Setting Permissions for Documents and Libraries
Ensuring Data Security
| Key Takeaway | Description |
|---|---|
| Permission Levels | SharePoint offers default permission levels: Full Control, Edit, Contribute, Read, and View Only, each designed for different roles and access needs within an organization. |
| Custom Permission Levels | Administrators can create custom permission levels by combining SharePoint’s granular permissions to meet specific organizational requirements. |
| Group-based Permissions Management | Assigning permissions to groups rather than individuals simplifies management and ensures consistent access control based on roles. |
| Principle of Least Privilege | Applying the least privilege principle by giving users the minimum access necessary reduces security risks and protects sensitive information. |
| Integration with Active Directory | SharePoint integrates with Active Directory for streamlined user and group management, enhancing permissions management across the organization’s IT ecosystem. |
| Advanced Security Measures | Beyond basic permissions, implementing encryption and two-factor authentication (2FA) adds layers of security, protecting data from unauthorized access even if credentials are compromised. |
| Monitoring and Auditing | Regular monitoring and auditing of permissions and access patterns are essential for identifying potential security gaps and ensuring compliance with data protection regulations. |
In the digital age, where data flows as freely as water, securing our digital documents and libraries has become a paramount concern. As we navigate through an ever-expanding digital universe, the line between accessibility and security is often blurred. Striking the perfect balance requires not just technical know-how but a strategic mindset. Setting appropriate permissions is not just a safeguarding tactic; it’s a critical component of modern data management. This guide delves into the essence of data security through the lens of permissions management, offering insights, strategies, and actionable advice to secure your digital assets effectively.
The Importance of Data Security
In today’s interconnected world, the sanctity of our digital information is under constant threat. Data security is not just about protecting information from unauthorized access; it’s about ensuring that the right people have the right access at the right time. The stakes are incredibly high. A single breach can lead to catastrophic losses, both financial and reputational. Understanding the risks associated with inadequate data protection is the first step towards crafting a robust security strategy. This section will explore the critical role of permissions in mitigating these risks and safeguarding digital assets against both external and internal threats.
Data breaches are not just a threat to large corporations; they pose a significant risk to organizations of all sizes. The fallout from these incidents can be devastating, affecting every aspect of an organization. Financial repercussions, legal challenges, and the erosion of customer trust are just the tip of the iceberg. The importance of data security in today’s digital landscape cannot be overstated. It is the foundation upon which the trust between organizations and their stakeholders is built. As we delve deeper into the nuances of data security, we’ll uncover the pivotal role permissions play in creating a secure digital environment.
SharePoint Storage Explorer
Gain insights in to your SharePoint Online Storage Consumption
Download our completely FREE TOOL
Send download link to:
Understanding the Risks
The digital realm is fraught with risks. From sophisticated cyber-attacks to simple human error, the avenues through which data can be compromised are vast and varied. Unsecured documents and libraries are akin to open doors for cybercriminals, inviting unauthorized access and potential data breaches. These vulnerabilities can lead to a range of adverse outcomes, including data theft, espionage, and the introduction of malware or ransomware into an organization’s systems.
Understanding these risks is crucial for developing an effective data security strategy. This section will dissect the various threats to digital documents and libraries, highlighting the importance of a proactive and comprehensive approach to data protection. Through real-world examples and expert insights, we’ll explore how permissions play a critical role in mitigating these risks, providing a layer of security that is both flexible and robust.
The Impact of Data Breaches
The consequences of a data breach can be far-reaching and long-lasting. Beyond the immediate financial losses, which can be significant, the intangible costs of a breach often have a more profound impact. The damage to an organization’s reputation, the loss of customer trust, and the potential legal ramifications can have lasting effects on its future prospects.
SharePoint RBAC Model
The SharePoint Role-Based Access Control (RBAC) model is an approach to managing users’ permissions that focuses on roles within an organization rather than on individual users. This model simplifies the management of permissions by assigning access rights based on the roles users have within the organization, rather than assigning permissions to each user individually. SharePoint’s implementation of RBAC is designed to make the process of granting, adjusting, and revoking access to resources both efficient and secure. Let’s delve into the key components and how SharePoint applies the RBAC model
Mastering SharePoint Online
Please fill out the form below to get our free Ebook "Mastering SharePoint Online" emailed to you
Send download link to:
Key Components of SharePoint RBAC
- Roles: In SharePoint, roles represent sets of permissions that are designed to correspond to the tasks users need to perform within the site or organization. These roles could be predefined by SharePoint, such as “Reader,” “Contributor,” and “Full Control,” or they can be custom-defined by administrators to cater to specific organizational needs.
- Permission Levels: Each role in SharePoint is associated with a specific permission level, which is a collection of permissions that define the access level for that role. Permission levels are granular and can be customized to include any combination of SharePoint’s extensive list of permissions, from viewing items and editing items to managing lists and overriding checkouts.
- Groups: SharePoint groups are collections of users that are treated as a single entity. Administrators assign roles to groups instead of individual users. By managing access at the group level, SharePoint simplifies the process of permissions management. When a user’s role within an organization changes, administrators can simply move the user to a different group, automatically updating their access rights according to their new role.
How SharePoint Applies the RBAC Model
- Simplifying Permissions Management: By assigning users to groups based on their roles and then assigning roles to resources, SharePoint allows for a streamlined approach to managing access. This model significantly reduces the complexity and time involved in permissions management, especially in large organizations or sites with a high number of users.
- Enhancing Security: RBAC helps in minimizing the risk of unauthorized access by ensuring that users only have the permissions necessary to perform their roles. This principle of least privilege is a fundamental security best practice, and SharePoint’s RBAC model facilitates its implementation.
- Improving Compliance: SharePoint’s RBAC model supports compliance with internal policies and external regulations by providing a clear framework for access control. The model makes it easier to audit who has access to what information, which is crucial for meeting compliance requirements.
- Flexibility and Scalability: SharePoint’s RBAC model is both flexible and scalable, accommodating the changing needs of organizations. New roles can be created, and permission levels adjusted as the organization evolves. This adaptability is essential for growing businesses and evolving security landscapes.
- User and Group Management: SharePoint integrates with Active Directory (AD) for user and group management, allowing for seamless synchronization of user roles between SharePoint and other systems. This integration further simplifies the management of user access across an organization’s entire IT ecosystem.
Practical Application
In practice, an administrator might set up a SharePoint site for project collaboration. Instead of individually assigning permissions to each user, the administrator creates groups such as “Project Managers,” “Team Members,” and “Viewers,” each with different roles and permission levels. Users are then added to these groups based on their role in the project, automatically granting them the appropriate level of access.
The SharePoint RBAC model offers a powerful and efficient way to manage permissions, ensuring that access control is both secure and aligned with organizational roles. By leveraging roles, permission levels, and groups, SharePoint administrators can effectively control access to resources, streamline the permissions management process, and uphold security and compliance standards.
SharePoint Storage Explorer
Gain insights in to your SharePoint Online Storage Consumption
Download our completely FREE TOOL
Send download link to:
Advanced Security Measures
Beyond the basic assignment of permissions, safeguarding sensitive information requires the implementation of advanced security measures. These measures serve as additional layers of defense, enhancing the protection of documents and libraries against sophisticated threats.
Encryption
Encryption transforms readable data into a coded format that can only be accessed with the correct decryption key, providing a strong layer of protection for sensitive information. In the context of document and library permissions, encryption ensures that even if unauthorized access is somehow gained, the data remains unintelligible and secure.
- Implementation: Effective encryption strategies involve selecting the right encryption standards (such as AES-256 for documents) and ensuring encryption is applied both in transit and at rest. This section will guide readers through the process of implementing encryption, including key management practices and compliance with regulatory requirements.
- Impact on Permissions: While encryption primarily protects the contents of documents and libraries, it also influences how permissions are managed. For instance, access to decryption keys must be tightly controlled, aligning with the permissions set for each document or library.
Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring two forms of identification from users before granting access to documents or libraries. This significantly reduces the risk of unauthorized access due to compromised credentials.
- Application in Permissions Management: Integrating 2FA into permissions management involves setting up a system where access to certain levels of permissions requires additional authentication steps. This might include access to highly sensitive documents or admin-level permissions.
- Benefits and Challenges: This section will explore the benefits of implementing 2FA, such as reduced risk of data breaches and enhanced trust among stakeholders, alongside the challenges, including potential user friction and the need for user education.
Mastering SharePoint Online
Please fill out the form below to get our free Ebook "Mastering SharePoint Online" emailed to you
Send download link to:
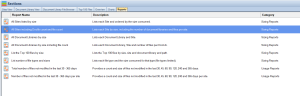
SharePoint Permissions
In SharePoint, permissions are fundamental to managing access to content and resources, ensuring that users have appropriate levels of access based on their roles and responsibilities. SharePoint organizes these permissions into various levels and groups to facilitate granular control over site access, document libraries, and individual items. Understanding the types of permissions is crucial for effective SharePoint administration. Here’s an overview of the key permission types in SharePoint:
Basic Permission Levels
SharePoint defines a set of default permission levels that correspond to common roles within an organization. Each permission level is a collection of individual permissions designed to suit particular tasks or responsibilities. Here are some of the default permission levels:
- Full Control: Users with this level have complete control over all site content, settings, and permissions. They can add, edit, delete, and change permissions on all items. Typically, this is reserved for administrators.
- Edit: This level allows users to add, edit, and delete lists; view, add, update, and delete list items and documents. It’s designed for users who manage content but do not need to manage site settings.
- Contribute: Contributors can view, add, update, and delete list items and documents. This level is suitable for team members who need to collaborate on documents or list items but don’t need to change the site structure.
- Read: Users with Read permissions can view pages and items in existing lists and document libraries. They can also download documents. This level is ideal for users who need access to information but do not contribute content.
- View Only: Similar to Read, but users cannot download documents from the library. This is useful for sharing sensitive information that should not be copied.
Special Permission Levels
In addition to the basic permission levels, SharePoint allows for the creation of custom permission levels to accommodate specific needs. Administrators can mix and match from a comprehensive list of individual permissions to create new levels. Some special permissions include:
- Manage Permissions: Create and change permission levels on the web site and assign permissions to users and groups.
- Approve Items: Approve or reject list items or documents in lists with content approval enabled.
- Manage Web Site: Create and delete sites, list templates, and libraries, including managing site themes and borders.
- Add and Customize Pages: Add, change, or delete HTML pages or web part pages, and edit the website using a SharePoint Designer and web browser.
Individual Permissions
Individual permissions are the building blocks of permission levels. SharePoint provides a wide range of these granular permissions, allowing administrators to precisely control access to site features and content. These permissions include actions like viewing items, opening items, editing personal user information, managing lists, and more.
Mastering SharePoint Online
Please fill out the form below to get our free Ebook "Mastering SharePoint Online" emailed to you
Send download link to:
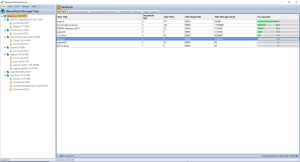
How Permissions are Applied
Permissions in SharePoint can be assigned directly to individual users, but it’s generally recommended to assign permissions to SharePoint groups. Groups organize users with similar access needs, simplifying the management of access rights. Permissions can also be inherited from parent objects (like sites or libraries), or they can be set uniquely for more granular control.
When setting up permissions, administrators should carefully consider the principle of least privilege—providing users with the minimum level of access necessary to perform their roles. This approach minimizes security risks and helps protect sensitive information.
Understanding the types and levels of permissions in SharePoint is critical for maintaining a secure and well-organized digital workspace. By judiciously assigning permissions, administrators can ensure that users have the access they need to collaborate effectively while safeguarding the organization’s data.
Monitoring and Auditing
Maintaining a secure document and library environment requires ongoing vigilance. Regular monitoring and auditing practices are essential for identifying potential security gaps and ensuring that permission settings are consistently applied and updated according to organizational policies and compliance requirements.
Regular Reviews
Conducting regular reviews of permissions settings helps ensure that access rights remain aligned with users’ current roles and responsibilities. This section will cover strategies for scheduling and conducting these reviews, including which metrics to monitor and how to address discrepancies.
- Tools for Monitoring: Leveraging tools that provide real-time monitoring and alerting for unusual access patterns or permission changes can help organizations respond quickly to potential security threats. Recommendations for effective tools and practices will be discussed.
Compliance Standards
Compliance with data protection regulations (such as GDPR, HIPAA, etc.) often requires specific permissions settings and auditing practices. This part of the guide will delve into how organizations can ensure their permissions management practices meet these regulatory requirements, highlighting key considerations for maintaining compliance.
- Auditing Practices: Effective auditing practices involve tracking and documenting changes to permissions settings, access attempts, and data handling activities. This section will offer guidance on setting up an auditing framework that supports both security and compliance objectives.
Common Challenges and Solutions
Despite best efforts, organizations may encounter challenges in managing permissions and ensuring data security. This section will address some of the most common challenges, such as managing permissions at scale, dealing with legacy systems, and training users on security practices.
- Scalability: As organizations grow, managing permissions for an increasing number of documents and users can become complex. Solutions such as role-based access control (RBAC) and attribute-based access control (ABAC) can offer more scalable approaches.
- Legacy Systems: Integrating advanced permissions management and security measures with legacy systems can be particularly challenging. Strategies for modernizing these systems or implementing interim measures will be explored.
- User Training: Ensuring that all users understand the importance of data security and how to comply with permissions policies is crucial. This section will provide tips for effective security awareness training and fostering a culture of security.
SharePoint Storage Explorer
Gain insights in to your SharePoint Online Storage Consumption
Download our completely FREE TOOL
Send download link to:
Mastering SharePoint Online
Please fill out the form below to get our free Ebook "Mastering SharePoint Online" emailed to you
Send download link to: