by Mark | May 14, 2023 | Azure, Azure VM Deployment
Understanding Azure Virtual Machine Sizes
Azure Virtual Machines (VMs) let you run applications and workloads in the cloud using flexible, scalable computing power. But Azure offers dozens of VM types and sizes — so how do you choose?
Each VM size offers a different mix of resources like CPU, memory (RAM), and disk speed. The key is choosing a VM size that matches the performance needs of your workload — without overspending.
Below is a breakdown of Azure’s main VM categories. We explain what each one is designed for and what makes them different, in a way that’s easy to understand.
Azure VM Categories: Explained Simply
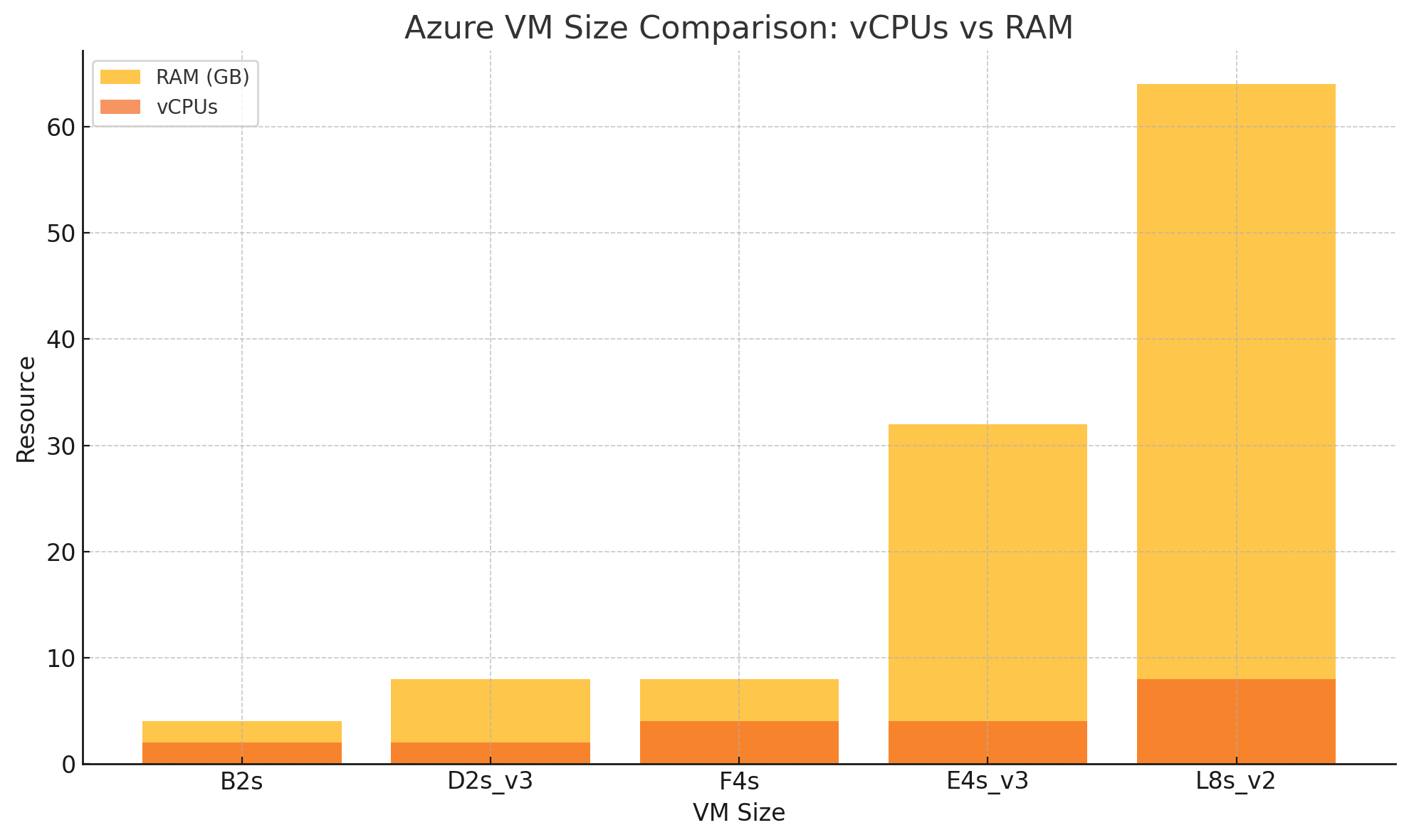
Azure offers a wide range of virtual machine (VM) sizes, each tailored to different types of workloads. Choosing the right Azure VM size can help you balance performance and cost. Here’s an easy-to-understand breakdown of the four main Azure VM categories and what they’re best suited for.
| Category |
Best For |
Key Features |
Example Series |
| General Purpose |
Web servers, dev/test, small databases |
Balanced CPU-to-memory ratio; good for everyday use |
B, D, Dv2, Av2 |
| Compute Optimized |
Batch processing, web front-ends, gaming servers |
Higher CPU-to-memory ratio; ideal for compute-heavy tasks |
F, Fsv2 |
| Memory Optimized |
Large databases, in-memory caching, SAP HANA |
High memory per vCPU; optimized for RAM-intensive workloads |
E, Ev3, Ev4, M |
| Storage Optimized |
Big data, NoSQL databases, data warehousing |
High disk throughput and IOPS; local SSD storage |
Lsv2, Msv2 |
Tip: Not sure where to start? Try a B-Series (Burstable VM). It’s a low-cost, flexible option great for development, testing, or small web apps that don’t always need full CPU power.
How to Choose the Right Azure VM Size
The best Azure VM size for your workload depends on what your application needs most: CPU, memory, or storage.
– For general flexibility, start with General Purpose.
– If you’re running processor-intensive workloads like API servers or video encoding, Compute Optimized is the way to go.
– Memory Optimized VMs are great for database-heavy apps, and Storage Optimized VMs shine with IOPS-heavy apps and big data.
Microsoft regularly updates and adds new VM series, so always check the official Azure VM sizes documentation for the latest specs and availability in your region.
Introducing Carbon
Carbon is a purpose-built tool designed to simplify Azure VM management and streamline virtual machine migrations. Whether you’re moving workloads back to on-premises infrastructure or optimizing Azure environments, Carbon gives you full control and deep visibility into every VM.
Core Features
- Effortless Migration: Seamlessly migrate Azure VMs to VMware or Hyper-V environments with just a few clicks.
- Comprehensive VM Insights: Access detailed configuration, usage stats, and performance data for each virtual machine.
- Automated Workflows: Carbon handles configuration, export, and setup automatically, reducing manual workload and errors.
- Progress Alerts: Receive real-time email updates during each stage of migration or deployment.
- Secure Transfers: All data is handled securely using encrypted connections and trusted authentication protocols.
Why Use Carbon?
Carbon was built for IT administrators, cloud engineers, and architects looking for a better way to manage their virtual environments in Azure. Whether you’re migrating, optimizing, or reporting, Carbon makes your job easier.
- Reduce Azure Costs: Migrate or remove underutilized VMs to optimize billing and performance.
- Gain Visibility: View all your VM data from a single pane of glass, including disk usage, VM size, and uptime.
- Simplify Management: Automate the time-consuming tasks involved in VM administration.
- Ensure Continuity: Minimize downtime and avoid misconfigurations with intelligent workflows.
Frequently Asked Questions About Azure VM Sizes
1. How do I choose the right Azure VM size?
Start with your workload. If your app needs balanced performance, go with General Purpose. For heavy compute or memory needs, pick Compute or Memory Optimized VMs. Azure also offers sizing recommendations in the portal when deploying VMs.
2. Can I resize a VM later?
Yes, you can resize most VMs in the Azure portal or using CLI. However, your VM may need to be stopped first, and the new size must be available in the region where your VM is hosted.
3. What’s the cheapest Azure VM size?
The B-Series (like B1s or B2s) is usually the most cost-effective. It’s ideal for workloads that don’t run at full CPU all the time, such as development or low-traffic websites.
4. What happens if I choose the wrong size?
Your VM might underperform or cost more than needed. Fortunately, you can always resize to a better-suited tier once you understand your actual usage and performance needs.
5. What’s the difference between vCPU and core?
A vCPU is a virtual CPU — essentially a portion of a physical core on a hypervisor. Azure charges and assigns VM power based on vCPUs, not actual physical cores.
Pro Tip: Always monitor your VM’s CPU, memory, and disk usage using Azure Monitor. This helps you adjust VM size to match performance and cost efficiency.

by Mark | May 12, 2023 | Azure, Azure Blobs, Cloud Storage
Best Practices and Use Cases
Introduction
Are you storing your data in the cloud? If yes, then you must be aware of the various security challenges that come with it.
One of the biggest concerns in cloud computing is securing data from unauthorized access. However, with Azure Storage Private Endpoints, Microsoft has introduced a solution that can help organizations secure their data in the cloud.
Brief overview of Azure Storage Private Endpoints
So what exactly are Azure Storage Private Endpoints? Simply put, private endpoints provide secure access to a specific service over a virtual network. With private endpoints, you can connect to your Azure Storage account from within your virtual network without needing to expose your data over the public internet.
Azure Storage Private Endpoints allows customers to create a private IP address for their storage accounts and map it directly to their virtual networks. This helps customers keep their sensitive data within their network perimeter and enables them to restrict access only to necessary resources.
Importance of securing data in the cloud
Securing data has always been a top priority for any organization. The rise of cloud computing has only increased this concern, as more and more sensitive information is being stored in the cloud.
A single security breach can cause irreparable damage not only to an organization’s reputation but also financially. With traditional methods of securing information proving inadequate for cloud-based environments, new solutions like Azure Storage Private Endpoints have become essential for businesses seeking comprehensive security measures against cyber threats.
We will explore how Azure Storage Private Endpoints offer organizations much-needed protection when storing sensitive information in the public cloud environment. Now let’s dive deeper into what makes these endpoints so valuable and how they work together with Azure Storage accounts.
What are Azure Storage Private Endpoints?
Azure Storage is one of the most popular cloud storage services. However, the public endpoint of Azure Storage is accessible over the internet. Any user who has the connection string can connect to your storage account.
This makes it difficult to secure your data from unauthorized access. To solve this problem, Microsoft introduced a feature called “Private Endpoints” for Azure Storage.
Private endpoints enable you to securely access your storage account over an Azure Virtual Network (VNet). Essentially, you can now create an endpoint for your storage account that is accessible only within a specific VNet.
Definition and explanation of private endpoints
Private endpoints are a type of network interface that enables secure communication between resources within a VNet and Azure services such as Azure Storage. The endpoint provides a private IP address within the specified subnet in your VNet.
When you create a private endpoint for your storage account, it creates a secure tunnel between the VNets where the private endpoint is created and where the storage account resides. This tunnel enables traffic to flow securely between these two locations without exposing any traffic to the public internet.
How they work with Azure Storage
When you create a private endpoint for Azure Storage, requests from resources in the same VNet as the private endpoint automatically route through this new interface instead of using the public internet-facing endpoints. In other words, once you’ve established a connection via Private Endpoint, all traffic between resources on that VNet and your Azure Storage Accounts will stay entirely within that virtual network. One benefit of this approach is increased security because it removes any exposure to attacks on an otherwise publicly available service like accessing data stored in an open container or blob; all connections go directly through an encrypted tunnel maintained by Microsoft itself with no chance for exposure or exploitation by malicious third parties outside or inside customer environments (as long as those environments are properly secured).
Additionally, working with Azure Storage accounts using Private Endpoints is incredibly straightforward and transparent. The process is essentially the same as if you’re connecting to the public endpoints, except your traffic stays on your private network entirely.
Benefits of using Azure Storage Private Endpoints
Improved security and compliance
One of the most significant benefits of using Azure Storage Private Endpoints is improved security and compliance. Traditional storage accounts often rely on access keys or shared access signatures to control access to data, which can be vulnerable to attacks such as phishing or insecure connections. Private endpoints, on the other hand, use a private IP address within a virtual network to establish a secure connection between the storage account and clients.
Additionally, private endpoints allow for granular control over network traffic by allowing only authorized traffic from specific virtual networks or subnets. This level of control significantly reduces the risk of unauthorized access and ensures compliance with industry regulations such as HIPAA or PCI-DSS.
Reduced exposure to public internet
Another major advantage of using Azure Storage Private Endpoints is reduced exposure to the public internet. With traditional storage accounts, data is accessed through a public endpoint that exposes it to potential threats such as DDoS attacks or brute-force attacks on authentication credentials.
By using private endpoints, you can ensure that your data remains within your virtual network and never leaves your organization’s infrastructure. This approach significantly reduces the risks associated with exposing sensitive data to unknown entities on the internet.
Simplified network architecture
Azure Storage Private Endpoints also simplify your organization’s overall network architecture by reducing the need for complex firewall rules or VPN configurations. By allowing you to connect directly from your virtual network, private endpoints provide a more streamlined approach that eliminates many of the complexities associated with traditional networking solutions.
This simplification allows organizations to reduce overhead costs in managing their networking infrastructure while providing enhanced security measures designed specifically for Azure Storage accounts. Additionally, since private endpoints can be deployed across multiple regions around the world without requiring any additional infrastructure configuration, they are an ideal solution for global organizations looking for an efficient and secure way to access their data.
Setting up Azure Storage Private Endpoints
Step-by-step guide on how to create a private endpoint for Azure Storage account
Setting up Azure Storage Private Endpoints is easy and straightforward. To create a private endpoint, you need to have an Azure subscription and an existing virtual network that the private endpoint will be attached to.
To create a private endpoint for an Azure Storage account, follow these steps:
1. Go to the Azure portal and select your storage account
2. Click on “Private endpoints” under settings
3. Click “Add” to create a new private endpoint
4. Select your virtual network and subnet
5. Choose the service you want to connect to (in this case, it would be Blob, File or Queue)
6. Select the storage account you want to connect to
7. Configure the DNS name label
8. Review and click “Create” Once completed, your private endpoint will be created.
Configuring virtual network rules and DNS settings
After creating your private endpoint, you need to configure virtual network rules and DNS settings. To configure virtual network rules:
1. Go back to your storage account in the Azure portal
2. Click on “Firewalls and virtual networks” under security + networking
3. Add or edit existing virtual network rules as needed
Virtual network rules allow traffic from specific IP addresses or ranges of IP addresses within your Virtual Network (VNet) to access the storage service over a specified set of ports.
To configure DNS settings:
1. Navigate back to the Private Endpoint blade in the portal.
2. Find your new storage account endpoint.
3. Copy its FQDN (fully qualified domain name). This will be used in place of traditional endpoints when accessing blobs/files/queues in this particular storage account.
4. Create CNAME records pointing from that FQDN to your actual storage account domain name. DNS settings allow clients within your Virtual Network to resolve the private endpoint’s FQDN to its corresponding private IP address.
Configuring virtual network rules and DNS settings is a crucial part of setting up Azure Storage Private Endpoints. By doing so, you are ensuring that only the necessary traffic can access your storage account privately.
Best practices for managing Azure Storage Private Endpoints
Limiting Access to Only Necessary Resources
When it comes to managing Azure Storage Private Endpoints, the first and most important step is to limit access only to necessary resources. This approach helps reduce the risk of unauthorized access, which can jeopardize the security of your data. As a best practice, you should only grant access permissions to users who need them for their specific tasks.
One effective way to limit access is by using role-based access control (RBAC). RBAC allows you to define roles and assign them specific permissions based on a user’s responsibilities within your organization.
With this approach, you can ensure that users have only the permissions they need and nothing more. Another way to limit access is by implementing network security groups (NSGs) within your virtual network.
NSGs are essentially firewall rules that allow or deny traffic based on IP addresses or port numbers. By creating firewall rules for your Azure Storage Private Endpoint, you can restrict traffic coming in and out of your network.
Monitoring and Logging Activities
The second best practice for managing Azure Storage Private Endpoints is monitoring and logging activities. Monitoring activities includes collecting metrics about resource usage, analyzing logs for suspicious behavior, and setting up alerts when certain conditions are met.
Azure provides several tools that help monitor activities within your storage account, including Azure Monitor and Log Analytics. These tools allow you to track network traffic patterns, monitor system performance in real-time, view logs related storage operations such as reads or writes performed against storage accounts.
Logging activities involves storing detailed information about events within the environment being monitored. Logging is essential in identifying potential security breaches or anomalies in system behavior patterns over time which may go unnoticed otherwise
Regularly Reviewing and Updating Configurations
reviewing configurations regularly will ensure that changes made do not expose the environment to vulnerabilities or noncompliance. Regularly reviewing and updating configurations is crucial for maintaining a secure environment and ensuring compliance with regulations.
It’s important to regularly review all configurations related to your storage account and endpoints, including virtual network rules, DNS settings, firewall rules, and permissions. By doing so, you can identify any misconfigurations that may be putting your organization at risk.
Additionally, it is important to keep up-to-date with the latest security best practices and changes in regulatory requirements which may impact how you configure Azure Storage Private Endpoints. limiting access rights while setting up Azure Storage Private Endpoints as well as monitoring all activities are key steps in keeping data safe from unauthorized users.
Regularly reviewing configurations is also essential for maintaining a secure environment over time. By following these best practices, you can take full advantage of Azure Storage’s powerful capabilities while keeping your data secure in the cloud.
Use Cases for Azure Storage Private Endpoints
Healthcare Industry: Securing Patient Data
The healthcare industry is one of the most heavily regulated industries in the world, with strict guidelines on how patient data can be stored and transmitted. Azure Storage Private Endpoints provide a secure way to store and access this sensitive data.
By creating a private endpoint for their Azure Storage account, healthcare providers can ensure that patient data remains protected from prying eyes. With the use of virtual network rules and DNS settings, healthcare organizations can limit access to only necessary resources, ensuring that patient data is kept confidential.
Additionally, with Azure Security Center, healthcare providers can be alerted to any suspicious activity or potential security threats. By monitoring and logging activities related to their Azure Storage Private Endpoint, healthcare providers can quickly identify and respond to any security issues that may arise.
Financial Industry: Protecting Sensitive Financial Information
The financial industry also deals with highly sensitive information such as financial transactions and personal identification information (PII). With the use of Azure Storage Private Endpoints, financial institutions can ensure that this data is secure while still being easily accessible by authorized personnel. By setting up a private endpoint for their Azure Storage account, financial institutions can reduce their exposure to the public internet and limit access only to those who need it.
This helps prevent unauthorized access or breaches of sensitive information. Azure Security Center also provides advanced threat protection capabilities that help detect, assess, and remediate potential security threats before they become major issues.
Government Agencies: Ensuring Compliance with Regulations
Government agencies also deal with sensitive information such as classified documents or personally identifiable information (PII). These agencies must comply with strict regulations regarding how this information is stored and accessed. With Azure Storage Private Endpoints, government agencies can ensure compliance with these regulations while still having easy access to their data.
By setting up private endpoints for their Azure Storage accounts, agencies can limit access to only authorized personnel and ensure that data remains secure. Azure Security Center also provides compliance assessments and recommendations based on industry standards such as HIPAA and PCI DSS, helping government agencies stay compliant with regulations.
Conclusion
Azure Storage Private Endpoints provide a secure way to access data stored in the cloud. By limiting public internet exposure and implementing private connectivity within your virtual network, you can reduce the risk of unauthorized access to your data.
Additionally, by using private endpoints, you can improve compliance with industry regulations and simplify network architecture. By following best practices for managing Azure Storage Private Endpoints such as regularly monitoring and reviewing configurations, limiting access to only necessary resources, and logging activities, you can ensure that your data remains secure.
Azure Storage Private Endpoints are especially useful in industries such as healthcare, finance and government where security and compliance are paramount. They enable these industries to securely store their sensitive information in the cloud while ensuring that it is only accessible by authorized personnel.
Overall, with Azure Storage Private Endpoints you can rest assured that your data is secure in the cloud. So go ahead and take advantage of this powerful feature to improve security and compliance for your organization!
Azure Storage Unlocked
Please fill out the form below to get our free Ebook "Azure Storage Unlocked" emailed to you
FREE DOWNLOAD

by Mark | May 11, 2023 | Azure Blobs, Azure FIles, Blob Storage, Storage Accounts
A brief overview of Azure Storage and its importance in cloud computing
Azure Storage is a cloud-based storage solution offered by Microsoft as part of the Azure suite of services. It is used for storing data objects such as blobs, files, tables, and queues.
Azure Storage offers high scalability and availability with an accessible pay-as-you-go model that makes it an ideal choice for businesses of all sizes. In today’s digital age, data has become the most valuable asset for any business.
With the exponential growth in data being generated every day, it has become imperative to have a robust storage solution that can handle large amounts of data while maintaining high levels of security and reliability. This is where Azure Storage comes in – it offers a highly scalable and secure storage solution that can be accessed from anywhere in the world with an internet connection.
Explanation of Shared Access Signatures (SAS) and their role in securing access to Azure Storage
Shared Access Signatures (SAS) are a powerful feature provided by Azure Storage that allows users to securely delegate access to specific resources stored within their storage account. SAS provides granular control over what actions can be performed on resources within the account, including read, write, delete operations on individual containers or even individual blobs. SAS tokens are cryptographically signed URLs that grant temporary access to specific resources within an account.
They provide secure access to resources without requiring users’ login credentials or exposing account keys directly. SAS can be used to delegate temporary access for different scenarios like sharing file downloads with customers or partners without giving them full control over an entire container or database table.
One important thing to note is that SAS tokens are time-limited – they have start times and expiry times associated with them. Once expired they cannot be reused again which helps prevent unauthorized access after their purpose has been served.
What are Shared Access Signatures?
Shared Access Signatures (SAS) is a mechanism provided by Azure Storage that enables users to grant limited and temporary access rights to a resource in their storage account. SAS is essentially a string of characters that contains information about the resource’s permissions, as well as other constraints such as the access start time and end time, and IP address restrictions.
The purpose of SAS is to enable secure sharing of data stored in your Azure Storage account without exposing your account keys or requiring you to create multiple sets of shared access keys. With SAS, you can give others controlled access to specific resources for a limited period with specific permissions, thereby reducing the risk of accidental or intentional data leaks.
Types of SAS: Service-level SAS and Container-level SAS
There are two types of Shared Access Signatures: service-level SAS and container-level SAS. A service-level SAS grants access to one or more storage services (e.g., Blob, Queue, Table) within a storage account while limiting which operations can be performed on those services. On the other hand, container-level SAS grants access only to specific containers within a single service (usually Blob) while also restricting what can be done with those containers.
A service-level SAS may be used for situations where you need to provide an external application with controlled read-only privileges on all blobs within an entire storage account or write privileges on blobs contained in specific storage containers. A container-level Shared Access Signature may be useful when you want users with different permissions over different containers inside one Blob Service.
Benefits of using Shared Access Signatures
Using Shared Access Signatures provides several benefits for accessing Azure Storage resources securely:
-
- Reduced Risk: with limited permissions enabled by shared access signatures, there’s less risk exposure from spreading around unsecured resources.
-
- Authorization Control: access to the resources is strictly controlled with sas since it can be assigned only to specific accounts or clients, with set time limits and other conditions.
-
- Flexibility: sas provides a flexible method of granting temporary permissions that can be set from one hour up to several years.
-
- No Need for Shared Keys: with sas, you don’t need to share your account keys with external clients and applications, thereby reducing the risk of unauthorized access to your storage account.
Overall, using Shared Access Signatures is a best practice for securing access to Azure Storage resources. It saves you time and effort as it’s much easier than generating multiple access keys.
How to Create a Shared Access Signature
Creating a Shared Access Signature (SAS) is a simple and straightforward process. With just a few clicks, you can create an SAS that grants specific access permissions to your Azure Storage resources for a limited period of time. This section provides you with step-by-step instructions on creating an SAS for Azure Storage.
Step-by-step guide on creating an SAS for Azure Storage
1. Open the Azure Portal and navigate to your storage account.
2. Select the specific container or blob that you want to grant access to.
3. Click on the “Shared access signature” button located in the toolbar at the top of the page.
4. Choose the desired options for your SAS, such as permissions, start time, expiry time, IP address restrictions, and more.
5. Click “Generate SAS and connection string”. 6. Copy the generated SAS token and use it in your application code.
Explanation of different parameters that can be set when creating an SAS
When creating an SAS, there are several parameters that can be configured based on your specific needs: – Permissions: You can specify read-only or read-write access for blob containers or individual blobs.
– Start Time: You can set a specific start time for when the SAS becomes effective.
– Expiry Time: You can set an expiration date and time after which the SAS will no longer be valid.
– IP Address Restrictions: You can limit access by specifying one or more IP addresses or ranges from which requests will be accepted. In addition to these basic parameters, there are also advanced options available such as specifying HTTP headers or setting up stored access policies.
Overall, creating an SAS is a powerful tool in securing your data stored in Azure Storage by providing temporary and limited access without compromising security standards. By following these simple steps and configuring relevant parameters based on your specific use-case, you can easily and securely grant access to your Azure Storage resources.
Best Practices for Using Shared Access Signatures
Tips on how to securely use SAS to protect your data in Azure Storage
Shared Access Signatures (SAS) are a powerful tool for securing access to your Azure Storage resources, but they must be used with care to avoid exposing sensitive data. One important tip is to always use HTTPS when creating or using SAS, as this protocol encrypts all communication between the client and the server.
It is also recommended that you do not store SAS tokens in unencrypted files or transmit them over insecure channels such as email. Another best practice when using SAS is to limit the scope of permissions granted by each token.
When creating a SAS, you can specify which specific actions (such as read, write, or delete) are allowed and which resources (such as containers or blobs) can be accessed. By carefully controlling these settings, you can ensure that only authorized users have access to your Azure Storage resources.
Recommendations on how to manage and revoke access when necessary
One of the main benefits of using SAS tokens is that they provide fine-grained control over who has access to your Azure Storage resources. However, this level of control also means that it is essential to have a clear management strategy in place for handling SAS tokens. One recommendation is to keep track of all active SAS tokens in use and regularly review them for any potential security risks.
This may involve periodically auditing token usage logs or reviewing alerts triggered by unusual activity patterns. Another best practice is to have procedures in place for revoking access when necessary.
For example, if an employee leaves your organization or a contractor’s project ends, their associated SAS tokens should be revoked immediately. This can be done either manually through the Azure portal or programmatically using APIs provided by Microsoft.
Discussion on the importance of monitoring access logs for security purposes
It is important to monitor access logs for any suspicious activity that may indicate a security breach. Azure Storage provides detailed logs that can be used to track all SAS token usage, including the time of access, the resource accessed, and the IP address of the client making the request. By reviewing these logs regularly, you can quickly identify any unauthorized access attempts or unusual activity patterns that may indicate a security threat.
You can also use advanced analytics tools like Azure Monitor and Azure Sentinel to detect and respond to security incidents in real-time. By following these best practices for using Shared Access Signatures in Azure Storage, you can help ensure the security and integrity of your data while still providing authorized users with flexible and controlled access.
Advanced Topics in Shared Access Signatures
Shared Access Policies
When managing large teams who require access to Azure Storage, maintaining the required security level can get complicated. Fortunately, Azure Storage has a feature that simplifies this process called shared access policies.
Shared access policies allow you to create sets of constraints that can be applied to a group of users or applications. When you assign a shared access policy, it applies the same set of permissions and constraints across all entities at once.
This helps you reduce administration overheads by avoiding the need to manage each individual entity separately. Using shared access policies in your Azure Storage environment improves security by granting specific types of permissions on specific items or containers so that users only have the necessary level of access needed for their role.
For example, read-only permission for analysts who need data but don’t require write-access is possible with shared access policies. The options available include creating read-only SAS tokens, which are valid for a specified period and cannot modify data.
Stored Access Policies
Stored Access Policies in Azure Storage are similar to shared access policies but function differently by attaching them directly to the container instead of assigning them individually. This makes it easier to manage and maintain SAS tokens over time since they’re now attached directly to containers rather than created through code.
Stored Access Policies grant permissions on objects within containers and provide further control over how users interact with your storage resources. You can use these stored policies when calling an API method like Get Blob or Get Container service operations providing more granular control over who has what kind of permission where.
Versioning Support
With versioning support enabled on your storage accounts, you can ensure your data is protected from accidental deletion or modification by retaining all previous versions. Each time a new version is created in response to an update request; the previous version remains available until you explicitly delete it.
Versioning support can be useful in case someone accidentally overwrites your data. You can restore a previous version of the object and avoid loss or corruption.
Versioning also prevents accidental deletion, which might occur because of errors made by users or malicious activity like hacking or ransomware attacks. Utilizing advanced features like shared access policies and stored access policies in Azure Storage can significantly enhance the security, performance, and usability of your applications.
Incorporating these features into your storage solutions provides a greater level of control over user permissions while reducing administrative overheads. Additionally, enabling versioning support ensures you never lose valuable data inadvertently overwritten or deleted.
Conclusion
Shared Access Signatures are an essential feature of Azure Storage that provides a secure and flexible way to grant access to your Azure Storage resources. With SAS, you can create fine-grained access control policies for your data and applications, without having to expose your account credentials or keys.
By using SAS, you can improve the security posture of your cloud applications while maintaining the scalability and performance benefits of distributed storage in the cloud. Throughout this article, we have explored the basics of Shared Access Signatures in Azure Storage.
We have learned about the different types of SAS available in Azure Storage, how to create them with various options and parameters, and best practices for using them securely. Furthermore, we have covered several advanced topics such as shared access policies, stored access policies, versioning support, and more.
As cloud computing continues to evolve rapidly over time, it is likely that new features and capabilities will be added to Azure Storage Shared Access Signatures. However, by understanding the fundamental concepts covered in this article – such as how to create a service-level or container-level SAS with specific permissions or restrictions – you should be well equipped to use SAS effectively in securing access to your valuable data stored in the cloud.
So go ahead and try out Shared Access Signatures in Azure Storage today! With their ability to provide granular control over resource access while reducing security risks associated with handling account keys or credentials directly within an application’s codebase; they are surely worth considering for any organization seeking improved security measures without sacrificing performance or simplicity.

by Mark | May 10, 2023 | Azure, Cloud Computing, HyperV, Microsoft HyperV, VMWare
In today’s world of virtualization, IT professionals are often faced with the challenging task of choosing the right platform for their organization’s needs. Azure, VMware, and Hyper-V are three major players in the virtualization market, each with its strengths and weaknesses. In this article, we will provide a comprehensive comparison of these three platforms and discuss how Carbon, a software solution, can assist you in migrating Azure virtual machines back to on-premise VMware or Hyper-V environments.
Overview of Azure, VMware, and Hyper-V
Azure
Azure is a cloud computing platform developed by Microsoft that provides a range of cloud services, including virtual machines (VMs), databases, and storage. It offers a wide variety of VM sizes and configurations, as well as a robust ecosystem of third-party tools and services.
VMware
VMware is a virtualization and cloud computing software provider that offers a comprehensive suite of products, including vSphere, vCenter, and vSAN. VMware’s solutions allow organizations to create and manage virtual machines on-premises or in the cloud.
Hyper-V
Hyper-V is a virtualization platform developed by Microsoft, available as a stand-alone product or as a feature of Windows Server. It allows users to create and manage virtual machines on Windows-based systems and is known for its ease of use and integration with other Microsoft products.
Key Comparison Factors
Scalability
Azure provides virtually limitless scalability, with the ability to add or remove resources on-demand. This makes it an attractive option for organizations that experience fluctuating workloads or require rapid expansion.
VMware and Hyper-V both offer on-premises scalability, although they may be constrained by the physical hardware limitations of your organization’s data center.
Performance
Performance is highly dependent on the specific workloads and configurations of each platform. Azure typically offers good performance for most use cases, although its performance may vary due to factors like network latency and resource contention.
VMware has a long history of delivering high-performance virtualization solutions, and its performance is often considered industry-leading.
Hyper-V’s performance is generally on par with VMware, although some users may find that specific workloads perform better on one platform over the other.
Security
All three platforms offer robust security features, such as encryption, network security, and access controls. Azure benefits from Microsoft’s extensive security investments, providing users with a secure and compliant cloud environment.
VMware and Hyper-V both offer strong security features, with VMware’s security built around its vSphere platform and Hyper-V leveraging its integration with Windows Server.
Cost
Azure’s pay-as-you-go model can be cost-effective for organizations with fluctuating workloads, but it may become expensive for long-term, consistent use. Additionally, data transfer and storage costs can add up over time.
VMware and Hyper-V have upfront licensing costs, and on-premises hardware and maintenance expenses should also be considered. However, these platforms can be more cost-effective for organizations with stable workloads and those who prefer to manage their infrastructure.
Management Tools
Azure offers a wide range of management tools, including the Azure Portal, Azure CLI, and Azure PowerShell, making it easy to manage and monitor your VMs.
VMware provides a comprehensive suite of management tools, such as vCenter, vSphere, and vRealize, which are well-regarded for their functionality and ease of use.
Hyper-V’s management tools include Hyper-V Manager, System Center Virtual Machine Manager, and Windows Admin Center, providing a seamless management experience for Windows users.
Differences and Similarities in Deployment Options
Azure
Being a cloud-based platform, Azure allows users to deploy VMs and other services in Microsoft’s data centers worldwide. This global reach ensures low latency and redundancy for applications and data. Additionally, Azure enables hybrid cloud scenarios, allowing users to leverage on-premises resources alongside cloud resources.
VMware
VMware primarily focuses on on-premises virtualization solutions, with its vSphere platform enabling users to create and manage VMs in their data centers. However, VMware has also ventured into the cloud market with VMware Cloud, which offers VMware-based cloud services in partnership with providers like AWS, Azure, and Google Cloud. This allows users to create hybrid or multi-cloud environments using familiar VMware tools and interfaces.
Hyper-V
Hyper-V is primarily an on-premises virtualization solution, offering VM management on Windows Server or Windows 10 systems. While it does not have a native cloud offering, Microsoft offers Azure Stack HCI, a hybrid cloud solution that leverages Hyper-V and other Windows Server technologies to create a consistent experience across on-premises and Azure environments.
Differences and Similarities in Networking
Azure
Azure offers a robust suite of networking services and features, including Virtual Networks (VNETs), Load Balancers, and Application Gateways. Users can create isolated and secure virtual networks, manage traffic with load balancing, and implement advanced application delivery and security features.
VMware
VMware’s networking capabilities are built around its vSphere Distributed Switch (VDS) technology, which allows users to create and manage virtual networks, segment traffic, and enforce security policies across multiple hosts. VMware NSX, a network virtualization platform, extends these capabilities by providing advanced features like micro-segmentation, load balancing, and VPN.
Hyper-V
Hyper-V’s networking features are closely integrated with Windows Server, allowing users to create virtual switches, configure VLANs, and implement Quality of Service (QoS) policies. While its capabilities may not be as extensive as VMware’s NSX or Azure’s networking services, Hyper-V provides a solid foundation for virtualized network management.
Differences and Similarities in Storage
Azure
Azure offers a wide range of storage options, including Azure Blob Storage, Azure Files, and Azure Disk Storage. Users can choose from various performance tiers and redundancy levels to meet their specific requirements. Additionally, Azure provides advanced features like geo-replication, backup, and disaster recovery.
VMware
VMware’s storage capabilities are centered around its vSAN technology, which enables users to create software-defined storage pools using local storage resources on vSphere hosts. This allows for high-performance, scalable, and resilient storage for VMs. VMware also supports traditional storage technologies like SAN, NAS, and iSCSI.
Hyper-V
Hyper-V storage is based on Windows Server storage technologies, such as Storage Spaces and SMB file shares. Users can create flexible and resilient storage pools using local or shared storage resources. Hyper-V also supports features like storage live migration and storage replica for increased flexibility and reliability.
Differences and Similarities in High Availability and Disaster Recovery
Azure
Azure offers native high availability and disaster recovery features, such as Availability Sets, Availability Zones, and Azure Site Recovery. These services ensure that VMs remain operational during planned or unplanned outages and provide geo-redundancy for critical applications and data.
VMware
VMware’s high availability features are built around its vSphere High Availability (HA) and vSphere Fault Tolerance (FT) technologies, which automatically restart VMs on other hosts in case of a hardware failure or maintain continuous availability for mission-critical applications. For disaster recovery, VMware offers Site Recovery Manager (SRM), a solution that automates the recovery process and provides orchestrated failover and failback capabilities.
Hyper-V
Hyper-V leverages Windows Server Failover Clustering (WSFC) for high availability, allowing users to create clusters of Hyper-V hosts that automatically handle VM failover during host outages. For disaster recovery, Hyper-V offers Hyper-V Replica, a feature that asynchronously replicates VMs to a secondary site, enabling users to recover their VMs in case of a disaster.
Differences and Similarities in Backup and Recovery
Azure
Azure offers native backup and recovery services, such as Azure Backup and Azure Site Recovery, which allow users to protect and restore their VMs and data in case of failure or disaster. These services provide features like incremental backups, geo-replication, and automated recovery processes, ensuring data integrity and minimal downtime.
VMware
VMware’s backup and recovery capabilities are primarily delivered through third-party solutions, such as Veeam, Rubrik, and Commvault, which provide integration with vSphere for VM backup and recovery. These solutions offer features like image-level backups, deduplication, and instant recovery, ensuring reliable and efficient data protection.
Hyper-V
Hyper-V supports backup and recovery through its integration with Windows Server Backup, a built-in feature of Windows Server that allows users to create and manage backups of VMs and data. Additionally, third-party backup solutions like Veeam and Altaro provide advanced features and integrations for Hyper-V environments.
Differences and Similarities in Licensing and Pricing
Azure
Azure follows a pay-as-you-go pricing model, where users are billed based on the resources they consume. This model can be cost-effective for organizations with fluctuating workloads, but it may become expensive for long-term, consistent use. Additionally, data transfer and storage costs can add up over time.
VMware
VMware’s licensing model is based on per-CPU licensing for its vSphere product line, with additional costs for features like vSAN and NSX. Organizations must also consider the costs of on-premises hardware and maintenance when evaluating VMware’s pricing. However, VMware can be more cost-effective for organizations with stable workloads and those who prefer to manage their infrastructure.
Hyper-V
Hyper-V is included with Windows Server, which is licensed per-core, making it a cost-effective option for organizations already using Windows Server. However, additional costs for Windows Server Datacenter Edition or System Center may apply for organizations requiring advanced features.
Differences and Similarities in Ecosystem and Integration
Azure
Azure’s ecosystem is vast, with a wide variety of third-party tools and services available for users to choose from. Additionally, Azure has strong integration with other Microsoft products, such as Office 365, Dynamics 365, and Power BI, making it an attractive option for organizations invested in the Microsoft ecosystem.
VMware
VMware’s ecosystem is also extensive, with numerous third-party tools and services available for users to enhance their virtualization experience. VMware’s solutions integrate with many popular products like backup software, monitoring tools, and security solutions, providing users with a seamless and flexible experience.
Hyper-V
Hyper-V’s ecosystem is smaller compared to Azure and VMware, but it benefits from strong integration with other Microsoft products and services. This can be advantageous for organizations already using Windows Server, System Center, or other Microsoft solutions.
Differences and Similarities in Performance and Scalability
Azure
Azure offers a wide range of VM sizes and performance tiers to accommodate various workloads, from small development environments to large-scale enterprise applications. Azure’s autoscaling capabilities enable users to automatically scale their VMs based on demand, ensuring optimal performance and cost efficiency. Additionally, Azure’s global infrastructure provides the ability to deploy applications and services in multiple regions for increased redundancy and performance.
VMware
VMware’s vSphere platform is known for its performance and scalability, enabling users to create and manage large-scale virtual environments with ease. VMware supports advanced features like Distributed Resource Scheduler (DRS), which automatically balances VM workloads across hosts to optimize performance. Additionally, VMware’s VMotion technology enables live migration of VMs between hosts with no downtime, ensuring seamless scalability and resource optimization.
Hyper-V
Hyper-V offers solid performance and scalability for Windows-based virtual environments. While it may not provide as many advanced features as VMware’s vSphere platform, Hyper-V supports live migration and dynamic memory allocation for VMs, which helps optimize resource usage and performance. Hyper-V’s integration with Windows Server also allows users to leverage features like Storage Spaces Direct and Scale-Out File Server for increased storage scalability.
Differences and Similarities in Security Features
Azure
Azure provides a robust set of security features to protect VMs and data. These features include Azure Security Center, which offers centralized security management and monitoring, and Azure Private Link, which allows users to access Azure services over a private connection. Additionally, Azure supports encryption for data at rest and in transit, network security features like Network Security Groups and Firewalls, and access controls based on Azure Active Directory and role-based access control (RBAC).
VMware
VMware’s security features are built around its vSphere platform, with technologies like vSphere Trust Authority and vSphere Secure Boot ensuring the integrity of the virtual environment. VMware NSX provides advanced network security features like micro-segmentation, distributed firewalls, and intrusion detection and prevention. Additionally, VMware supports encryption for data at rest and in transit, as well as integration with third-party security solutions.
Hyper-V
Hyper-V leverages its integration with Windows Server to provide security features like Shielded VMs, which protect VMs from unauthorized access and tampering, and Host Guardian Service, which ensures the integrity of Hyper-V hosts. Hyper-V also supports encryption for data at rest and in transit, network security features like virtual network isolation and port ACLs, and access controls based on Windows Server Active Directory and RBAC.
Differences and Similarities in Container Support
Azure
Azure offers strong support for container technologies, including Azure Kubernetes Service (AKS), which enables users to easily deploy and manage Kubernetes clusters in Azure. Additionally, Azure supports container instances and Azure Container Registry for storing and managing container images.
VMware
VMware’s container support is built around its vSphere Integrated Containers (VIC) technology, which enables users to run containers alongside VMs on vSphere hosts. VMware also offers Tanzu Kubernetes Grid, a Kubernetes runtime that allows users to deploy and manage Kubernetes clusters across vSphere and public clouds.
Hyper-V
Hyper-V supports running containers through its integration with Windows Server and Windows 10, which includes support for both Windows and Linux containers. Additionally, Microsoft offers Azure Kubernetes Service on Azure Stack HCI, a hybrid cloud solution that enables users to deploy and manage Kubernetes clusters in their Hyper-V environments.
Carbon: The Migration Solution
For organizations looking to migrate their Azure VMs back to on-premises VMware or Hyper-V environments, Carbon offers a robust solution that streamlines the process and ensures a smooth transition.
Migrating Azure VMs to VMware
With Carbon, users can easily migrate Azure VMs to VMware using a step-by-step process that simplifies the migration and minimizes downtime.
Migrating Azure VMs to Hyper-V
Carbon also supports migrating Azure VMs to Hyper-V environments, providing a flexible solution for organizations using either VMware or Hyper-V.
Carbon’s Key Features
Real-time Monitoring
Carbon offers real-time monitoring during the migration process, allowing users to keep track of their VMs and ensure a successful migration.
Customizable Settings
Carbon’s customizable settings allow users to tailor the migration process to their specific needs, providing greater control and flexibility.
Email Notifications
With Carbon’s email notifications, users are kept informed of the migration progress, ensuring that any issues can be addressed promptly.
Conclusion
In summary, Azure, VMware, and Hyper-V each offer unique benefits and drawbacks, making it essential for organizations to carefully evaluate their specific needs before selecting a virtualization platform. For those looking to migrate their Azure VMs back to on-premises VMware or Hyper-V environments, Carbon provides a robust, user-friendly solution that simplifies the process and ensures a smooth transition.
FAQs
- Can I migrate from Azure to both VMware and Hyper-V using Carbon?
Yes, Carbon supports migrating Azure VMs to both VMware and Hyper-V environments.
- How does Carbon ensure a smooth migration process?
Carbon offers real-time monitoring, customizable settings, and email notifications to keep users informed and in control throughout the migration process.
- Is Carbon suitable for users with limited technical skills?
Yes, Carbon’s step-by-step process and intuitive interface make it accessible for users of all skill levels.
- What factors should I consider when choosing between Azure, VMware, and Hyper-V?
Factors to consider include scalability, performance, security, cost, and available management tools.
- Do Azure, VMware, and Hyper-V all offer similar security features?
Yes, all three platforms provide robust security features, such as encryption, network security, and access controls.

by Mark | May 9, 2023 | Azure, Azure Blobs, Blob Storage, Storage Accounts
Brief Overview of Azure Storage Account Failover
Azure Storage Account Failover is a critical feature offered by Microsoft Azure that provides users with the ability to switch to an alternative instance of their storage account in case of a disaster or an outage. In simple terms, it is the act of transferring control of Azure storage account operations from one region to another, ensuring business continuity and disaster recovery. This means that if a user’s primary storage account becomes unavailable due to a natural disaster, human error, or any other reason, they can quickly failover to their secondary storage account without experiencing any disruption in services.
One advantage of Azure Storage Account failover is that it is fast and automated. With automatic failover configured for a user’s primary storage account, Microsoft can detect and respond to service disruptions automatically.
This feature ensures minimal downtime for your applications and data access. It is essential for businesses running mission-critical applications on Microsoft Azure that require high availability.
Importance of Failover in Ensuring Business Continuity and Disaster Recovery
The importance of failover in ensuring business continuity and disaster recovery cannot be overstated. A well-architected architecture should provide the highest level of uptime possible while still being able to recover promptly from unexpected failures/disasters. The goal should be maximum availability with minimal downtime.
A failure can occur at any time without warning – ranging from hardware failures to natural disasters like floods or fires. Businesses must have contingency plans in place because they are dependent on their IT systems’ availability at all times.
By having an Azure Storage Account Failover strategy in place, companies can mitigate the risk associated with sudden outages that could lead to significant data loss or prolonged downtime. Furthermore, regulatory compliance requires businesses operating within certain industries — such as finance and healthcare –to implement robust business continuity plans (BCPs) that include backup and disaster recovery procedures.
An Azure Storage Account Failover strategy can help businesses meet these requirements. In the next section, we will discuss what an Azure Storage Account Failover is and how it works to ensure business continuity and disaster recovery.
Understanding Azure Storage Account Failover
What is a Storage Account Failover?
Azure Storage Account Failover is a feature that allows you to switch your storage account from one data center to another in case of an outage or maintenance event. The failover process involves redirecting all requests and operations from the primary data center to the secondary data center, ensuring minimal disruption of service. Azure Storage Account Failover is critical for maintaining business continuity and disaster recovery in the cloud.
How does it work?
Azure Storage Account Failover works by creating a secondary copy of your storage account in an alternate region. This copy is kept in sync with the primary copy using asynchronous replication.
In case of an outage or maintenance event, Azure will automatically initiate failover by promoting the secondary copy as the new primary and redirecting all traffic to it. Once the primary region is back online, Azure will synchronize any changes made during the failover period and promote it back as the primary.
Types of failovers (automatic and manual)
There are two types of failovers supported by Azure Storage Account: automatic and manual. Automatic failovers are initiated automatically by Azure when there is an unplanned outage or disaster impacting your storage account’s availability. During automatic failover, all requests are redirected from the primary region to the secondary region within minutes, ensuring no data loss occurs.
Manual failovers are initiated manually by you when you need to perform planned maintenance or updates on your storage account’s primary region. During a manual failover, you can specify whether to wait for confirmation before initiating or immediately perform a forced takeover.
Factors to consider before initiating a failover
Before initiating a failover for your storage account, there are several factors you should consider. First, ensure that your secondary region is at least 400 miles away from your primary region to minimize the risk of both regions being impacted by the same disaster.
Additionally, consider the availability of your storage account’s services during failover and how it may impact your customers. Ensure you have adequate bandwidth and resources to support a failover event without impacting other critical operations.
Configuring Azure Storage Account Failover
Step-by-step guide on how to configure failover for your storage account
Configuring Azure Storage Account Failover is a crucial step in ensuring business continuity and disaster recovery. Here is a step-by-step guide on how to configure failover for your storage account:
1. Navigate to the resource group containing the storage account you want to configure for failover.
2. Open the storage account’s overview page by selecting it from the list of resources.
3. In the left-hand menu, select “Failover”.
4. Select “Enable” to enable failover for that storage account.
5. Select target region(s) where you want data replication. 6. Review and confirm the settings
Best practices for configuring failover
To ensure successful failover, here are some best practices that should be followed when configuring Azure Storage Account Failovers:
1. Ensure that your primary region is designated as “Primary”.
2. Choose secondary regions that are geographically separated from your primary region.
3. Use identical configurations in all regions, including network configurations, access keys, and firewall rules.
4. Configure monitoring services such as Azure Monitor or Log Analytics to receive alerts during an outage or when a failover event occurs.
Common mistakes to avoid when setting up failover
There are several common mistakes that can occur when setting up Azure Storage Account Failovers which could lead to ineffective disaster recovery solutions or further damage during outages:
1. Not having enough available secondary regions – it’s important not only to designate adequate secondary regions but also check their availability before committing them in case they’re already experiencing some problems themselves
2. Failing to keep configurations identical across all regions – failing to do this could cause unexpected behavior during a fail-over event which could lead into further complications
3. Not testing failover – test your storage account’s failover capabilities before an actual disaster occurs to ensure it works effectively. By following these best practices and avoiding common mistakes when configuring Azure Storage Account Failovers, you can ensure that your business stays operational even during a disaster.
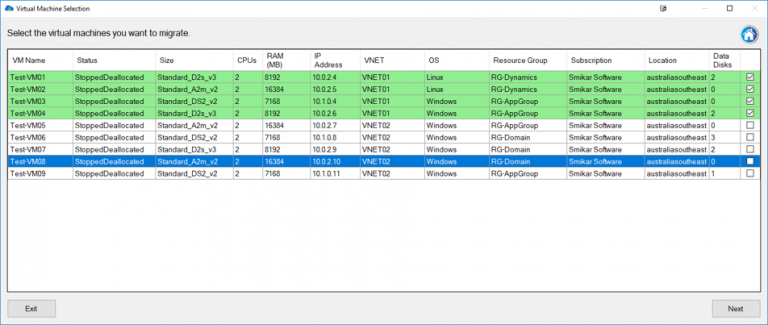
Testing Azure Storage Account Failover
The Importance of Testing Failover Before an Actual Disaster Occurs
Testing the failover capabilities of your Azure Storage Account is a crucial step in ensuring that your business operations will continue to run smoothly in the event of a disaster. By testing your failover plan, you can identify any potential issues or gaps in your plan and take steps to address them before they become a real problem. Testing also allows you to measure the time it takes for your system to recover, and gives you confidence that your systems will work as expected.
Additionally, testing can help you ensure that all key personnel and stakeholders are aware of their roles and responsibilities during a failover event. This includes not only technical teams who are responsible for executing the failover process, but also business teams who may need to communicate with customers or other stakeholders during a disruption.
How To Test Your Storage Account’s Failover Capabilities
To test your storage account’s failover capabilities, there are several steps you can follow:
1. Create a test environment: Set up a separate environment that simulates what might happen during an actual disaster. This could include creating mock data or running tests on separate virtual machines.
2. Initiate Failover: Once the test environment is set up, initiate the failover process manually or automatically depending on what type of failover you have configured.
3. Monitor Performance: During the failover event, monitor key performance metrics such as recovery time and network connectivity to identify any problems or bottlenecks.
4. Perform Post-Failover Tests: Once the system has been restored, perform post-failover tests on critical applications to ensure that everything is functioning as expected. 5. Analyze Results: Analyze the results of your tests and use them to improve your overall disaster recovery plan
Tips for Successful Testing
To ensure that your testing is successful, consider the following tips:
1. Test Regularly: Regularly test your failover plan to identify and address issues before they become a problem.
2. Involve All Stakeholders: Involve all key stakeholders in the testing process, including business teams and technical teams.
3. Document Results: Document the results of your tests and use them to continuously improve your disaster recovery plan.
4. Don’t Rely on Testing Alone: While testing is crucial, it’s important to remember that it’s just one part of an overall disaster recovery strategy. Make sure you have a comprehensive plan in place that includes other elements such as data backups and redundant systems.
Monitoring Azure Storage Account Failovers
Monitoring your Azure Storage Account Failover is critical to ensure that you can take the proper actions in case of an outage. Monitoring allows you to detect issues as they arise and track the performance of your failover solution. There are several tools available in Azure for monitoring your storage account failovers, including:
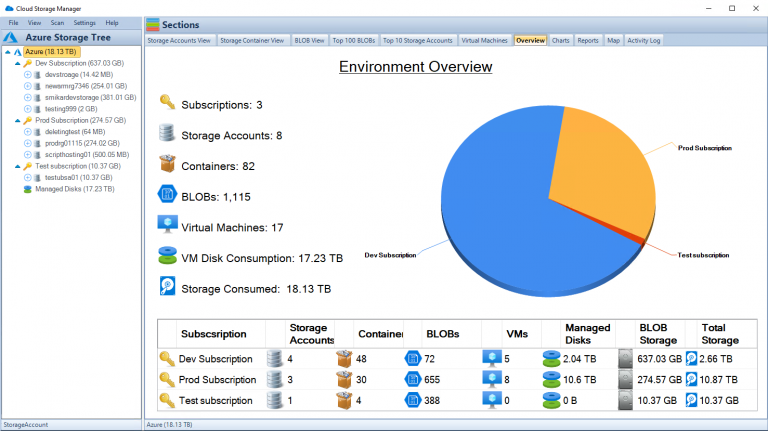
Tools available for monitoring storage account failovers
Azure Monitor: This tool provides a unified view of the performance and health of all your Azure resources, including your storage accounts. You can configure alerts to notify you when specific metrics cross thresholds or when certain events occur, such as a failover event. Log Analytics: This tool enables you to collect and analyze data from multiple sources in real-time.
You can use it to monitor the status of your storage accounts, including their availability and performance during a failover event. Other tools that you might consider include Application Insights, which helps you monitor the availability and performance of web applications hosted on Azure; and Network Watcher, which provides network diagnostic and visualization tools for detecting issues that could impact a storage account’s failover capability. Additionally, use Cloud Storage Manager to monitor your Azure consumption.
Key metrics to monitor during a failover event
When it comes to monitoring your storage account’s failover capability, there are several key metrics that you should keep an eye on. These include:
Fault Domain: This metric indicates whether the primary or secondary location is currently active (i.e., which fault domain is currently serving requests).
Data Latency: this metric measures how long it takes for data to replicate from primary location to secondary location.
RPO (Recovery Point Objective): this metric indicates the point in time to which you can recover data in case of a failover event.
RTO (Recovery Time Objective): this metric indicates the amount of time it takes for your storage account to become available again after a failover event has occurred.
By monitoring these metrics, you can quickly detect issues and take appropriate actions to ensure that your storage account remains available and performs optimally during a failover event.
Troubleshooting Azure Storage Account Failovers
Common issues that can occur during a storage account failover
Common issues that can occur during a storage account failover
During a storage account failover, there are several issues that may arise. One common issue is data loss or corruption. This can happen if the replication between primary and secondary regions has not been properly configured or if there is a delay in replication before the failover occurs.
Another issue that may occur is an inability to access the storage account. This could be due to network connectivity issues or if there are incorrect settings in the DNS records.
Another common issue that can arise during a storage account failover is performance degradation. This can occur due to an increase in latency when accessing data from the secondary region, which may cause slower read/write speeds and longer response times.
How to troubleshoot these issues
To troubleshoot data loss or corruption issues during a storage account failover, it’s important to ensure that replication settings are properly configured and up-to-date before initiating a failover. Additionally, it’s important to monitor replication status throughout the process of failing over and afterwards.
To troubleshoot connectivity issues, first check your DNS records to ensure they are correctly configured for both regions. Also, check network connectivity between regions using tools like ping or traceroute.
If you’re experiencing performance degradation during a storage account failover, consider scaling up your secondary region resources temporarily until the primary region is fully restored. Ensure your resources have been optimized for optimal performance by monitoring metrics like CPU usage and IOPS.
While Azure Storage Account Failovers are designed to provide business continuity and disaster recovery capabilities, they do come with their own set of potential issues. By proactively monitoring and troubleshooting any potential problems before initiating a failover event you’ll be better prepared should any complications arise.
Recap on Azure Storage Account Failovers
In today’s digital age, data is an essential asset for businesses. With cloud computing becoming the norm, businesses need to ensure that their data is secure and accessible at all times to ensure business continuity.
Azure Storage Account Failover provides an automatic and manual option for protecting your data in the event of a disaster. Proper configuration, testing, monitoring, and troubleshooting provide confident assurance that your business will continue running smoothly even in the face of disaster.
This comprehensive guide has covered all aspects of Azure Storage Account Failover. By understanding what it is and how it works, configuring it properly, testing its capabilities regularly, monitoring for any issues during failover events and troubleshooting problems that may arise during those events, you can rest assured that your critical data will be protected.
Creating this guide on Azure Storage Account Failovers was necessary as this feature has become increasingly important to businesses given the amount of critical data being stored in cloud repositories. While it may seem daunting at first with proper planning and execution Azure Storage Account Failover provides a seamless way to protect your organization’s critical information from disasters or outages ensuring minimal downtime thus meeting the needs of today’s fast-paced digital world.