482 for SCCM 1602
Microsoft released a new patch for System Centre Configuration Manager today (KB3155482) which fixes the following issues in SCCM version 1602.
- Remote Control
- The SCCMRDPSYSTEM.EXE process stops running on Windows Embedded clients after your try and start a remote control session.
- Site Systems
- The DBSchemaChangeHistory table in the site database grows exponentially.
- Microsoft Intune and Mobile Device Management
- The Service Connection Point can take 30 minutes or more to recognize a newly added Microsoft Intune Subscription.
- Incorrect certificate data can be used to manage mobile devices which can causes this to fail
- The Service Connection Point may try and renew the wrong certificate if multiple certificates are installed and have the same expiration date.
- An “Invalid parameter to CIM setting” message is displayed when you try to check the baseline deployment status of a custom IOS or Mac profile.
- The SMS_DMP_Connector registry key remains after you remove a Microsoft Intune subscription. Successive attempts to add a new Microsoft Intune subscription trigger authentication errors.
The hotfix should be now available to install directly from your SCCM console.
Open the SCCM console and go to Administration, then Cloud Services, then Updates and Servicing
In the right pane, you should see the update has downloaded and is ready to install.

Right click the update and choose Install Update Pack
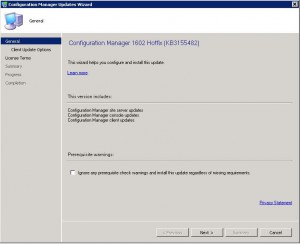 Click on Next to start the installation.
Click on Next to start the installation.
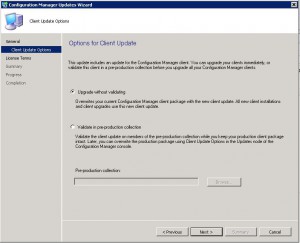 Choose whether you want to vaildate or not and click on Next.
Choose whether you want to vaildate or not and click on Next.
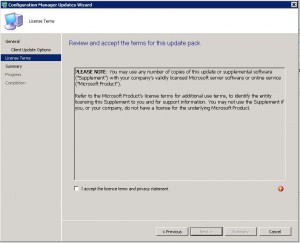
Accept the license terms checkbox and click on Next.
Make sure your environment is ready for the installation and when you are ready to do so, click on Next.
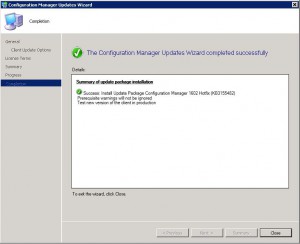
If all has gone well and the installation didnt come across any errors, you can now Close the window.
You should now have installed KB3155482 in to your SCCM 2012 environment.
See how our software, SnaPatch Patch Management addon for SCCM can help you.

by Mark | Mar 29, 2016 | How To, Patch Management
Manually download updates with SCCM
In today’s fast-paced world, keeping up with the latest software updates is critical. With new features, bug fixes, and security patches being released every day, it’s essential to ensure that your systems are up to date. Microsoft’s System Center Configuration Manager (SCCM) is an enterprise-grade software management solution that allows you to deploy and manage software updates across your organization. In this article, we will explore how to manually download updates with SCCM to keep your systems up to date.
What is SCCM?
SCCM is a software management tool developed by Microsoft. It allows IT administrators to manage and deploy software updates, security patches, and other configuration changes across their organization’s Windows devices. SCCM provides a centralized console where administrators can view and manage all of their organization’s Windows devices and ensure that they are up-to-date with the latest software and security updates.
Why Use SCCM?
There are several benefits to using SCCM for software management:
- Centralized management: SCCM provides a centralized console for managing all Windows devices in an organization, making it easy to manage software updates and security patches across multiple devices.
- Automation: SCCM can automate the deployment of software updates and security patches, saving IT administrators time and ensuring that updates are consistently applied across all devices.
- Reporting: SCCM provides detailed reporting capabilities, allowing administrators to track which devices are up-to-date with the latest software and security updates.
Now that we’ve covered the basics of SCCM let’s dive into the process of manually downloading updates with SCCM.
Understanding SCCM Software Updates
Before we dive into how to manually download updates with SCCM, let’s first understand what software updates are and how SCCM handles them. Software updates are packages that contain updates to existing software, such as security patches, bug fixes, and feature enhancements. SCCM uses the Windows Server Update Services (WSUS) infrastructure to manage and deploy software updates.
WSUS is a server role that allows administrators to manage and distribute updates for Windows operating systems and other Microsoft software. SCCM uses WSUS to download software updates from Microsoft Update and distribute them to client computers in the organization. SCCM also allows administrators to create and deploy custom software updates to meet specific business needs.
Now that we have a basic understanding of how SCCM handles software updates let’s explore how to manually download updates with SCCM.
If you ever have the need to Manually Download Updates with SCCM (like with a zero day exploit deployment) I will show you how to below. This helps even if updates haven’t been downloaded automatically by the Auto Deployment Rule.
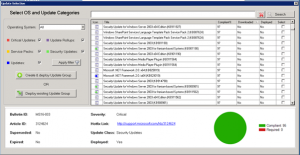
To kick off a manual download of updates with SCCM, follow these steps.
Open your SCCM console and go to Software Library, then expand Software Updates and then click on All Software Updates.
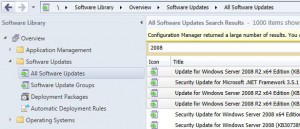
Let the list populate and select the updates that want to download, then right click and choose Download.
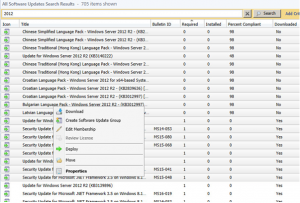
It will then prompt your to Select a Deployment Package. Click Browse.
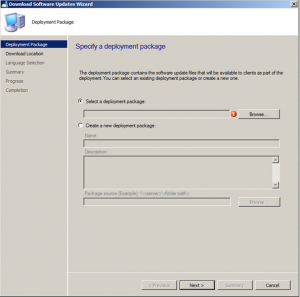
Select the Auto Deployment Rule that you use for your monthly patch deployments and then click on OK.
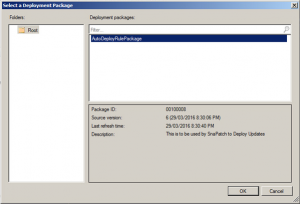
Once the deployment rule had been selected, click on Next.
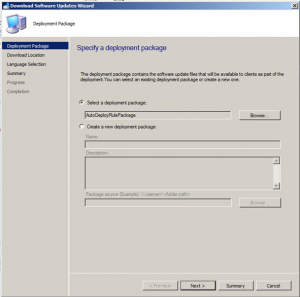
Now choose to Download software updates from the Internet.
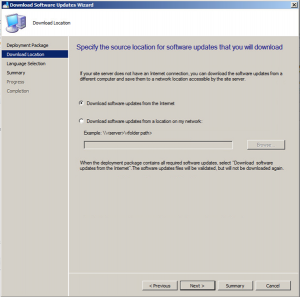
Choose the required update language then click Next.
Now you should be ready to download the updates you have selected. If ready to do so, click on Next.
Your updates will start downloading. Note that this may take some time to complete the downloads.
Hopefully all went well and your updates are now ready to be deployed.
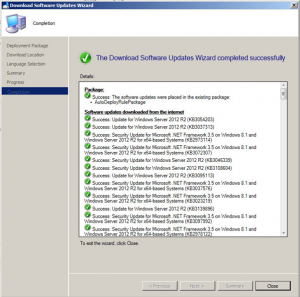
This is a great way to download updates really quickly and make them available to deploy them to your desktops and servers. Click the link to see another great post on how to create a SCCM Automatic Deployment Rule.
by Mark | Feb 16, 2016 | SCCM
SCCM – version 1511 New Features
The latest version of Microsoft’s System Centre Configuration Manager has been released. (SCCM 1511). While we all expected this to be called SCCM 2016, it is in fact now called SCCM 1511. The new versioning is due to the fact that SCCM update cycle will be frequent. Every new version will be named as SCCM YYMM (Year and Month). Version 1511 was released on the 15th of November, hence 1511.
The new features as part of this release are as follows;
Windows 10
- Windows 10 servicing
- Sideloading apps in Windows 10
- Compliance settings for Windows 10
Infrastructure
- Preferred management points
- Single Primary site supports up to 150k clients and 700k client in a hierarchy
- Support for Microsoft Azure virtual machines
- Diagnostics and Usage Data
- Service a server cluster
- Support for SQL Server AlwaysOn for highly available databases
- Integration with Windows Update for Business
Console
- Natively manage Office 365 desktop client update
- Deploy Windows Business Store applications
- Support for multiple Automatic Deployment Rules
- Client deployment status in console monitoring
- Schedule and run the WSUS clean up task from the Configuration Manager console
- Updates and servicing
- Client piloting to preproduction
- Software Center
Operating System Deployment
- Windows 10 in-place upgrade task sequence
- Windows PE Peer Cache
Mobile Device Management
- Mobile device management (MDM) feature parity between Intune stand-alone and Configuration Manager
- Mobile Application Management
- Data protection for mobile devices
- On-premises mobile device management (MDM)
- App deployment to Windows 10 devices with on-premises MDM
- Certificate provisioning is supported for Windows 10 devices that you manage using on-premises mobile device management.
- Improved workflow for creating mobile device configuration items
- Bulk enrollment of Windows 10 devices with on-premises MDM
- Wipe and retire for on-premises mobile device management
A perfect addon for SCCM patching deployment to your virtual machines, is our product known as SnaPatch. Click here to see how SnaPatch can help you reduce the risk of patch deployment.
by Mark | Dec 9, 2015 | Patch Management, Patch Releases, SCCM
Microsoft’s December 2015 Patch Releases
The following twelve Patch Tuesday updates / patches have been released by Microsoft for the December 2015 Update deployment.
MS15-112 – Critical
Cumulative Security Update for Internet Explorer (3104517)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS15-125 – Critical
Cumulative Security Update for Microsoft Edge (3116184)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS15-126 – Critical
Cumulative Security Update for JScript and VBScript to Address Remote Code Execution (3116178)
This security update resolves vulnerabilities in the VBScript scripting engine in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if an attacker hosts a specially crafted website that is designed to exploit the vulnerabilities through Internet Explorer (or leverages a compromised website or a website that accepts or hosts user-provided content or advertisements) and then convinces a user to view the website. An attacker could also embed an ActiveX control marked “safe for initialization” in an application or Microsoft Office document that uses the Internet Explorer rendering engine to direct the user to the specially crafted website.
MS15-127 – Critical
Security Update for Microsoft Windows DNS to Address Remote Code Execution (3100465)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker sends specially crafted requests to a DNS server.
MS15-128 – Critical
Security Update for Microsoft Graphics Component to Address Remote Code Execution (3104503)
This security update resolves vulnerabilities in Microsoft Windows, .NET Framework, Microsoft Office, Skype for Business, Microsoft Lync, and Silverlight. The vulnerabilities could allow remote code execution if a user opens a specially crafted document or visits a webpage that contains specially crafted embedded fonts.
MS15-129 – Critical
Security Update for Silverlight to Address Remote Code Execution (3106614)
This security update resolves vulnerabilities in Microsoft Silverlight. The most severe of the vulnerabilities could allow remote code execution if Microsoft Silverlight incorrectly handles certain open and close requests that could result in read- and write-access violations. To exploit the vulnerability, an attacker could host a website that contains a specially crafted Silverlight application and then convince a user to visit a compromised website. The attacker could also take advantage of websites containing specially crafted content, including those that accept or host user-provided content or advertisements.
MS15-130 – Critical
Security Update for Microsoft Uniscribe to Address Remote Code Execution (3108670)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains specially crafted fonts.
MS15-131 – Critical
Security Update for Microsoft Office to Address Remote Code Execution (3116111)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS15-132 – Important
Security Update for Microsoft Windows to Address Remote Code Execution (3116162)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow remote code execution if an attacker accesses a local system and runs a specially crafted application.
MS15-133 – Important
Security Update for Windows PGM to Address Elevation of Privilege (3116130)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to a target system and runs a specially crafted application that, by way of a race condition, results in references to memory locations that have already been freed. Microsoft Message Queuing (MSMQ) must be installed and the Windows Pragmatic General Multicast (PGM) protocol specifically enabled for a system to be vulnerable. MSMQ is not present in default configurations and, if it is installed, the PGM protocol is available but disabled by default.
MS15-134 – Important
Security Update for Windows Media Center to Address Remote Code Execution (3108669)
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if Windows Media Center opens a specially crafted Media Center link (.mcl) file that references malicious code. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS15-135 – Important
Security Update for Windows Kernel-Mode Drivers to Address Elevation of Privilege (3119075)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to a target system and runs a specially crafted application.

 Click on Next to start the installation.
Click on Next to start the installation. Choose whether you want to vaildate or not and click on Next.
Choose whether you want to vaildate or not and click on Next.














