A Comprehensive Guide to sharing with external parties in SharePoint Online
In today’s interconnected business world, external collaboration is essential. SharePoint Online provides the flexibility to share documents with external partners, clients, and vendors, but this can also expose organizations to data security risks. Securing external sharing while ensuring smooth collaboration is key to maintaining trust and protecting sensitive information. Here’s how you can achieve that balance.

Best Practices for Secure External Sharing in SharePoint Online
SharePoint Online enables powerful collaboration with partners, vendors, and clients—but it must be done securely. This guide outlines seven critical best practices that will help you safeguard sensitive information while enabling productivity.
1. Define Organization-Wide Sharing Policies
Set boundaries on what can be shared, who can share it, and how sharing happens across departments. Limit permissions for sensitive areas like HR while enabling flexibility for teams like marketing.
- Restrict sharing to authenticated users only
- Use site-level permissions for sensitive departments
2. Enforce MFA and Conditional Access
Multi-Factor Authentication (MFA) and Conditional Access provide layered security. Use them to restrict access based on location, device type, or sign-in behavior.
- Require MFA for all external collaborators
- Use conditional rules to block access from unmanaged devices
3. Use Sensitivity Labels and Microsoft Information Protection
Protect sensitive data using Microsoft Information Protection (MIP) tools. Sensitivity labels classify content and apply security policies automatically.
- Auto-encrypt confidential documents
- Limit forwarding and editing via access controls
4. Use Specific People Sharing & Set Expiration Dates
Avoid using “Anyone with the link.” Instead, choose “Specific people” to control exactly who can access files. Always set link expiration dates for time-bound access.
5. Monitor and Audit External Sharing
Use SharePoint audit logs and alerts to monitor unusual file-sharing behavior. Investigate mass downloads or access from unrecognized locations.
- Enable alerting for risky sharing events
- Conduct monthly audits of external access logs
6. Leverage Azure AD B2B for Guest Management
Use Azure AD B2B to manage external users as guests. Apply the same policies you do for internal users—MFA, device restrictions, and more.
- Secure onboarding/offboarding of external users
- Centralize control and automate access provisioning
7. Use Access Reviews and Guest Expiration Policies
Review guest access quarterly and revoke accounts that are no longer needed. Set expiration timelines for guest access to automate offboarding.
Decision Matrix
| Scenario | Best Practice |
|---|---|
| Temporary vendor access | Specific people link + expiration + MFA |
| Long-term partner collaboration | Azure B2B + sensitivity labels + access reviews |
| One-time file delivery | Specific people link + expiration |
Conclusion
Secure external sharing in SharePoint Online is achievable with a layered, policy-driven approach. By using built-in Microsoft tools like MFA, Conditional Access, and Sensitivity Labels—plus managing guest access with Azure AD—you can keep data safe while supporting collaboration.
Adopt these seven steps to build a SharePoint environment that’s both collaborative and secure.
FAQs: Secure External Sharing in SharePoint Online
1. Can I disable external sharing entirely?
Yes, SharePoint Online allows you to disable external sharing at both the tenant and site level.
2. Is using ‘Anyone with the link’ ever safe?
This option is not recommended for sensitive content. Use “Specific People” links with expiration dates for better control.
3. What happens when a guest user’s access expires?
The guest account is automatically removed based on the expiration policy you configure.
4. How often should I run access reviews?
Quarterly access reviews are recommended to ensure external access remains current and justified.
5. Can I track who accessed a shared document?
Yes, SharePoint provides detailed audit logs that track document access and sharing activity.
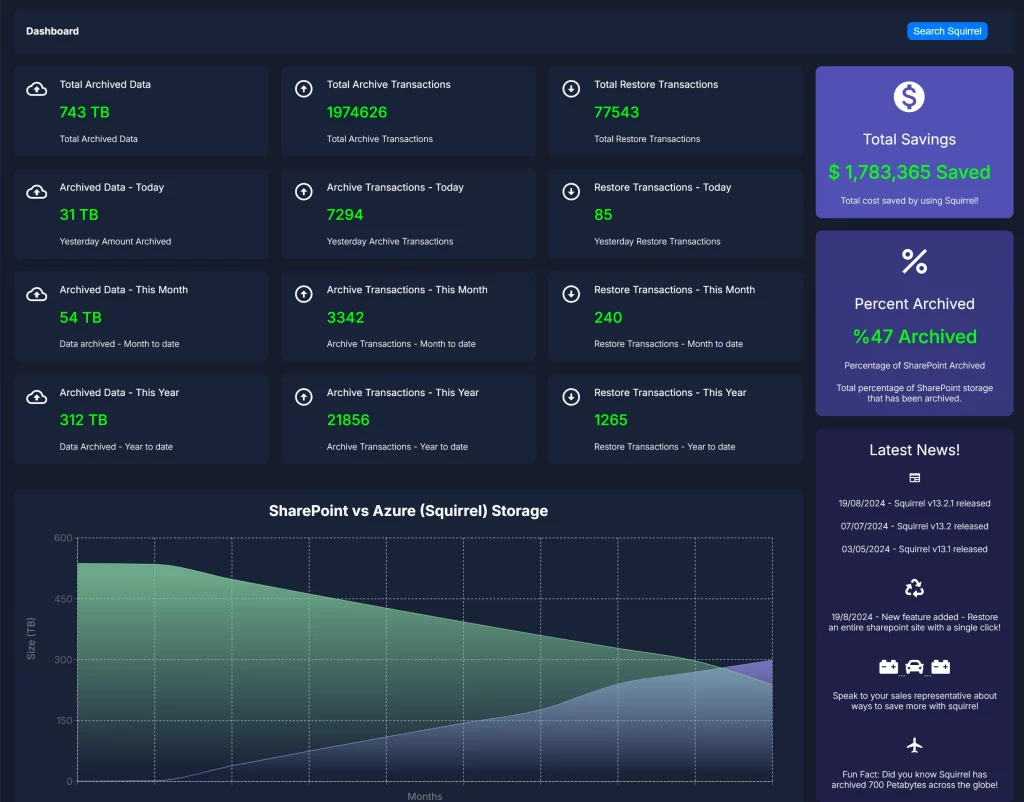
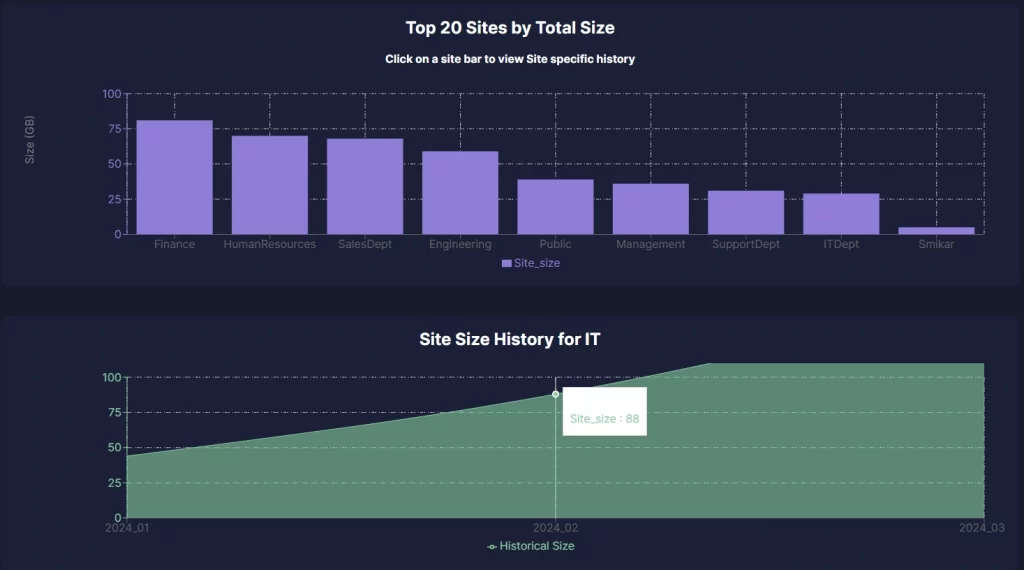
Managing Your SharePoint Online Costs Doesn’t Have to Be Hard.
With Squirrel, you can reduce your SharePoint Online Storage cost without reducing deleting a file. Intelligent Archiving for SharePoint made easy with Squirrel.