Introduction
In today’s digital era, the cloud has revolutionized the way we store, process, and transmit data, offering scalability, efficiency, and flexibility. As we continue to transition towards this cloud-first approach, the importance of robust cloud security can’t be overstated. This article will provide ten essential tips for ensuring the safety and security of your data in the cloud.
Understanding the Basics of Cloud Security
Before we delve into the security tips, it’s important to understand what cloud security entails. In essence, cloud security is a broad set of policies, technologies, and controls deployed to protect data, applications, and infrastructure associated with cloud computing. It helps shield your cloud services from threats such as data breaches, cyberattacks, and system downtime.
A critical aspect of cloud security is understanding the shared responsibility model. This model underscores that cloud security is a collective responsibility between the cloud service provider and the user. While the provider ensures the security of the cloud, users are responsible for securing their data within the cloud.
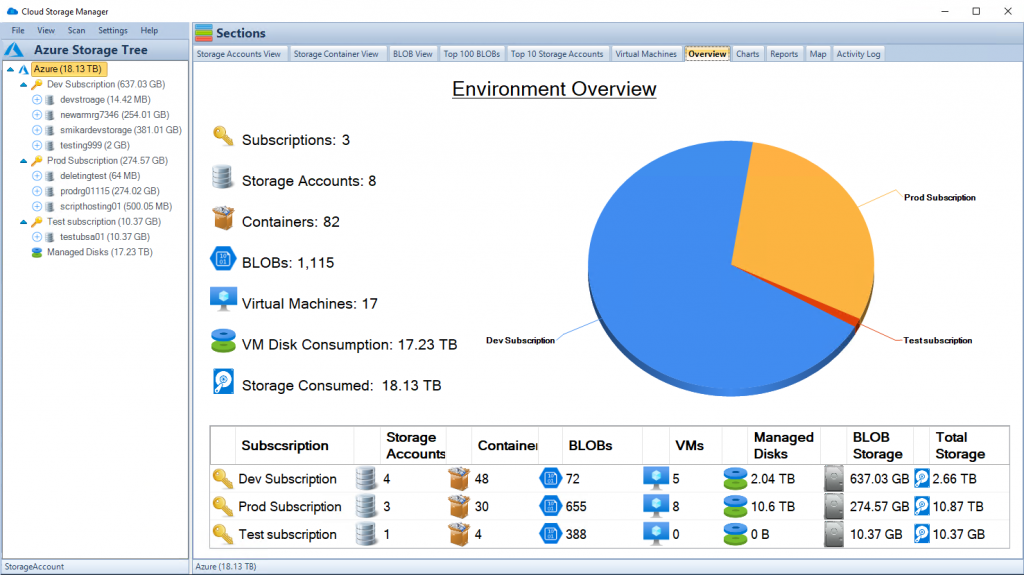
The Ten Essential Security Tips for Cloud Services
Now that we have a fundamental understanding of cloud security, let’s explore the ten vital tips to ensure optimal security of your cloud services.
Strong Authentication Measures
Implement Multi-factor Authentication (MFA): MFA adds an extra layer of protection to your accounts by requiring users to provide at least two forms of identification before accessing cloud services. This typically involves something you know (password), something you have (smartphone), and something you are (biometrics). Even if a cybercriminal gains your password, MFA makes it significantly harder for them to gain unauthorized access.
Enforce Strong Password Policies: Passwords are your first line of defense against unauthorized access. Implementing policies like mandatory periodic password changes, using a mix of alphanumeric and special characters, and avoiding easily guessable passwords can go a long way in securing your cloud environment.
Regular Updates and Patches
Keep Your Cloud Services Updated: Just like your local software, cloud services also receive updates to fix security vulnerabilities. Regular updates can prevent cybercriminals from exploiting these vulnerabilities.
Implement Regular Patching: Alongside updates, patches are crucial for fixing specific security vulnerabilities and are often released between major updates. They should be implemented as soon as possible to prevent potential breaches.
Encryption of Data
Encrypt Your Data: Encryption transforms data into an unreadable format, decipherable only with a decryption key. Encrypting data at rest and in transit protects it from unauthorized access, even if it falls into the wrong hands.
Role-Based Access Control (RBAC)
Implement RBAC: RBAC restricts network access based on roles within your organization, ensuring that individuals can only access the data necessary for their roles. This minimizes the risk of unauthorized data access and reduces potential damage in case of a breach.
Regular Auditing and Monitoring
Perform Regular Audits: Regular auditing helps you stay aware of your cloud environment’s state. It helps identify any potential vulnerabilities, suspicious activities, or unauthorized changes, allowing you to mitigate risks before they cause harm.
Use Cloud Monitoring Tools: These tools provide real-time monitoring and alerting of suspicious activities. They can help you promptly detect and respond to potential security incidents, minimizing their impact.
Secure Cloud Architecture
Adopt a Secure Cloud Architecture: An architecture that integrates security considerations at its core provides a solid foundation for protecting your data. This might include measures like network segmentation, firewalls, intrusion detection/prevention systems, and zero trust models.
Backup and Disaster Recovery Plan
Have a Backup and Disaster Recovery Plan: In the face of a disaster or data loss, having a backup and recovery plan can mean the difference between a minor hiccup and a major catastrophe. Regularly back up your data and ensure you have a recovery plan to restore services promptly.
Secure API Integrations
Secure Your APIs: APIs are often used to integrate different cloud services, but if not secured properly, they can create vulnerabilities. Implementing security measures like token-based authentication, encryption, and rate limiting can protect your APIs.
Vendor Security Assessments
Perform Vendor Security Assessments: Before choosing a cloud service provider, assess their security measures. This includes their security certifications, data encryption practices, privacy policies, and more. Make sure they align with your security needs.
Employee Training and Awareness
Train Your Employees: Your security measures are only as strong as your weakest link. Regular training sessions can keep your employees aware of the latest cybersecurity threats and best practices, reducing the chances of human error leading to a security breach.
Conclusion
Adopting robust security measures for your cloud services is crucial in today’s digital landscape. As we’ve discussed, strong authentication, regular updates and patching, encryption, role-based access control, regular audits, secure cloud architecture, backup plans, secure APIs, vendor assessments, and employee training form the ten pillars of cloud security.
Remember that cloud security is an ongoing journey, not a one-time activity. It requires consistent effort and proactive measures. Given the ever-evolving nature of cyber threats, staying abreast of new vulnerabilities and adopting the latest security measures will ensure that your cloud services remain secure and your data protected. The benefits of a secure cloud far outweigh the investment, providing peace of mind and securing the trust of your customers in the long run.
Cloud Security FAQs
- Q: What is cloud security? A: Cloud security is a set of policies, controls, procedures, and technologies that work together to protect cloud-based systems, data, and infrastructure. It covers everything from encrypting data to making access decisions to setting firewalls.
- Q: What is a shared responsibility model in cloud security? A: The shared responsibility model is a framework that outlines who is responsible for what in the context of cloud security. It delineates the security responsibilities of the cloud provider and the customer to ensure all aspects of security are covered.
- Q: Why is multi-factor authentication important? A: Multi-factor authentication (MFA) adds an additional layer of security that makes it harder for unauthorized users to access your data. Even if your password is compromised, MFA requires another form of verification, keeping your data safer.
- Q: What is role-based access control (RBAC)? A: Role-Based Access Control (RBAC) is a principle that restricts network access based on an individual’s role within an organization. It ensures that individuals can only access the data necessary for their job, minimizing potential damage in case of a breach.
- Q: Why is it important to have a backup and disaster recovery plan? A: A backup and disaster recovery plan is essential for restoring data and applications in the event of a disaster, system failure, or cyberattack. It ensures that you can quickly recover and continue your operations with minimal downtime.
- Q: What is encryption, and why is it important in cloud security? A: Encryption is the process of converting data into a code to prevent unauthorized access. It’s important in cloud security because it protects data at rest and in transit, reducing the risk of it being intercepted or accessed by unauthorized entities.
- Q: How does regular auditing and monitoring help in cloud security? A: Regular auditing and monitoring provide insight into your cloud environment’s state. It helps identify any potential vulnerabilities, suspicious activities, or unauthorized changes, enabling you to address risks before they escalate into serious security incidents.
- Q: Why is secure API integration essential for cloud security? A: APIs are often used to integrate different cloud services. If not secured properly, they can create security vulnerabilities. Therefore, secure API integration is essential to protect your data and maintain the integrity of your cloud services.
- Q: What should I look for in a cloud service provider’s security measures? A: You should look for a cloud service provider with a robust security framework, including data encryption practices, secure API integrations, adherence to industry-standard security certifications, regular audits, a disaster recovery plan, and privacy policies that align with your security needs.
- Q: Why is employee training important for cloud security? A: Employees often are the first line of defense against cyber threats. Regular training can make them aware of the latest cyber threats, how to identify suspicious activities, and follow best security practices, reducing the risk of human-induced security incidents.

