
by Mark | Mar 7, 2016 | SCCM
System Centre Configuration Manager (SCCM) Auto Deployment Rule Error 0x87d20415
Are you experiencing Auto Deployment Rule Error 0x87d20415 in SCCM? Don’t worry, it’s a common issue related to SCCM’s hard-coded limit on the number of updates that can be downloaded by an Automatic Deployment Rule. To fix it, check your Auto Deployment Rules in SCCM’s Software Library and investigate the issue by examining the ruleengine.log file. Once you’ve identified the problem, set the Date Revised or Released to the last month, go to your Automatic Deployment Rule, and choose Run Now. After completing this process, check the ruleengine.log file again to ensure that updates download without any issues. By following these steps, you can easily overcome Auto Deployment Rule Error 0x87d20415 in SCCM and ensure that your Automatic Deployment Rules run smoothly. For more helpful solutions to SCCM deployment issues, be sure to check out our other articles.
Check your Auto Deployment Rules
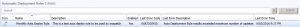
When you notice that updates haven’t been downloading as intended, one of the first things to check is your Auto Deployment Rules. Go to the Software Library in SCCM and select Automatic Deployment Rules. In the main window, you should be able to see the error code and why your Auto Deployment Rule hasn’t run. The error in this case is 0x87d20415.
Go to Software Library and choose Automatic Deployment Rules
I
In the main window you should be able to see the error code and why your Auto Deployment Rule hasnt run. The error in this example is 0x87d20415, as per the below image.
The issue is that SCCM has a hard coded limit on the number of updates (1000) that can be downloaded by an Automatic Deployment Rule. The best place to start to investigate that this is the case, is to check the ruleengine.log, located install directory – Microsoft Configuration Manager – Logs – ruleengine.log.
Looking at the file with cmtrace, you should be able to easily identify that this is in fact the issue. (Issue highlighted in yellow)
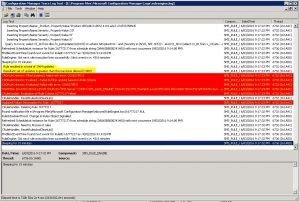
You can see that the ADR has hit the 1000 update limits as highlighted in yellow above.
To overcome this issue, you need to set the date revised or released to the last month. This way, SCCM will only check for updates released in this period. To do this, right click on your Automatic Deployment Rule and click properties. Go to the Software Updates tab, and choose Date Released or Revised, and set this for a more suitable time frame (1 month should suffice, but this does depend on your Update deployment schedule)
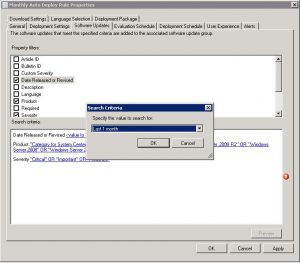
Once you have changed this range, go to your Automatic Deployment Rule, and choose Run Now.
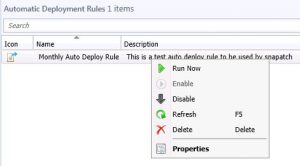
Once this has been completed, check the Ruleengine.log once again, and you should hopefully see that the updates are now in fact downloading and the dreaded error, Auto Deployment Rule Error 0x87d20415 has disappeared.
In conclusion, fixing Auto Deployment Rule Error 0x87d20415 in SCCM can be quite simple. By following the steps outlined above, you can resolve this issue and ensure that your Automatic Deployment Rules run smoothly without encountering this error. If you encounter any other SCCM deployment issues, be sure to check out our other articles for solutions.
by Mark | Dec 9, 2015 | Patch Management, Patch Releases, SCCM
Microsoft’s December 2015 Patch Releases
The following twelve Patch Tuesday updates / patches have been released by Microsoft for the December 2015 Update deployment.
MS15-112 – Critical
Cumulative Security Update for Internet Explorer (3104517)
This security update resolves vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS15-125 – Critical
Cumulative Security Update for Microsoft Edge (3116184)
This security update resolves vulnerabilities in Microsoft Edge. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Microsoft Edge. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS15-126 – Critical
Cumulative Security Update for JScript and VBScript to Address Remote Code Execution (3116178)
This security update resolves vulnerabilities in the VBScript scripting engine in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if an attacker hosts a specially crafted website that is designed to exploit the vulnerabilities through Internet Explorer (or leverages a compromised website or a website that accepts or hosts user-provided content or advertisements) and then convinces a user to view the website. An attacker could also embed an ActiveX control marked “safe for initialization” in an application or Microsoft Office document that uses the Internet Explorer rendering engine to direct the user to the specially crafted website.
MS15-127 – Critical
Security Update for Microsoft Windows DNS to Address Remote Code Execution (3100465)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if an attacker sends specially crafted requests to a DNS server.
MS15-128 – Critical
Security Update for Microsoft Graphics Component to Address Remote Code Execution (3104503)
This security update resolves vulnerabilities in Microsoft Windows, .NET Framework, Microsoft Office, Skype for Business, Microsoft Lync, and Silverlight. The vulnerabilities could allow remote code execution if a user opens a specially crafted document or visits a webpage that contains specially crafted embedded fonts.
MS15-129 – Critical
Security Update for Silverlight to Address Remote Code Execution (3106614)
This security update resolves vulnerabilities in Microsoft Silverlight. The most severe of the vulnerabilities could allow remote code execution if Microsoft Silverlight incorrectly handles certain open and close requests that could result in read- and write-access violations. To exploit the vulnerability, an attacker could host a website that contains a specially crafted Silverlight application and then convince a user to visit a compromised website. The attacker could also take advantage of websites containing specially crafted content, including those that accept or host user-provided content or advertisements.
MS15-130 – Critical
Security Update for Microsoft Uniscribe to Address Remote Code Execution (3108670)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted document or visits an untrusted webpage that contains specially crafted fonts.
MS15-131 – Critical
Security Update for Microsoft Office to Address Remote Code Execution (3116111)
This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS15-132 – Important
Security Update for Microsoft Windows to Address Remote Code Execution (3116162)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow remote code execution if an attacker accesses a local system and runs a specially crafted application.
MS15-133 – Important
Security Update for Windows PGM to Address Elevation of Privilege (3116130)
This security update resolves a vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to a target system and runs a specially crafted application that, by way of a race condition, results in references to memory locations that have already been freed. Microsoft Message Queuing (MSMQ) must be installed and the Windows Pragmatic General Multicast (PGM) protocol specifically enabled for a system to be vulnerable. MSMQ is not present in default configurations and, if it is installed, the PGM protocol is available but disabled by default.
MS15-134 – Important
Security Update for Windows Media Center to Address Remote Code Execution (3108669)
This security update resolves vulnerabilities in Microsoft Windows. The more severe of the vulnerabilities could allow remote code execution if Windows Media Center opens a specially crafted Media Center link (.mcl) file that references malicious code. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS15-135 – Important
Security Update for Windows Kernel-Mode Drivers to Address Elevation of Privilege (3119075)
This security update resolves vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to a target system and runs a specially crafted application.





